Anyone who has used a personal computer at any point during the 90’s has inevitably heard of Id Soft’s Doom, the popular video game that helped consolidate the first person shooter genre established by Id Soft’s previous title, Wolfenstein. Well, the good news is that you can now play Doom from the discomfort of your Canon Pixma printer’ LCD display, or at least that’s what security researcher Michael Jordon (not the legendary basketball player) wanted to demonstrate was possible after hacking the Internet-connected printed.
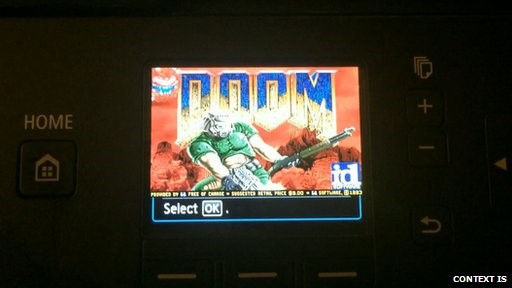
Jordon undertook the four-month endeavor of getting the game to run the printer’s hardware in order to demonstrate the inherent security flaws present in the heaps of Internet-of-Things labeled electronics being churned out. Like all IoT devices, the Pixma is remotely accessible, allowing users to check the device’s status; presumably, ink levels and print history. Jordon, a researcher employed by Context Information Security, discovered that the web interface had no user name or password requirement, allowing anyone to check the printer’s status.
BBC reports that a quick comb through Shodan, the search engine for Internet-connected devices, reveals thousands of other IoT devices similarly vulnerable.
Jordon observed that the remote access feature could be exploited to forcefully update the printer’s firmware through the same interface used to monitor the device. To Canon’s credit, the underlying code was encrypted to prevent outsiders from tampering, but not secure enough to prevent knowledgeable hackers from reverse engineering the encryption system and authenticating their own firmware. That was the easy part.
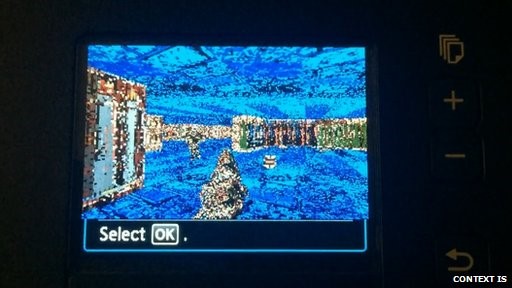
The challenge that took Michael Jordon four months to complete was converting Doom’s source code code into a version compatible with the Pixma’s 32-bit Arm processor; the printer’s software lacked the features found in a PC’s OS that are needed to run a game. But, after spending all his free time experimenting, Jordon finally had a working version just two days before he was scheduled to present his findings at UK’s 44con hacker convention.
“The color palette is still not quite right,” he said. “But it proves the point and it runs quite quickly, though it's not optimized.”
Unfortunately, the grueling hours left Michael Jordon disillusioned and unwilling to make the game run smoothly. “I'm so sick of it,” he tells the BBC. “I'm done.”
Canon exclaimed that it’s working to patch the loophole and make future devices harder to hack. Unfortunately, this is but one example of the myriad of security flaws that all early adopters of the IoT will be susceptible one.
Via BBC
Advertisement
Learn more about Electronic Products Magazine





