Internet-connected television? Hacked. Internet-connected refrigerators? Also hacked. And now, the latest contender of Internet-connected devises to have been hacked is the light bulb. White-hat hackers from Context Security have orchestrated an attack against smart LED bulbs that exposes Wi-Fi username and passwords to anyone in close proximity to the light bulb.
The attack was demonstrated against the programmable, smartphone controlled, LIFX smart LED bulbs that won the hearts of many-a Kickstarter supporters back in 2012, when the campaign raised 13 times its original goal of $100,000.
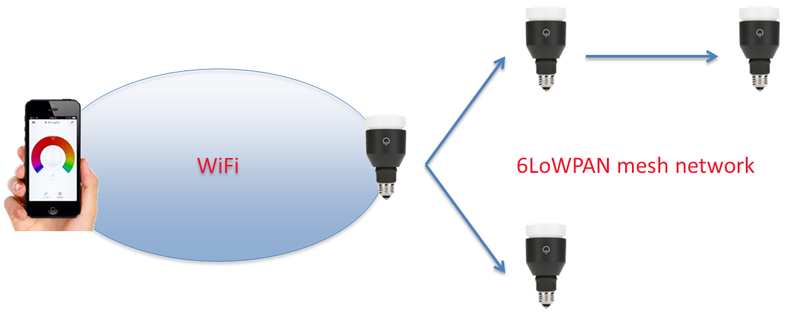
The exploit allowed hackers standing just 30 meters away to obtain passwords used to secure the connect Wi-Fi network by sending a command to the compromised bulb with their smartphones. Once commands are received, the credentials are broadcasted from the master bulb to all the other bulbs over a networked powered by 6LoWPAN, a wireless specification built on top of the IEEE 802.15.4 standard. Although the Advanced Encryption Standard (AES) was to encrypt passwords, the pre-shared key never changed, thus enabling hackers to easily decipher the payload.
“We bought some light bulbs and examined how they talked to each other and saw that one of the messages was about the username and password,” explained Michael Jordon, research director at Context Security, to BBC. “By posing as a new bulb joining the network we were able to get that information,” he added.
Given that version 1.1 of the LIFX firmware was unavailable for download, hackers were prevented from simply reverse engineering it to uncover specific crypto loopholes* that exposed the Wi-Fi credentials. Instead, Content Security’s engineers spent two weeks removing the microcontroller embedded within each bulb before connecting specific JTAG pins to a piece of debugging hardware that monitored the signals being sent whenever bulbs joined or left a network. “At this point we can merrily dump the flash memory from each of the chips and start the firmware reverse engineering process,” the researchers wrote.” *All it took was tampering with the hardware of a single bulb.
In response to the demonstration, LIFX developers released a firmware update this weekend that encrypts all 6LoWPAN traffic using an encryption key derived from the Wi-Fi credentials and secures connections when connecting the bulb to new networks. It’s unfortunate that the exploit was discovered long after the bulbs have already been manufactured, forcing consumers in the awkward circumstance of connecting the light bulbs to the Internet and updating its firmware.
In a broader perspective, the LIFX incident highlights the growing security hazard we smother ourselves with by becoming early adopters of the Internet-of-Things when the market is clearly unready to protect consumers against privacy threats. Given the low cost-of entry presented by crowd-funding organizations, the risk of incompetent solutions, with vast potential impact, falling into the hands of the public is significantly compounded.
Via Ars Technica, BBC
Advertisement
Learn more about Electronic Products Magazine





