Security researchers from Israel have demonstrated just how easy it is to capture the radio emissions given off by personal devices like laptops and tablets, and which include within them data about the keys.
And they did this using a gadget small enough that it could be concealed within a serving of pita bread.

Prior to this demonstration, capturing these radio signals was though to require very bulky and very expensive equipment. But the four-man team out of Tel Aviv University proved one could accomplish this feat using cheap components that simply monitor the radio signals given off when a nearby device’s central processing unit is crunching data.
Specifically, the team discovered that many different data crunching operations in a computer, like playing games, decrypting files, etc., had a characteristic pattern of radio activity.
The different power demands a CPU made while it was working gave further rise to these signals. And by monitoring these signals when the computer was decrypting an email message sent to it by an attacker, it became possible to work out the unique key being used to secure data.
Upon demonstrating that the attack worked in the lab, the group went ahead and created a mobile version called the Portable Instrument for Trace Acquisition, or PITA for short. During their follow-up test, they were able to prove outside the lab that their technology worked from a distance of about half-a-meter, grabbing keys used in several widely used encryption programs and algorithms used to protect data.
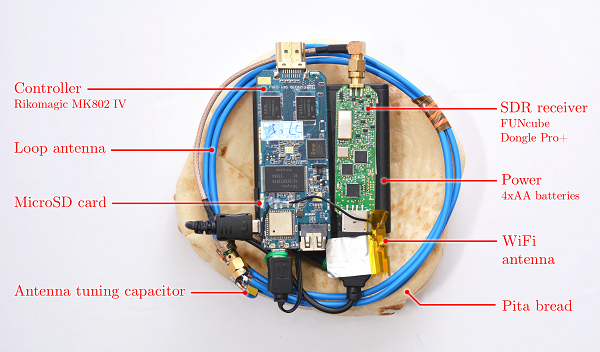
Needless to say, at this point in the game, it’s probably pretty easy to steer clear of anyone less than two-feet away who happens to be carrying a piece of pita bread that has blinking lights and wires sticking out of it. But looking down the road, the technology demonstrated by these researchers should be noted, as it proves it’s on the horizon, and that these things are not only possible, they could be even more prevalent just a few months down the road.
The group will formally present their findings at the Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2015 in September 2015. Until then, you can check out their paper: Stealing Keys from PCs using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation for free.
Via BBC
Advertisement
Learn more about Electronic Products Magazine





