Lancaster University computer scientists have developed a method of using Wi-Fi signal analysis to determine if and when web-connected devices are under physical attack.
This could prove to be significant with the continued proliferation of mobile devices, along with the ongoing establishment of IoT devices in both house and office.
 Now, while wireless transmissions can technically be encrypted to protect transmitted data from hackers, it’s hard to remotely determine if a web-connected device has been physically tinkered with.
Now, while wireless transmissions can technically be encrypted to protect transmitted data from hackers, it’s hard to remotely determine if a web-connected device has been physically tinkered with.
A good example of what’s being referred to here is a wirelessly connected security camera such as those seen on the outside of buildings, within airports, and around power stations (among other locations). An attacker may not necessarily try to hack the data transmission between the camera and its server, but he/she may tamper with the device by sending a signal to have it rotate away from the area it is guarding; and in this day and age, it’s quite easy to do so without ever triggering any sort of alert.

In their study, “Using Channel State Information for Tamper Detection in the Internet of Things,” the team of Lancaster computer scientists describes a new method they’ve established that analyzes Wi-Fi signals at several receivers to detect physical attacks to these devices. Specifically, they look for a change in the pattern of wireless signals being picked up by the receivers to determine if there’s been any sort of tampering done to the device.
The algorithm they created is able to detect attacks without being influenced by signal noise caused by such natural changes in the surrounding environment like, say, people walking through the communication paths.
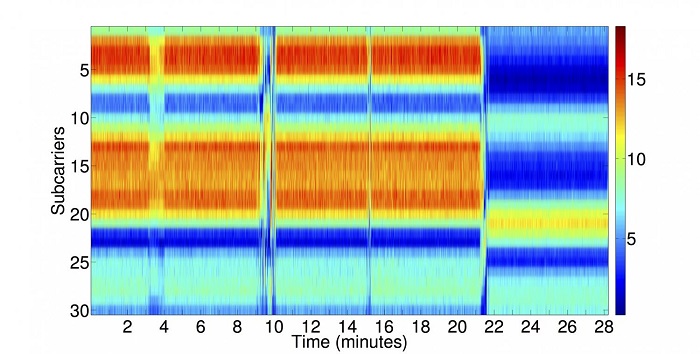
“A large number of Internet-of-Things systems are using Wi-Fi, and many of these require a high level of security,” explains Dr. Utz Roedig, Reader in Lancaster University's School of Computing and Communications and one of the report’s authors. “This technique gives us a new way to introduce an additional layer of defense into our communication systems. Given that we use these systems around critically important infrastructure, this additional protection is vital.”
To read the full study, download it here.
Via Phys.org
Advertisement
Learn more about Electronic Products Magazine





