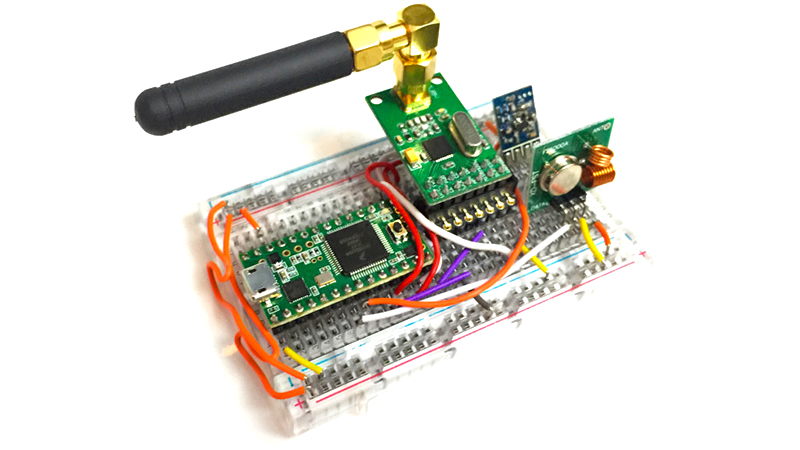
When was the last time you used an actual key to open your vehicle’s door? Wireless car key remotes and garage door openers are 21st century conveniences that’ve grown into expectations, but opening your door from a few meters away comes at a price: it’s an unreliable security measure that’s easily thwarted by an informed hacker with about $30 of over-the-counter electronics. During this year’s Defcon, the most renowned white hat/black hat hacker convention in the nation, “security researcher” Samy Kamkar debuted the “RollJam,” a homemade device called that’s able to intercept and the record the revolving security keys used by recording wireless fobs/remotes.
In principle, there are two types of wireless fobs: those that recycle the same code every time (and are very easy to hack) or those that generate a new code with each button press. The latter is obviously superior, but it too may be easily compromised with the RollJam. The device is designed specifically to subvert the revolving code security systems used with most modern automobiles keyless, alarm systems, and modern garage doors.
When placed in close proximity to its intended target, the RollJam uses a pair of cheap radios to emit noise on the two common frequencies used by cars and garages door openers and jam the signal, causing the first press of the key fob to seemingly not work while secretly recording the fob’s signal over the intended receiver’s signal. If the target presses the button a second time, the Rolljam jams the signal again while simultaneously broadcasting the code from the initial press. The target thinks the second press unlocked the door when in fact it was the first press that did it while the second press was diverted and stored for later use.
“You think everything worked on the second time, and you drive home,” says Kamkar. “But I now have a second code, and I can use that to unlock your car,” explains Samy. What’s most alarming is that a hidden RollJam can indefinitely repeat its cycle of jamming and intercepting no matter how many times the car/garage owner presses the keyless fob.
Samy has successfully tested the device on a number of vehicles from Ford, Toyota, Volkswagen, Chrysler, Nissan, and Lotus, in addition to after-market security solutions such as Viper and Cobra, and each has proven vulnerable. He does, however, credit the newer Cadillacs’ security system for using a temporal code that times out after a short time and becomes ineffective.
Code grabber have previously been used by thieves to subvert vehicle security, but the automotive industry had circumvented their past techniques by incorporating the current system of rolling codes that Samy’s device has proven capable of cracking.
Source: Wired
Advertisement
Learn more about Electronic Products Magazine





