By Patrick Mannion, contributing editor
The hacking of Equifax through an unpatched weakness in open-source software exposes two issues that developers wrestle every day when it comes to ensuring device and network security: management indifference and the need to be vigilant, even after a product has shipped, whether it’s hardware or software.
However, there are other issues facing network security as organizations move rapidly to dispersed cloud-computing data centers for critical business lines and the IoT continues to see more connected devices.
For example, according to a SANS Survey for Netscout, authored by Barbara Filkins, some organizations are reluctant to implement available active security features because of the performance impact (68%) and latencies they might induce, some are just tired of false alarms, and some are concerned about network downtime (Fig. 1 ). Not surprisingly, most companies had less than 20% of their in-line security features enabled: Only 5% used 100% of available in-line security features.
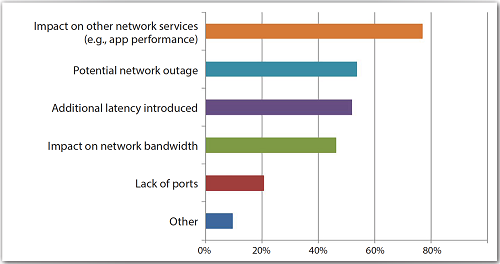 Fig. 1: The performance impact ranks highest among reasons for not implementing all available active security features. Image Credit: Sans Institute.
Fig. 1: The performance impact ranks highest among reasons for not implementing all available active security features. Image Credit: Sans Institute.
This need to balance the need for heightened security with concerns over latency and performance is one that designers of data centers and related equipment can address through hardware-based security.
This is one of the salient aspects of the AMD Epyc 7000 system-on-chip (SoC) announced earlier this year. Along with up to 32 Zen x86 cores and 128 PCIe Gen 3 lanes, AMD added a dedicated 128-bit AES encryption engine and hardware root-of-trust subsystem based on an ARM Cortex-A5 (Fig. 2 ).
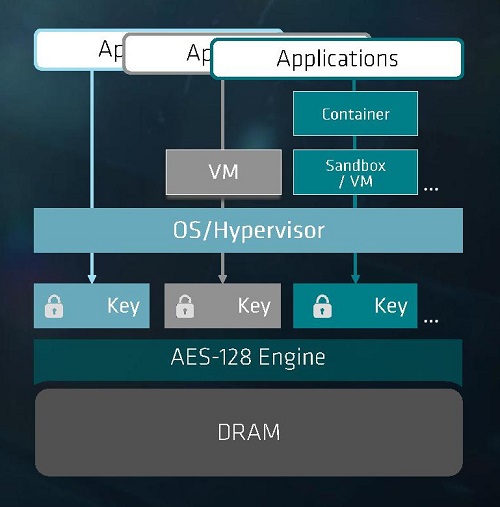 Fig. 2: AMD’s Epyc 7000 SoC has hardware root-of-trust based on an ARM Cortex-A5 that enables features such as memory encryption and secure encrypted virtualization.
Fig. 2: AMD’s Epyc 7000 SoC has hardware root-of-trust based on an ARM Cortex-A5 that enables features such as memory encryption and secure encrypted virtualization.
The security processor uses ARM’s TrustZone to partition the CPU to run sensitive and non-sensitive applications and tasks. It also ensures secure boot and runs the Trusted Platform Module (TPM) and its own OS/Hypervisor. This doesn’t exclude the use of an off-board TPM, which might be required by some customers.
Along with accelerating encryption, making the system more tamperproof, and lowering power and latencies, the architecture enables two unique features of particular use in the data center: Secure Memory Encryption (SME) and Secure Encrypted Virtualization (SEV).
SME protects against physical attacks by encrypting memory. SEV allows encryption of virtual machines (VMs) or containers so that applications can run securely.
Securing the IoT network end to end
In the case of Equifax, in-line security features such as those enabled by the AMD Epyc would have been of little use because the vulnerability was an unpatched version of Apache Struts, an open-source software package. As it wasn’t a zero-day vulnerability, Equifax could have prevented the attack by adherence to a simple rule: Update the software regularly, especially with respect to security patches.
This sounds so simple, but it’s so often overlooked. In the context of the IoT, it’s also hard to do, as there may be thousands of devices covering a wide geographic area. Also, few device manufacturers are convinced that they may be the target of an attack, so such devices are often woefully lacking in defenses, turning them into back-door entryways to corporate networks.
Recognizing the pernicious nature of the IoT security problem, whole companies have sprung up to fill the security gap between the hardware and the application. One such company is IoTium, which provides end-to-end security at the application and network layer, along with zero-touch management.
Specializing for now in industrial and smart-building applications, IoTium’s eNode OS is installed on the remote site’s gateway once a connection is established, and from there, all services and security are managed remotely through the cloud using IoTium Orchestrator (Fig. 3 ). Every data stream from every sensor is encrypted separately, and only the authorized end user can decrypt it.
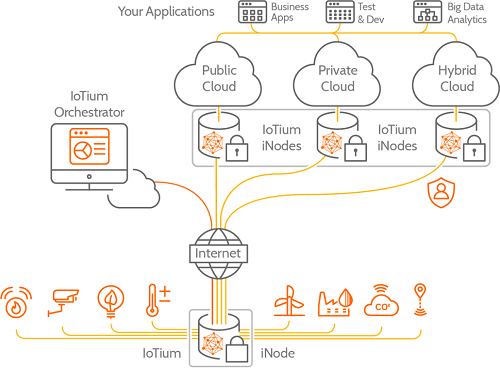 Fig. 3: IoTium’s zero-touch approach to IoT security ensures that data from all devices and sensors is secure end to end.
Fig. 3: IoTium’s zero-touch approach to IoT security ensures that data from all devices and sensors is secure end to end.
Critical aspects of the IoTium approach include the elimination of user names and passwords for each device or facility through public key encryption, no truck rolls, and no changes to IT’s enterprise proxy and firewall policies.
Of particular interest, given the nature of the Equifax debacle and the difficulty of updating many IoT devices, IoTium’s software is constantly updating itself, and all devices are fully provisioned and managed in real time. There’s no waiting around for a manual update. Every asset and every data stream is fully secured. In addition, new applications and services can be deployed at the push of a button across select devices or the whole network.
Embedded IoT struggles
For many embedded system designers, the difficulty of security starts with the fact that, traditionally, embedded systems were secure enough, as they were standalone and unconnected. Connectivity and the rise of IoT have raised awareness, but there are still time-to-market pressures, and often, the development team needs to push back hard on management to ensure that a device or system is thoroughly secured.
That said, the increasing use of over-the-air (OTA) updates is helping, but if a debug port is left open or memory isn’t secured, the device becomes an attack surface and a back door to the network.
Some other precautions to take include securing keys in EEPROM and erasing it upon tamper detect, or, better again, encrypting the key using public key encryption.
On the software side, Apache put out some reminders about network security enforcement that everyone should take to heart. Along with regular updates, it reminds users that any complex software contains flaws. “Don’t build your security policy on the assumption that supporting software products are flawless, especially in terms of security vulnerabilities.”
Also, establish network security layers: It’s just good practice.
Is security a losing battle?
While it may seem like an impossible task, achieving high levels of network security for the data center with minimal compromise in throughput and power is feasible, thanks to advances in hardware security as shown on AMD’s Epyc 7000. However, determined attackers are tenacious and it’s very much a case of making a network sufficiently secure so that attackers move on to the next, less secure device or system.
Advertisement
Learn more about Electronic Products Magazine





