Security may often be considered a job primarily for software solutions, but, especially in the case of disaggregated open radio access networks (Open RANs, or O-RANs), it cannot be achieved without hardware. In particular, there are vulnerabilities associated with O-RAN’s open ecosystem that cannot be mitigated without assistance from the microprocessors that control the key functional blocks ranging from the radio unit and distributed unit to the centralized unit and RAN intelligent controller.
Understanding the challenges
Unlike legacy, closed RANs, O-RANs exist in an open ecosystem involving standardized interfaces, protocols and interoperable hardware from multiple vendors who, in turn, are integrating components from multiple suppliers. This disaggregated multi-vendor environment impacts the threat surface area at the interfaces between the architecture’s integrated technologies. For this reason, designing and deploying radios and other equipment for Open RAN brings security challenges, starting with the hardware.
There are other security concerns. Service providers will face ongoing issues related to the use of open-source applications, as well as new 5G network functions and interfaces whose standards are still evolving. Additionally, mobile network operators will need to address all the challenges that any network faces, ranging from cloud infrastructure and virtualization to containerization and distributed denial-of-service attacks.
Yet another challenge with a multi-vendor environment is where the security responsibility resides. With traditional, proprietary RAN baseband units, a single supplier tends to bear this responsibility. With Open RANs, however, the responsible party will not be obvious and network operators may need to research which of their many suppliers they need to work with.
Many operators will create Open RANs based on the core of existing LTE networks that are already susceptible to passive eavesdropping attacks as well as active “man in the middle” attacks. Worse, the attack surface is only going to grow as the number of connected devices increases. As security management overhead correspondingly grows, network operators risk seeing the cost benefits of their O-RANs eroded as threat mitigation expenses rise.
Network operators can mitigate some of these security threats by leveraging features already integrated into established cloud-computing architectures, especially as opportunities for virtualization move RANs toward cloud-based implementations. Not all networks will be virtualized, though. Others may only have limited virtualization based on an assessment of the initial and ongoing cost benefits of implementing these types of networks.
Regardless of whether virtualized security is implemented, many security requirements can be met only through physical security at the hardware level. Securely storing boot data in a microprocessor and using cryptoprocessors is an important way to bring security into the hardware that runs Open RAN equipment while maintaining the benefits of Open RAN technology. This can be accomplished with off-the-shelf semiconductor and hardware platform technologies that are designed to deliver cyber protection.
Deploying a solution
Today’s O-RAN cyber-protection solutions based on semiconductors and other hardware platform technologies include embedded processors with integrated security features, as well as certified trusted platform modules (TPMs), that are built on industry-recognized specifications.
The U.S. National Institute of Standards and Technology (NIST) has published guidelines to help OEMs and component suppliers implement solutions like these that deliver stronger security in telecom O-RANs and other critical infrastructure. An example of these guidelines is the NIST Computer Security Resource Center’s NIST Special Publication 800-193, which provides recommendations for supporting resiliency of the collection of fundamental hardware and firmware components that comprise a platform and are needed to boot and operate a system. The NIST recommendations are designed to protect firmware and data against potentially destructive attacks that could render a system temporarily or permanently inoperable, leading to disruptions for users.
There are three core principles in the NIST guidelines. The first principle is to protect the system by ensuring code and critical data are protected from either malicious or inadvertent changes. The second principle is detecting threats by identifying when code and critical data have been corrupted. The third principle is providing a means to restore code and critical data to a known good state as part of the recovery process.
These three principles drive the criteria for securing any system that forms any part of the Open RAN network. The criteria include secure boot to facilitate a hardware-enforced root of trust that ensures software integrity at start-up, as well as the provisioning of unique and verifiable identities for authentication.
Also important is securing communication by transmitting only authenticated and encrypted data. There must also be secure programming and debugging, which requires removal of the interface ports that had been used during product development so there can be tight control over access to the system’s physical interfaces.
The final criteria include asset protection through tight control over passwords, encryption keys and security certificates, and lifecycle management to keep up with evolving cyberthreats, as well as the demonstration that all system devices are cyber-hardened and have undergone penetration testing and other assurance measures.
Each of these criteria has been addressed by the semiconductor industry. Manufacturers have developed a variety of chip technologies with integrated security features and capabilities so that equipment can be developed much more easily.
One example is proven secure embedded controllers that have been carried over from computing and network storage applications to the O-RAN space. These controllers are designed to provide security in the same type of open system environment that O-RAN equipment manufacturers and system architects face.
They also feature the requisite secure boot (root of trust) capability, combining immutable code in the boot ROM along with public/private key cryptography. The authentication requirement is met by requiring all application code to be authenticated using the public key before execution, as well as an elliptic-curve-cryptography digital-signature algorithm that is then used to authenticate the code and validate that it is not corrupt.
When using secure embedded controllers to meet NIST recovery requirements, redundancy is achieved by storing multiple images of the controller’s application code in external memory. This ensures that an alternative image will be used if the first image is corrupted at boot time.
