Unable to land a government job? Stuck in a low level political rut? Feel like everyone’s out to get you? Well, there may be a reason for that. A great chunk of the technology inhabiting our daily life is potentially spying us, making modern espionage a cinch compared to what it was during the cold war era. As Philip K. Dick foreshadowed decades prior, modern interconnectivity may be sharing more than you know.
1. Household appliances
Internet-of-things this, internet-of-things that. The more household appliances join the always-connected-to-the-internet club, the easier it’ll be for spies to track the living habits of a “person of interest.” By controlling ovens, microwaves, coffeemakers, lighting and electric systems wirelessly through the internet, we are generating vast amounts of geo-tagged data.
According to Wired, CIA Director David Petraeus stated prior to resigning, “Items of interest will be located, identified, monitored and remotely controlled through technologies such as radio-frequency identification, sensor networks, tiny embedded servers and energy harvesters — all connected to the next-generation Internet using abundant, low-cost and high-power computing,”
Tip: Do not connect appliances to the internet in sensitive parts of the home.
2. Street lamps
Amongst the odder assortment of internet-of-things items are street lamps. Intellistreets, as they are called, are increasingly used in cities across the United States even finding their way into the English streets of London. The lamps are manufactured in Michigan, by a lightning manufacturer called Illuminating Concepts, under the pretense of providing homeland security, traffic control, public safety, and advertising.

This is accomplished using a system of two-way communication capable of broadcasting real-time information through visual and sound cues. Along with energy-efficient lighting, Intellistreets feature built-in microphones, cameras, and visual displays.
Tip: Watch what you say publically. Certain “hot” words may trigger big brother’s attention.
3. Computers and keyboards
The majority of passwords stolen from users of infected computers occur because the user voluntarily gave that password up by typing it.
It is very common for trojans, worms, and malware to include key-loggers that record every keystroke typed on the keyboard while simultaneously recording a user’s web activity. This paints a clear picture of what websites you visit and your password for that account along with whatever credit card number you’ve typed.
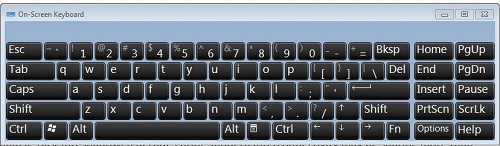
The On-Screen keyboard as it appears on Windows 7
Tip: Type all sensitive, account related information using an on-screen keyboard. On the PC, this can be accessed by clicking the Start Menu, All Programs, Accessories, Ease of Access, and On-Screen Keyboard. The primary purpose of the on-screen keyboard is make the computer usable in the event of a key-board malfunction, by virtually emulating a keyboard on the screen that users click on using their mouse. Mouse click are not tracked by malicious viruses.
4. Insulin pumps and pacemakers
White hat Hacker Barnaby Jack proved it was possible to wirelessly hack an insulin pump, commanding it to kill the wearer through insulin overdose. Prior to his sudden death, this same hacker was scheduled to speak at a Black Hat hacking convention, demonstrating how a programming flaw in commonly used pacemaker devices could be exploited for the same purpose.

Barnaby alleged that a hacker only need be within a 50 ft radius of the target in order to send the command that delivers a 830 volts of electricity into their heart. His claim may seem extremely radical, but bear in mind, this is the same hacker who proved that gambling machines and ATMs can be hacked into releasing money.
Tip: The US Federal Food and Drug Administration (FDA) “asked” manufacturers upgrade their security,; verify that your pacemaker, or future pacemaker has followed obeyed these suggestions.
5. Smartphones
Earlier in December, security expert Jacob Appelbaum presented a series of official looking NSA slides detailing the organization ability to transform iPhones into eavesdropping devices using a malicious software called DOPOUTJEEP. Apple denied these charges, arguing “Apple has never worked with the NSA to create a backdoor in any of our products, including iPhone,” according to a statement made to AllThingsD.
Tip: In any case, the security vulnerability of smart phones has long been known, particularly of those running the Android OS. Protecting yourself is a matter of using anti-viruses from reputable sources and smart browsing. Do not visit any websites you’d avoid on your home computer. Periodically, restore your phone to factory settings and format the SD card. As inconvenient as this may seem, it’s significantly less so than resolving fraudulent bank account charges.
All the apps you’ve purchased can be re-downloaded, and all the music and photos can be re-added.
Via Discovery News
Advertisement
Learn more about Electronic Products Magazine





