A malware platform referred to as “ProjectSauron” and “Remsec” was implemented five years ago and only discovered a few months back. Security experts reviewing the program’s script have determined it is so advanced in its design and execution, that it was likely developed with the active support of a nation-state.
It’s been active on approximately 30 targets since 2011.
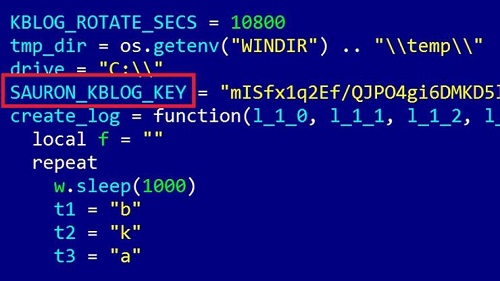
The fact that the platform has gone undetected this long is a credit to its creators, who likely studied other state-sponsored hacking groups and replicated their advances to avoid making any mistakes with this particular execution.
For those curious, some of the more (in)famous state-sponsored malware programs being eluded to includes Stuxnet, Flame, Duqu, and Reign.
In the case of ProjectSauron, the platform exists only in a computer’s memory, and it was written in the form of Binary Large Objects, thus making it difficult for antivirus software to detect its presence.
What’s particularly interesting about ProjectSauron is the software artifacts it has left behind within its targets; specifically, the fact that these clues are unique in each instance. This means that an artifact collected from one infected location does not help researchers in discovering new infections elsewhere. This is extraordinary from a code writing perspective because with most malware the same server, domain name, or IP address is reused for command and control channels; with ProjectSauron, a different one was used for nearly every target.
“The attackers clearly understand that we as researchers are always looking for patterns,” Kaspersky Lab researchers wrote in a report published Monday. “Remove the patterns and the operation will be harder to discover. We are aware of more than 30 organizations attacked, but we are sure that this is just a tiny tip of the iceberg.”
Another notable feature of the platform is its ability to collect data from air-gapped computers, which was executed via specially prepared USB storage drives that have a virtual file system not viewable by Windows OS. For computers infected with the malware, these removable drives appear as approved devices to the user, however, what’s hidden is several hundred megabytes specially reserved for storing data that is kept on the air-gapped machines. The code for this execution was written in such a way that it was able to operate even on computers outfitted with data-loss prevention software against the use of unknown USB drives.
Kaspersky researchers admitted they’re not exactly sure how this USB-enabled exfiltration works; the mere presence of an invisible storage area doesn’t allow attackers to seize control of these computers. So the immediate conclusion is that the purpose of this capability is meant to be used only in extreme cases, and that it likely requires the use of a zero-day exploit (which hasn’t yet been discovered).
All total, ProjectSauron is made up of at least 50 modules, all of which can be mixed and matched to meet the needs of each infection’s set of directions.
“Once installed, the main Project Sauron modules start working as 'sleeper cells,' displaying no activity of their own and waiting for 'wake-up' commands in the incoming network traffic,” Kaspersky researchers wrote in a separate blog post. “This method of operation ensures Project Sauron’s extended persistence on the servers of targeted organizations.”
Security experts discovered the malware late last year after a customer at a government organization brought them in to investigate some irregular network traffic. While researching the matter, the team discovered an executable program library that was loaded into the memory of one of the customer’s domain controller severs. Basically, this library was mocked up to look and act like a Windows password filter, which system administrators often put onto computers to ensure passwords match requirements for length and complexity. It started every time a network or local user logged in or changed a password, and was able to view passcodes in plaintext. This allowed the program to provide its operators with passwords, cryptographic keys, configuration files, and IP addresses of the key servers related to all active encryption software.
Groups that were infected include multiple government agencies, scientific research centers, military organizations, telecommunication providers, and financial institutions located throughout Russia, China, Sweden, Belgium, Rwanda, and possibly in Italian-speaking countries.
Due to how incredibly sophisticated the ProjectSauron malware appears to be, the security experts looking into the program are guesstimating that more than one specialist team was used in the creation of the program, and that it likely cost several million dollars to develop.
“The actor behind ProjectSauron is very advanced, comparable only to the top-of-the top in terms of sophistication: alongside Duqu, Flame, Equation, and Regin,” the Kaspersky researchers wrote. “Whether related or unrelated to these advanced actors, the ProjectSauron attackers have definitely learned from them.”
Via ArsTechnica
Advertisement
Learn more about Electronic Products Magazine





