DeepCover® embedded security solutions cloak sensitive data under multiple layers of advanced physical security to provide the most secure key storage possible.
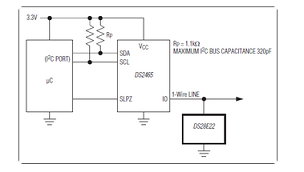
The DeepCover Secure Authenticator (DS28E22) combines crypto-strong, bidirectional, secure challenge-and-response authentication functionality with an implementation based on the FIPS 180-3-specified Secure Hash Algorithm (SHA-256).
A 2Kb user-programmable EEPROM array provides nonvolatile storage of application data and additional protected memory holds a read-protected secret for SHA-256 operations and settings for user memory control. Each device has its own guaranteed unique 64-bit ROM identification number (ROM ID) that is factory programmed into the chip. This unique ROM ID is used as a fundamental input parameter for cryptographic operations and also serves as an electronic serial number within the application.
A bidirectional security model enables two-way authentication between a host system and slave-embedded DS28E22. Slave-to-host authentication is used by a host system to securely validate that an attached or embedded DS28E22 is authentic.
Host-to-slave authentication is used to protect DS28E22 user memory from being modified by a nonauthentic host. The SHA-256 message authentication code (MAC), which the DS28E22 generates, is computed from data in the user memory, an on-chip secret, a host random challenge, and the 64-bit ROM ID. The DS28E22 communicates over the single-contact 1-Wire® bus at overdrive speed.
The communication follows the 1-Wire protocol with the ROM ID acting as node address in the case of a multiple device 1-Wire network.
Advertisement
Learn more about Maxim Integrated





