The Internet of Things seems poised to take over our lives if you measure its impact by the amount of press coverage it is receiving. However, the delivery of many of the potential applications envisioned could be jeopardized by security concerns.
There already have been internet-connected devices being hacked with dire consequences. The breach at Target stores that resulted in 40-million credit card records being stolen came in through the HVAC system. In a more ominous breach revealed just before Christmas, hackers struck a steel mill in Germany disrupting control systems so much that a blast furnace could not be properly shut down, resulting in “massive” damage.
Recent research conducted by Hewlett-Packard found that 70% of the most commonly used IoT devices have vulnerabilities. Security is becoming such a concern in the IoT world that we are witnessing key company acquisitions motivated by security. In fact, security was prominently mentioned by NXP as a reason for its acquisition of Freescale. Suppliers of IoT solutions are starting to use security as a key differentiator.
How do IoT device manufacturers make their products secure?
All experts are in agreement that there are many pieces to the puzzle, both on the software and the hardware side. There is no ‘silver bullet’ that can be added to a device to make it fully secure. Important limitations include the resource constraints in MCU-based IoT nodes: most existing security solutions require significant resources. It is important to recognize that chip designers creating new products are not security experts.
IoT memory needs security with power management
With the rapid adoption of IoT, focus needs to start evolving to the security of these devices without compromising power management. Since many of these devices are wireless and are pushing for more application capabilities and longer lifetime, power management is a necessity.
Memories are key components of IoT devices. They have multiple requirements and uses: low power with instant-On, small silicon footprint, programmable non-volatile code storage, and they must be highly secure. Embedded non-volatile memory (eNVM) has many forms such as embedded flash, electrical fuses, multi-time programmable (MTP), and one-time programmable (OTP). These are offered as embedded on-chip designs that are configurable, reduce costs, improve performance and enable secure storage.
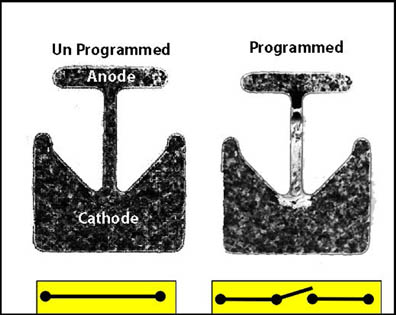
Figure 1: An eFuse register is not a secure solution because it is easy to identify the programmed bits. Programming is accomplished by silicide electromigration of the fuse link between the anode and the cathode.
For code that is fixed, ROM is the best eNVM solution. For code that changes often, requiring thousands of cycles of program/erase endurance and tolerating higher cost, flash-based technologies are the best. In between, where most IoT applications fall, logic eNVM technologies fill the need. These are embedded NVM IP implemented in standard logic CMOS, with no additional masks or processing steps.
In the logic eNVM space, technologies available in the market include:
- Poly fuse solutions typically provided by the foundry where change in resistance is created by blowing the silicide on the poly line
- Floating gate or charge-trapping solutions where the programming mechanism is hot carrier injection
- Antifuse solutions where “1”s are created from a hard oxide breakdown of the gate causing a resistive change
Antifuse is the most secure eNVM available today
Antifuse OTP is the non-volatile memory that has best-in-class security. It is proven to have lower power – both active and standby – and supports all the requirements listed above for IoT device memory.
eNVM using antifuse cannot be hacked using passive, semi-invasive or invasive methods. It provides a strong layer of protection at the most vulnerable physical layer – the issue with poly fuse. Unlike the floating-gate technology, the antifuse bit cell does not store a charge, hence there is no physical evidence of the state of the non-volatile memory bit cell. The bit determines an initial “0” or programmed “1” through the process of sensing current, not voltage.
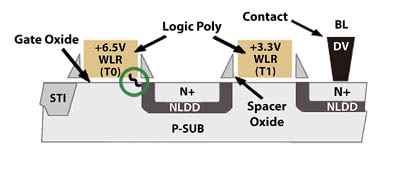
Figure 2: In antifuse eNVM bit cells, the gate oxide breakdown is statistical and can break at the channel, halo or LDD region, making it almost impossible to identify programmed.
Passive techniques using current profiles to determine the word pattern are unsuccessful because the bitcell current for “0”s and “1”s are much smaller than the current required for sensing or operating the peripheral circuits in order to read the memory. An intruder cannot determine the pattern of the word being read. Invasive techniques, including backside attacks or SEM passive voltage contrast, are unsuccessful because it is difficult to isolate the bitcell since it is connected in a cross point array. Furthermore, it is nearly impossible to determine which bit is programmed because it is difficult to locate the oxide breakdown using chemical etching or mechanical polishing and by looking at a cross-section or top view.
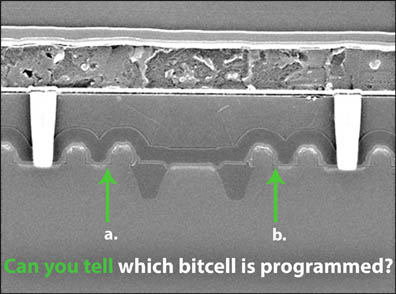
Figure 3: A cross-section of an antifuse NVM shows there is no visible difference between the programmed and non-programmed bit.
High-level security
Since information programmed into an antifuse bit cell provides a high degree of physical security, IoT device designers can integrate eNVM storage for data protection. This will make their system impenetrable to all but organizations totally not constrained by funding or time considerations.
Advertisement
Learn more about Kilopass





