A secure separation kernel can bring together multiple legacy systems on a single multicore platform
BY STUART FISHER
LynuxWorks, San José, CA
http://www.lynuxworks.com
A typical embedded system contains a number of software components that provide the basic functionality. These can generally be abstracted as the operating system, middleware, and custom application(s). The operating system provides the control and system functions to abstract the hardware layer from the system software above, while providing key functionality such as memory management, software isolation, and timing. The middleware, when used, provides system functions that exist at a higher layer than that of hardware control and may include features such as message passing, network functions, and system monitoring.
A typical legacy embedded system often has just one CPU with a single core executing from a single physical memory space. There may only be simple user I/O interfaces or many communication channels to other embedded devices. The system is a single black box or a number of networked black boxes.
Increasing security
Security in such systems generally takes the form of physically restricting the interfaces to and from the device and “sandboxing” these devices such that they perform the function without intervention of other systems. An example of this would be a legacy mobile phone and PDA two distinct devices, each with a very specific function. The mobile phone would provide the communication, and the PDA would contain sensitive user data. The two devices would be physically separated and so an intrinsic security exists. When migrating these types of devices into today’s “one-box multiple-function” world, it is clear that more security is required in the operating system and middleware layers.
Another trend in the marketplace is to consolidate legacy systems running on various hardware onto a single multicore platform. A software solution is needed that can provide a foundation for multiple guest operating systems running on a single device while maintaining the physical separation characteristics of two disconnected systems. The solution to this comes from a separation kernel a small layer of software running directly on the hardware.
A separation kernel, such as LynxSecure from LynuxWorks, allows developers to bring together multiple legacy systems on a single multicore hardware platform using hardware assisted virtualization techniques such as Intel’s VTx and VTd technology. LynxSecure was developed primarily as a military grade solution for high-end information assurance programs. Separation kernels exploit the features of a hypervisor and enable architectures consisting of many subjects functioning at differing security levels.
Kernels must meet standards
The kernels are developed to meet the needs of the Common Criteria framework and in particular achieve an Evaluation Assurance Level (EAL) of 7+, the highest level available. This standard stringently dictates the policies and requirements for security certification of a system, including features as auditing, denial of service mechanisms, secure message channels, information flow, and policy management.
Traditionally this level of software security was only available in sophisticated and expensive government projects. Using such products makes its possible to leverage the years of effort in software separation development and bring military grade security to legacy commercial devices.
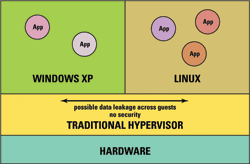
Fig. 1. A traditional hypervisor provides little security and isolation between guest operating systems.The use of hardware-assisted software virtualization is a very well understood way of consolidating multiple systems on a single hardware platform, but it is also an elegant way to add new functionality to a legacy system without redesign. Figure 1 shows the architecture of a system using a traditional hypervisor. The issue with this type of implementation is that virtualization alone does not imply separation so the intrinsic security is lost from when the two systems were physically separated.
This type of software virtualization cannot be used to add security functionality with any level of assurance. A separation kernel can provide both certified separation of subjects or guest operating system and the features of a traditional hypervisor.
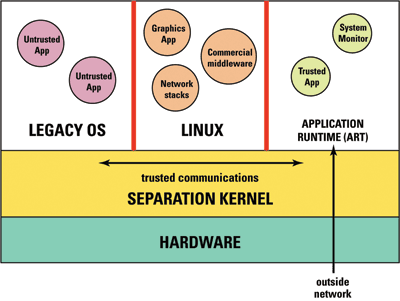
Fig. 2. A separation kernel and hypervisor allows the secure operation of multiple OSes on a single piece of hardware.
Putting things together.
Figure 2 shows the architecture of a legacy system that is hosted as a guest operating system on a separation kernel. In this example we explore the use of two additional guest operating systems providing functionality that the legacy system does not contain. The Linux guest may be providing a full networking stack while the application runtime (ART) is providing a secure connection to the outside world. The ART in this example is small software layer classed as a trusted guest and is deemed via certification to be privileged enough to act as a go-between from the unsecure legacy system and the outside network. It is typically acting as a secure gateway.
The guest operating systems occupy different CPU cores so that performance is maximized while giving an extra level of separation. An area where this type of architecture is gaining significant momentum is when the legacy system is based on Windows with a new requirement for additional functionality from another device or a new feature.
An example here could be a medical device and a patient-monitoring system on two separate devices. The patient record database could be based on Windows and the medical device on a real-time deterministic OS such as LynxOS. Here it is critical that the Windows system has separation from the measurement device and vice versa for intrinsic security. Using a software separation kernel would be an ideal solution to such a problem.
Consolidated systems require communication with each other, and the implications of adding such messaging channels need to be considered. When these systems are consolidated, there is a requirement on all communication channels to be certain malicious software cannot discover other guests by manipulating these channels. A separation kernel must implement secure channels to prevent covert channels being established between guests. This type of implementation should be an intrinsic certifiable function in any quality separation kernel. ■
.
Advertisement
Learn more about LynuxWorks





