Zhang Wanqiao, a Chinese researcher from Qihoo, discovered a vulnerability that allows a hacker to eavesdrop on a conversation, read a user’s texts, and track the smartphone’s location through a 4G LTE weakness.
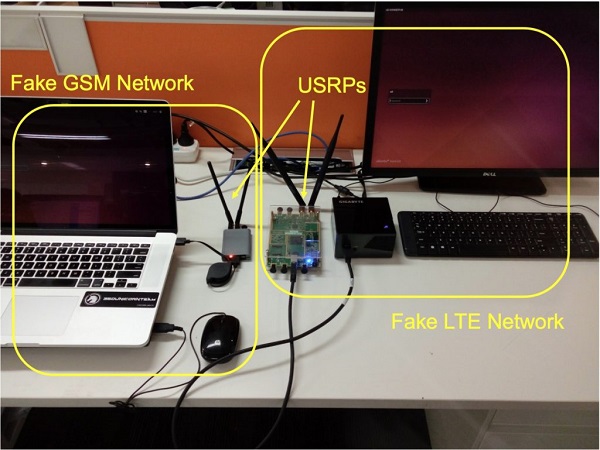
The vulnerability can be exploited on any 4G LTE network and is based off of a “fail-safe,” which is typically used during emergencies, such as natural disasters or phone tower overloads requiring redirection. The hack uses fake LTE towers to downgrade a phone’s LTE to 3G, and then ultimately down to 2G, where several vulnerabilities can be exploited.
While researchers brought this vulnerability up before, 3GPP, the organization that sets mobile data network standards and enforces them, acknowledged the problem but did nothing to fix it. In 2015, the issue was brought to the world again in a paper titled Practical attacks against privacy and availability in 4G/LTE mobile communication systems. That same year, the ACLU obtained documents that described the stingray surveillance as having identical vulnerabilities. Wanqiao extended the effective attack outlined by the initial researchers and presented it at DEFCON 24 in August 2016. Then, at Ruxcon this month, he demonstrated the attack, proving it can work on all LTE networks with readily available gear.
A possible reason the vulnerability wasn’t patched may be because it’s a surveillance technique actively used by law enforcement or intelligent agencies as a stingray or IMSI catcher device. While the specifics on how stingrays operate are not entirely clear, many people have drawn similarities between revealed technology and recent research.
As a solution to the 4G LTE vulnerability, choose a VPN that uses OpenVPN, and its TLS protocol will keep your conversations protected even in the event of an attack. Do note that older VPN methods, such as PPTP/L2TP/SOCKS, could still leave your device vulnerable. Since the attack uses readily available hardware and open-source software, an attacker could use this on your smartphone at any moment. As we saw with 3GPP 10 years ago, there doesn’t seem to be any plan to fix the vulnerability.
Source: Privacy News Online
Advertisement
Learn more about Electronic Products Magazine





