A major challenge in today’s increasingly hyper-connected world is how to protect new designs from cloning, reverse engineering, and/or tampering. FPGAs can help achieve these objectives through the inclusion of special features that address security needs all the way down to the device level.
The growing IoT security needs
The IoT can be seen as multiple electronic networks that require end-to-end layered security, starting at the device level (see Fig. 1). To help achieve this layered security, FPGAs can include unique built-in features and differentiated capabilities, and can also become the root of trust in what often are very complex applications.
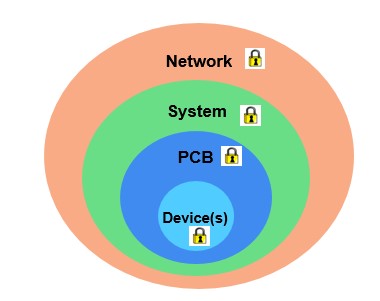
Fig. 1: Connected systems need end-to-end, layered security beginning with the device.
The solution starts with an FPGA whose embedded security works inherently and allows the system architect to plan its security architecture at the core level rather than as an afterthought. Many SRAM-based FPGAs have a fundamental problem in that they must be configured from an external memory each time they are turned on, thus exposing the design to reverse engineering. A better approach is the type of FPGA that stores configuration information on-chip in NVM.
Because data security is one of the most important security layers, the FPGA must protect all data, including the application data that it is processing. Numerous data protection features should be considered, including hardware protection from side channel attacks like differential power analysis (DPA) attacks. Simple and differential power analysis (SPA/DPA) can be used to extract secret keys by measuring power consumption during cryptographic operations like bitstream loading.
An important consideration is machine authentication through the use of a physically un-clonable function (PUF) to generate a private public key pair. Fig. 2 shows the architecture for a PUF that serves as a “biometric” identifier unique to each device – analogous to a human fingerprint, in that no two are alike, and they are considered unclonable.
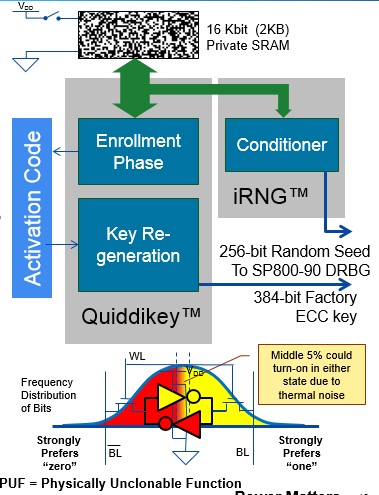
Fig. 2: SRAM PUF architecture takes advantage of the quasi-static random start-up behavior of SRAM bits.
SRAM PUF
An SRAM physically un-clonable function is one of the best characterized and most reliable types of memory PUF. It can be implemented on a smartcard chip, FPGA or other IC, and works by measuring the random start-up state of the bits in a block of SRAM. Each SRAM bit comprises two cross-coupled inverters that are nominally equal but not completely identical. As power is applied to the IC, each SRAM bit starts up in either the “one” or “zero” state based on a preference that is largely determined during IC manufacturing.
When inverters are exceptionally well balanced, thermal noise may occasionally cause the bit to overcome the pre-determined preference and start-up in the opposite state. However, the preference generally overcomes any dynamic noise, and the use of error correction techniques are usually all that is required to restore any noisy bits to original values and ensure the same key is reconstructed at each turn-on.
The SRAM PUF can be designed to guarantee perfect key reconstruction over all environments and its full lifetime with exceptionally low errors – as low as one per billion. Additionally, there is extremely strong protection of the SRAM PUF’s secret key since the SRAM PUF’s secret effectively disappears from the device when the power is off. If the activation code is erased, no amount of subsequent analysis will reconstruct the PUF secret key.
Cryptographic capabilities
Implementing PUF technology in an FPGA or SoC FPGA requires that the devices include built-in cryptographic capabilities such as hardware accelerators for AES, SHA, HMAC, and elliptic curve cryptography (ECC). Also required is a cryptographicgrade true random bit generator. With these capabilities, it is possible to create a user public key infrastructure with the user's own certificate authority blessing each legitimate machine in the network. This ensures that each machine has a chain-oftrust extending all the way from the user's well-protected root-CA keys on to the high-assurance, atomic-level identity that has been established by the FPGA’s PUF. Together, the PUF and PKI ensures that every machine and their communication are protected and can be safely, securely and confidently used in M2M, IoT and other hyperconnected applications.
Advertisement
Learn more about Microsemi