After the application code is loaded, the controller’s crypto hardware can extend the protection, detection and recovery requirements to the code and information that is stored in memory, such as the basic input/output system and the management engine. If corrupt system code is detected, the application code can then use the backup or “golden” images to restore the system.
A NIST-compliant embedded controller can be based on a master attached flash (MAF) memory configuration using a single SPI flash chip, as shown in Figure 1. Alternatively, MAF can be configured with two SPI chips, or with shared flash memory using a single SPI chip, or as a shared MAF using a pair of SPI chips.
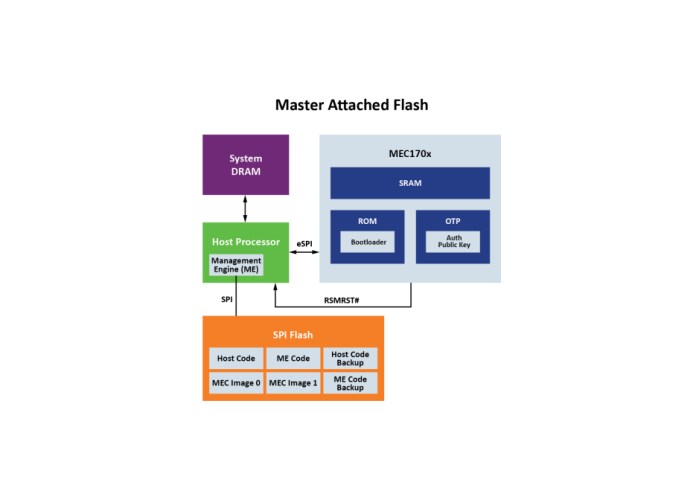
Figure 1: A system’s boot code and security keys are stored in a secure embedded controller that can be configured using a single SPI flash chip. (Source: Microchip Technology Inc.)
When an O-RAN equipment designer has based its hardware on microprocessors that do not offer secure system booting as an integrated capability, they lose this important first line of defense. They are unable to validate code prior to execution and need another way to add secure boot capability. This can be done with an off-the-shelf secure boot reference design built around the latest FPGA technology (see Figure 2).
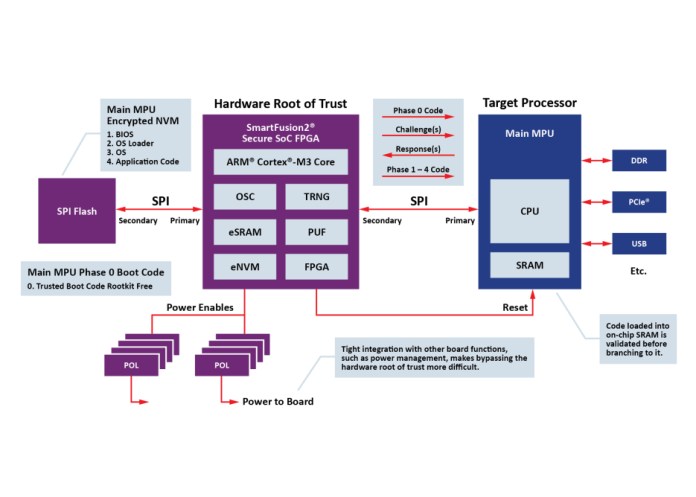
Figure 2: Secure system booting can be added even if the equipment’s microprocessor does not support it. Instead, an FPGA-based secure boot reference design provides a processor to handle the hardware root of trust for authentication. This processor can sit alongside the target processors and includes differential-power-analysis–resistant anti-tamper measures. (Source: Microchip Technology Inc.)
Meeting FIPS standards
Federal agencies have a particular need to ensure O-RAN security at the hardware level, so they protect sensitive information in computing and telecom equipment using cryptographic-based security systems. To meet this need, dedicated and standalone security cryptoprocessor ICs are now available that adhere to the Federal Information Processing (FIPS) standards developed by the NIST Computer Security Resource Center (CSRC) and support Trusted Computing Group (TCG) specifications.
FIPS-compliant chips perform like hardware crypto accelerators, enabling keys to be stored in protected hardware and managed so they can deliver multi-layer security. These chips offload complex security operations from the host processor and protect keys in hardware. They are widely available, cost-effective and proven in a broad range of embedded-system applications.
A single chip can combine a microcontroller, protected nonvolatile memory and strong, hardware-based public key (RSA) security technology. It can also implement the TCG specification for TPMs and include a FIPS-certified pseudo-random-number generator for key generation while offering secure boot, authentication, secure communications and intellectual property protection, as well as active shielding and a variety of capabilities for tamper detection and response.
Removing O-RAN security obstacles
Network architects must consider the safety and security of every possible O-RAN interface. This can be achieved using processors that help mitigate security issues so network operators can deploy robust and protected next-generation O-RAN infrastructures that meet the guidelines established by NIST and CISA.
These processors also support FIPs and TCG specifications while providing critical security functionality. This functionality can, in a growing number of cases, also be embedded in controllers and TPMs or, where this is not available, added via proven, off-the-shelf reference designs.
Advertisement
Learn more about Microchip Technology





