Digital power supplies make a system tamper proof
Digital power supply technology, encryption, and design techniques can make access to critical systems impossible
Many of today’s sophisticated electronics systems are being relied on to process store and communicate sensitive information which is of a critical and confidential nature. These systems can range from banking systems, medical systems, computers in police and public safety vehicles, military systems, servers to computers and more.
Today thieves are compromising systems not for the street value of the hardware – that can be relatively insignificant. The goal is breaking in to haul away the systems then data mine them for information or technology they can steal for identity theft purposes or to obtain an advantage.
In many cases, financial institutions and medical industries go to great lengths to institute security processes such as Health Insurance Portability & Accountability Act (HIPPA) and other policies or software encryption — frequent password changes and more which often times which simply frustrate legitimate users of data and systems. Meanwhile the thieves simply break into the front door of the medical or mortgage office in the unguarded strip mall.
They know they have time to compromise the light physical security and quickly remove what they have targeted they will be gone by the time authorities arrive. Meanwhile they have taken exactly what they wanted – the hard drives with the information they can access at their leisure at another location — passwords on systems are easily compromised once the hard drives are in hand.
It is also desirable to make sure that equipment which is compromised is rendered inert. Several years ago a navy Electronic Intelligence (ELINT) aircraft collided with a Chinese fighter and landed in China. The crew was detained and the aircraft and equipment was secured and inspected and later returned to the US military in crates.
Despite the crew’s best attempts to destroy computers, hard-disk drives, and other important equipment and data before landing, it is probable that some sensitive and/or secret military information fell into the wrong hands. As a result of this incident, policy has changed with efforts implemented to make it as difficult as possible for foreign nations to obtain sensitive U.S. information and technology resulting from a similar events ever occurring again.
This has led to what is referred to as “anti-tamper” technology, which seeks to slow or prevent the unauthorized reverse engineering or information retrieval of electronic equipment, computers, software, and other critical technologies and data. In critical military systems this can mean the difference between winning and losing battles or even wars.
Examples include protecting vital information from terrorists or where equipment is lost, stolen, captured and otherwise comes into contact with potential adversaries. In the commercial arena, systems such as ATMs are outside or sitting in a hotel lobby unguarded or commercial systems are in office buildings with no guards and limited physical security. Again, as much as policy and software encryption accomplished for sending and receiving data, they are of no use if a smash and grab operation is undertaken on facilities with weak and limited physical security.
Anti-tamper approachesSoftware GrammaTech (Ithaca, NY) creates software which can allow secure coding of systems. These systems offer trap doors or other hidden code to prevent its use in case an event occurs where deactivation is necessary. Due to its sensitive nature, details of anti-tamper technologies largely are classified secret so as not to give away how to keep the secrets.
Since anti-tamper technology can be applied to software, as well as hardware-and sometimes the best anti-tamper approaches involve both at a system level. GrammaTech software engineers are experts in the manipulation of software source code and binary code to enable reverse engineering, as well as to prevent reverse engineering. From systems level software, methods of erasing information and destroying circuitry which can fall into the bad guy’s hands must all be considered.

HardwareAnti-tamper approaches that involve hardware can range from placing crucial software code in FPGAs which can be erased on command to physically destroying crucial components through destructive means – this can include applying overvoltage’s and over currents to the devices or even pyrotechnics. The goal being to destroy the IC’s and firmware — disable the power supply, erase or destroy —overwrite memory contents, software etc before access can be obtained to data and algorithms.
One possible brute force method uses recently developed technology from Exar. The programmable digital power supply controller is well suited to this application. The power system can be controlled via an I2 C interface and has multirail power supply capability.
Consider at a system level the controller would be operating in a normal mode supplying 1.8, 2.2, and 3.3 V to ASICs, FPGAs, memory, microprocessors, microcontrollers, and such. A small microcontroller that is powered by the LDO in the 7714 controller would be activated when an event is triggered, which signals that a compromise situation is occurring.
Here are some examples: there could be an alarm signal that access has been gained in a physically secured area, it could be the signal for explosive bolts on a fighter canopy, an encoded RF signal to a transceiver that has fallen into hostile hands, or any number of event detection situations. Data could be overwritten and erased first.
Additionally there is technology available to trigger the microcontroller operations for the destruct sequence when a valid signal is received. In the case of a wireless device this can be triggered by a coded RF signal. Additionally, electronic fence technology is available which can secure an area electronically — when a device is taken outside of the electronic fence zone the microcontroller triggers the destruct sequence.
Moreover, a GPS signal could monitor where the device is physically located and if the device is detected out of bounds of the GPS area where its use is authorized a destruct sequence could be activated. For example, a secure radio that detects its in Pakistan and its not supposed to be — causes an event to be detected at that point.
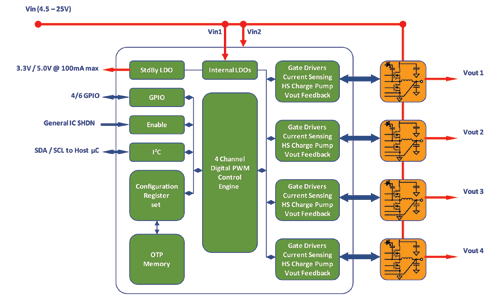
How it might work: The destruct sequence would entail the following , a valid event is detected At this point in time the power supply would set over current and over voltage trip points to maximum levels or even disable them — at this point the system would then set the output voltages to maximum levels for some period of time.
Subsequently, the micro would blow all the antifuses in the power supply controller rendering the power supply useless. This effectively burns out all of the VLSI devices and then makes the power supply inoperative. This occurs after data has been erased and overwritten in the storage areas of the device.
The goal is that equipment winding up in the wrong hands is worthless, burned up electronics and any memory contents are destroyed, erased, overwritten. Recent advances in digital power supply controller technology combined with mixed precautions of software encryption, cleaver hardware, and software design can render it difficult or impossible to access critical systems when these technologies are employed. Recent events underscore what happens when technology winds up in the wrong hands and is subsequently used against us. ■
BY KEVIN PARMENTER
Exar, Fremont, CA
www.exar.com
Advertisement
Learn more about Exar





