Digital security: A new generation of government ID chips
The security controller industry finds itself at a crossroads, a situation that demands radical rethinking
BY DR. PETER LAACKMANN and MARCUS JANKE
Infineon Technologies AG
www.infineon.com
Security microcontrollers are widely used in national ID cards and passports. Their integration is spreading daily, rendering the handling of such documents increasingly secure and convenient. Security, on the other hand, does not exist by default in a semiconductor chip.
Microcontrollers for electronic ID documents exchange information with the outside world using a contactless connection, but they differ significantly from typical RFID tagging devices such as those used in logistic applications. Chips in an electronic passport, for example, contain a central processing unit, administer account policy, and can even take autonomous actions against attacks.
Security devices in the field are facing progressively more threats, which in turn grow more dangerous. Meanwhile, electronic passports and national identification card applications demand increased security lifetimes. In light of existing and anticipated attack scenarios, conventional security concepts begin to crumble. The security controller industry finds itself at a crossroads, a situation that demands radical rethinking.
Classes of attacks
Three attack classes, which are used against hardware, and are well known. They have been constant for decades, and are expected to remain constant for many years to come.
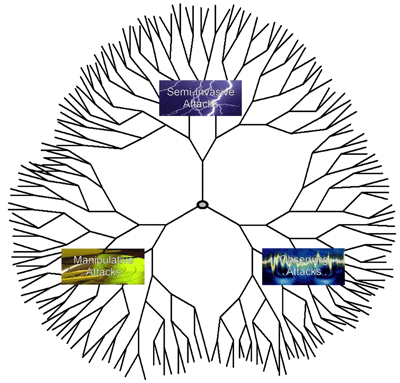
Fig. 1: The “attack tree” — thousands of attack scenarios originate from three attack groups.
Manipulative attacks
If an attacker performs manipulations of the hardware itself, such attacks are called “manipulative attacks.” This include the use of microscopic needles set on signal lines, over which secret information from the heart of a chip is extracted. Other manipulative attacks imply the modification of a chip’s structure and circuit by performing microsurgery on the silicon, typically by using a focused-ion-beam (FIB) workstation.
Recent manipulative attacks include the use of atomic force microscopy needles, which are only a few atoms wide and therefore compatible with even the latest, smallest technology.
Observing attacks
Observing attacks have existed for many decades. For example, observing the power consumption of a security device may yield information regarding secret data processed therein, or even reveal the secret key used to process this information. In principle, every side effect of semiconductor operation including timing behaviour, and the smallest traces of light emission or heat generation, can be used to extract secret data. For example, protection measures against “Differential Power Attacks” (DPA) would not automatically yield information on neighboured attack scenarios such as the successor attack “electromagnetic analysis” (EMA).
Semi-invasive attacks
With “semi-invasive” attacks, an adversary is trying to induce faulty behaviour in a security controller. Then, they can circumvent security decisions in the software, or manipulate data for their own purpose. Faulty cryptographic calculations may even lead to the extraction of a secret key. In principle, attackers can use every element that affects the behaviour of silicon chips: Electrical transients, called “spikes” or “glitches,” electromagnetic pulses, light or lasers, nuclear radiation from radioactive alpha particle sources, or temperature changes can be applied to induce faults.

Fig. 2. Nuclear radiation is used to circumvent “laser attack countermeasures”
A protection measures against “laser attacks,” an attack test often used in evaluation, does not automatically give indications regarding protection against other semi-invasive attack scenarios such as the use of nuclear radiation to induce faults.
Chip generations
In the 1980s, it became clear that software alone was insufficient to hold secrets or allow trusted processing. The first mass-produced commercial security microcontrollers appeared on the market. Indeed, in the first years, the step from software security to isolated chips was one a main method of repelling attackers. Adversaries soon found out that hardware could also be attacked — a variety of scenarios was developed to understand hardware functionality and subsequently extract hidden secrets to attack systems.
The industry, in turn, began developing hardware-specific countermeasures, ushering in the age of “conventional security,” which currently still exists. Until now, the approach was generally the same. Fundamental, system-intrinsic weaknesses were identified and mapped to known and anticipated attacks, and attack-specific “countermeasures” were integrated.
