
International law enforcement agencies are on the hunt for a team of cyber-thieves who’ve pulled off a string of Internet heists amounting to the theft of almost $100 million. Their primary tools of the trade: a digital keylogger that records login and password details used to access banking websites.
Dridex, as the virus is called, was first spotted by security researchers in November 2014 but gained notoriety following the apprehension of the a 30-year-old Moldovan named Andrey Ghinkul, the member of “Evil Corp” team who allegedly ran the Dridex botnet.
According to the UK’s National Crime Agency, Dridex may have triggered one of the worst cyber-attacks thus witnessed. The virus, which also goes by the pseudonym Bugat and Cridex, targeted specific individuals and small/medium-sized businesses from a database of 385 million email. Attacks were initiated using a series of emails that contained infected Microsoft Office or Excel files, but unlike worms and other Trojans, Dridex must be manually be downloaded by the person receiving the email; it cannot spread on its own.
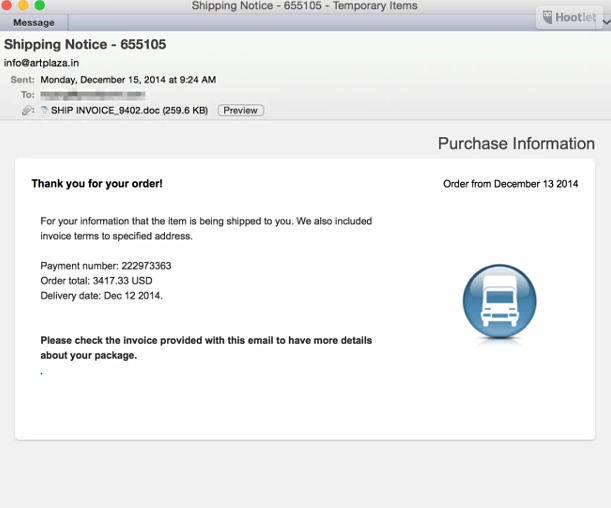
Emails are cleverly masked to resemble shipping invoices or commonly attached items
Once opened, the files trigger an embedded macro that serves as the catalyst for downloading an undetected Trojan. This Trojan, then installs itself in bowels of the OS and proceeds to unleash the keylogger. Unlike conventional viruses which rely on security exploits, Dridex bypasses legitimate channels, meaning, it won’t actually trigger unless the infected attachment is opened and the macro is run. Contemporary versions of MS Word and Excel require that the user willing consent to running the macro.
Worth noting is that the virus’ range of motion is limited to the Windows OS; Mac OS X and Chrome OS are unaffected as are smartphones.
How does it steal money?
Installation grants Dridex a wide range of control over infected computers, allowing it to upload, download, and run programs, as well as take screenshots of Internet browsing. Worse, the virus integrates the computer into the wider Dridex “botnet,” allowing its controller to use the infected computer to commence additional attacks—the majority of spam email attacks are autonomously waged by botnets.
While it’s not actively infecting other computers, the viruses incubates, waiting to snatch any inputted bank, email, or social media log details.
How to stay safe?
First and foremost, avoid opening attachments from unknown emails. Next, ensure that OS and cyber security software is up-to-date. If you do not possess an anti-virus, visit the NCA recommended websites CyberStreetWise and GetSafeOnline for links to sites where you could obtain some free solutions. Essentially, the rest is common sense: practice good browsing and computer security habits and you’ll remain safe
Source: The Guardian
Advertisement
Learn more about Electronic Products Magazine





