Over the past decade, the volume of electronic components in automotive has increased at a dramatic rate. In-car networks are increasingly being designed-in and deployed to connect systems such as infotainment, driver assist, and safety systems, often on shared high-bandwidth infrastructures. These networks, and the devices that connect to them, require diagnostics and service through external interfaces. As the car becomes more connected, essentially becoming a network on wheels, concern for securing the network infrastructure is on the rise.
While the likelihood of a vehicle network breach is low, it is possible. Given enough time and resources, a hacker could develop a set of attacks and potentially distribute such an attack throughout an entire fleet. A single, well-engineered attack could have a wide impact. This is why auto makers are taking steps to ensure the security of the connected car.
The global standard of Ethernet has a long history of successful and secure deployment in dynamic, ever-changing, environments, such as the enterprise. Based on its high bandwidth, price-performance, ubiquity, and inherent network security features, the use of automotive Ethernet is definitely on the rise. Ethernet’s proven security features have an added advantage in automotive applications. The devices and configurations of in-car networks are known and predictable, so identifying and protecting against threats can be a finely tuned process.
Ethernet fundamentals
One of the key features that make automotive Ethernet well suited in preventing network breaches is its message authentication and encryption capabilities, which provide a strong first line of defense against malicious attacks. But this alone is not sufficient to fully secure the connected car.
Ethernet uses a standard packet format that includes a source and destination address, a VLAN tag and a frame check. This provides basic authentication, isolation, and data integrity. Further, because the in-car network is typically highly-engineered and static with predictable traffic characteristics, it offers the opportunity to tightly configure and constrain the network operation according to the design intent. For instance, the packet addresses can be used by Ethernet switches to provide traffic isolation and filtering, through either static provisioning or dynamic learning.
VLANs can be used to isolate traffic of different types on the shared physical network such that devices can only talk to the other devices within their domain. For instance, one VLAN can be configured for infotainment while a separate one can be configured for driver assist and another for safety, and network isolation between the two is enforced by the Ethernet switches.
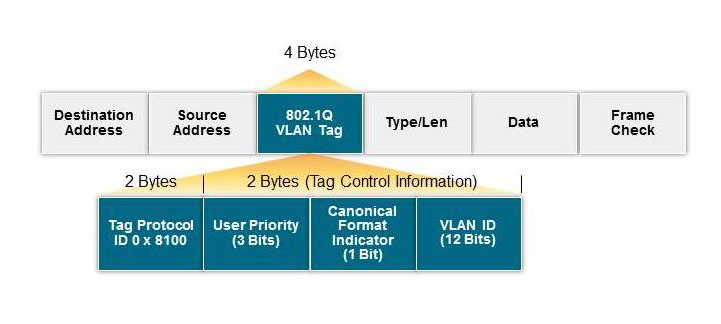
Figure 1: The Ethernet frame’s header contains destination and source MAC addresses as its first two fields and a CRC to verify packet integrity. It may also contain a virtual local area network (VLAN) tag, which defines a system and procedures to be used by bridges and switches.
Access control lists (ACLs) can be used to define precisely configured match-action rules for packet forwarding that define which stations can transmit, and where their traffic is allowed to go. Storm control enables the switch to monitor traffic levels and to drop broadcast, multicast, and unknown unicast packets when a specified traffic level is exceeded, protecting the network against violating stations. Flow-based policing can precisely define and enforce bandwidth rules on a per-flow level, protecting against rogue or faulty software. Finally, a rich set of statistics standards enable anomaly monitoring.
Device authentication
While each Ethernet packet contains a source MAC address, MAC addresses can be spoofed. The widely implemented 802.1x standard is one option to authenticate a device as valid prior to allowing entry on to the vehicle network. 802.1x defines a standardized means of passing Extensible Authentication Protocol (EAP) frames over a wired or wireless LAN. The framework allows for the exchange and validation of security credentials prior to granting access to the network. EAP supports many authentication methods (e.g., EAP-PSK and EAP-TLS); each one with its own set of authentication keys and credentials for device verification. The strength of the authentication is determined by the different methods and credentials used and this can all be pre-configured in the private environment at the manufacturing or service facility.
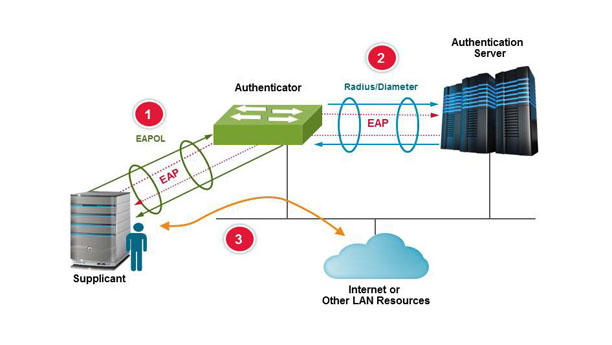
Figure 2: 802.1x defines a standardized means of passing Extensible Authentication Protocol frames over a wired or wireless LAN.
Data encryption
Encryption ensures that encoded data is accessible only to authorized parties. Encryption can be performed at many layers in the communication stack, including the Ethernet layer – the 802.11AE MAC Security (MACSec) standard offers MAC-level encryption and message authentication for Ethernet, using 802.1x for secure key exchange. However, it does require hardware support that brings with it added cost and power demands, and so is not typically supported in mainstream devices.

Figure 3: Automotive Ethernet’s inherent security features may just be the key to eliminating the connected car’s security vulnerabilities.
Ethernet has, of course, long been used in IT networks, its application in the connected car is an undeniably growing trend. Using automotive Ethernet as the centralized network backbone provides auto makers with the tools necessary to secure the network infrastructure.
Advertisement
Learn more about Broadcom