An example of this type of evolutionary approach includes “fault attacks,” used by an attacker to induce erroneous behaviour in a security controller. In this way, attackers managed to circumvent passwords, PIN entries, and even dumped secret keys and program code from security controllers. The first attacks were accomplished by “spiking,” which means applying electrical transients to the chip, causing it to make wrong decisions. Typical countermeasures included “spike sensors,” causing an alarm state so attackers jumped to optical fault induction (laser attacks) to achieve the same result.
Today, since most chips contain light sensors and other specific countermeasures against laser attacks, attackers simply use other sources to induce faults such as electromagnetic induction, alpha radiation, thermally induced voltage alterations, and many others. Many of today’s products are equipped with security features that are focused on specific attack scenarios or subgroups, like laser attacks or DPA.
Given that several hundred new attack scenarios occur annually, it is obvious that many questions were left open including: Who would know about a specific attack? It is not surprising that proficient attackers often keep their findings secret. So manufacturers of security controllers also must also ask, “What can be done to better protect a device against unknown attacks?”
The situation gets worse when countermeasures are tailored to only meet the attack equipment or parameters used in common tests. Is such a chip designed only for the purpose of surviving evaluation and certification?
After several years of research and development, a revolutionary approach for comprehensive security recently became a reality. The main idea was to find and eliminate root causes for the attackable nature of conventional designs by developing a new comprehensive architecture from the scratch. One of the tasks was to counteract complete groups of attacks instead of setting up scenario-specific countermeasures.
Requirements for a comprehensive security concept
Today, most typical security features should be eliminated when building the main security layer, as they are bound to specific attack parameters. A new comprehensive security concept must employ mechanisms that work independently from the characteristics of a single attack scenario.
The main requirements for designing future-orientated security concepts include:
• Strong hardware security.
• Easy-to-use technology.
• Autonomous security systems.
• Hardware should check itself.
• Robust designs.
• Mathematically modelled security mechanisms.
Technical realization
In the past, CPUs were not recognized to be one of the most important aspects of security controllers. Simple protection concepts such as adding parity bits in registers or other parts of the CPU were insufficient under attack conditions.
The use of a dual-CPU with very close denticulation allows comprehensive protection against semi-invasive attacks without negative impact on performance. Interestingly, such a system could often be more energy efficient, as other security measures that resulted in decreased performance, would not be needed anymore.
For protection against observative and manipulative attacks, encryption is very important. Conventional concepts, such as encrypting only memory and buses, still show a major weakness. Typically, the CPU, to process information stored in memory, had to use clear text. This effect can be compared to an encrypted email — a person could store his email or files in encrypted form on a computer, but to read it, it must be transferred to clear text first, making it vulnerable.
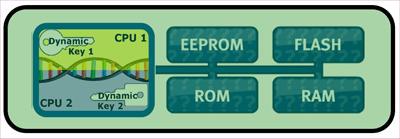
Fig. 3: Integrity Guard system with Dual-CPU error detection and encryption even in the CPU.
Today, it is even possible to process data in encrypted form in the CPU — if the CPU core itself is designed from scratch. Two CPUs can use different key sets each. In unpowered chips, such keys should of course not be “present,” but be volatile and dynamically generated and changed. In addition to silicon security features, production and distribution of these microcomputers must also be strictly controlled. These procedures may be compared to the use of special paper or special colors needed for the production of bank notes. These safety measures, as well as attack protection of the chips, are subject to the system security evaluations and certification.
Outlook
The future of security controllers for government ID applications is built through comprehensive digital security mechanisms. Mathematical modelling and simulation greatly simplify pre-evaluation. Uncertainties concerning upcoming attacks can be reduced. The paradigm shift toward encrypted processing of data in the CPU itself in combination with efficient error detection is a major step in security technology.
About the authors
Dr. Peter Laackmann is Senior Principal in the Chipcard and Security Division of Infineon Technologies AG. He has worked in the smart card industry, as well as for print and TV media as a consultant since 1991 and has written for numerous publications covering chip card technology and security.
Since 1991 Marcus Janke has been working on the conception, development and realizations of smart card systems. As author and consultant, he published numerous publications covering the sector of smart card security and held several lectures in this field. At Infineon Technologies AG, he currently leads the Product and System Security department. ■
Advertisement
Learn more about Infineon Technologies





