 Ransomware, as its name implies, is a type of malware software that encases computer files in a malicious encryption unless the victim pays a conciliatory fee. While there are different types of ransomware , they are all deigned to prevent the normal operation of a computer. Here’s a brief look at the decade-long history of ransomware, and what its future might hold.
Ransomware, as its name implies, is a type of malware software that encases computer files in a malicious encryption unless the victim pays a conciliatory fee. While there are different types of ransomware , they are all deigned to prevent the normal operation of a computer. Here’s a brief look at the decade-long history of ransomware, and what its future might hold.
Early ransomware:
Initially observed in Russia between 2005 and 2006, one of the first ransomware variants called TROJ_CRYZIPA was created by Russian organized criminals, largely targeting Russian and neighboring countries’ computers running Windows 98, ME, NT, 2000, XP, and Server 2003. Once covertly downloaded by a user, usually through an email link or phony website, the malware would identify files with a certain file-type and move them to a password-protected ZIP folder, deleting the original copies. Once executed, the ransomware would prompt users to transfer $300 to an E-Gold account, an anonymous gold-based digital currency, to recover the files. Later ransomware versions would use anonymous crypto-currencies like Bitcoin, prepaid credit cards, or even premium-rate phone numbers as ransom payment methods.
Global threat: the power of the law
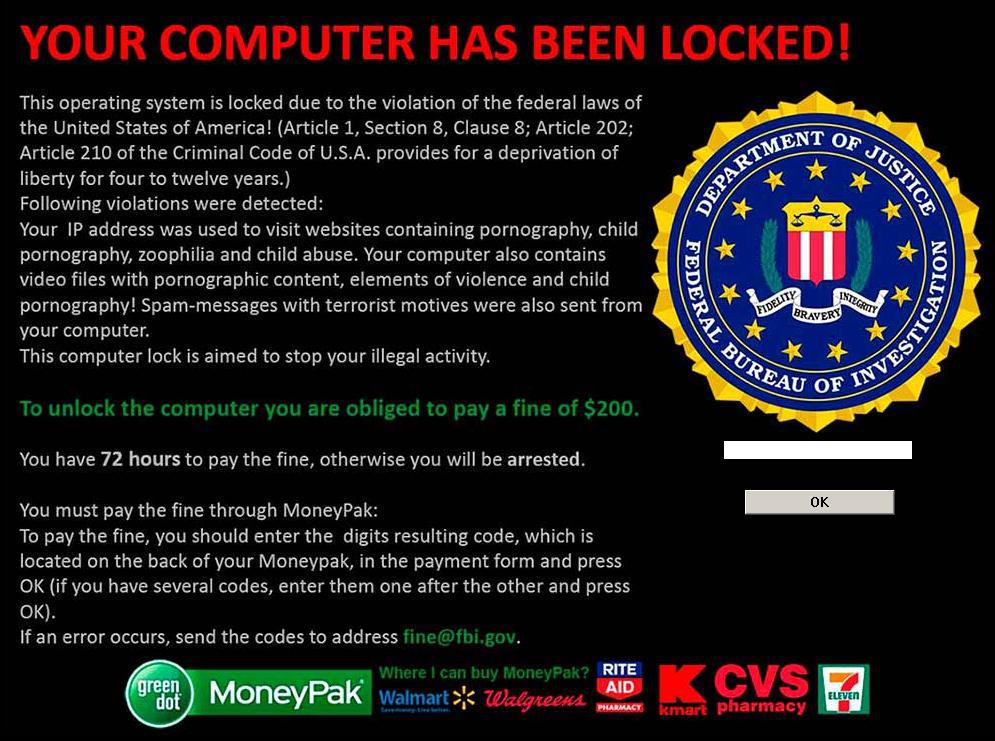 Toward the end of the 2000s and beginning of the 2010s, an increasing global familiarity with ransomware and growing air of caution prompted cybercriminals to get creative by, ironically, using police impersonation for extortion of ransom. After accusing the victim of being involved in internet crime such as copyright infringement or downloading illicit pornography, the ransomware informs the user that the computer is under investigation and subsequently locks the computer.
Toward the end of the 2000s and beginning of the 2010s, an increasing global familiarity with ransomware and growing air of caution prompted cybercriminals to get creative by, ironically, using police impersonation for extortion of ransom. After accusing the victim of being involved in internet crime such as copyright infringement or downloading illicit pornography, the ransomware informs the user that the computer is under investigation and subsequently locks the computer.
The user would then be faced with a choice: pay a “fine” that would drop the (non-existent) charges and return access to the computer or refuse and be threatened with arrest, trial, and potential imprisonment. If the victim delayed the decision, the fine would double.
One of the most globally recognized police-impersonation ransomwares was Reveton, which used localized data to appear more legitimate as a local law enforcement agent. The makers of the strain localized Reveton for virtually every European country, as well as Australia, Canada, New Zealand, and the US. However, since it did not encrypt users’ files, it could be removed simply and completely with an antivirus live-CD or by booting the computer into safe mode.
Leveling up: crypto-ransomware
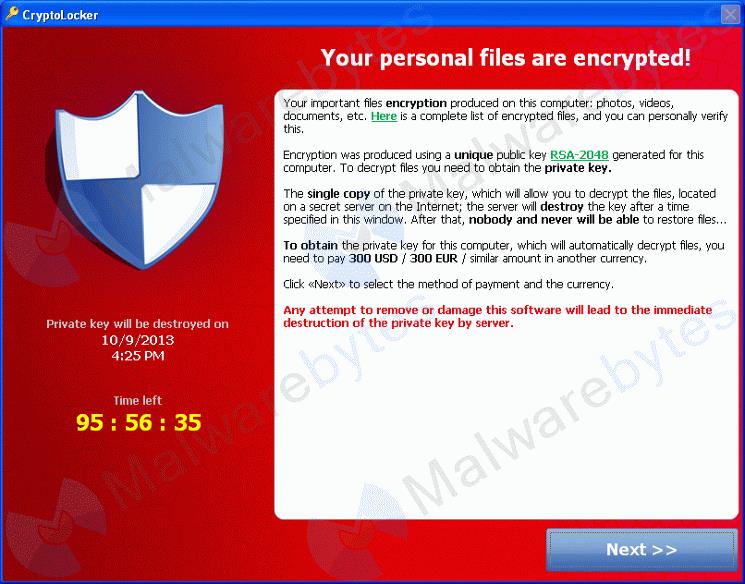 While Reveton was easily vanquished, the advent of crypto-ransomware, which employs near unbreakable encryption to entomb users’ files, cannot be so easily deciphered. Even after the malware is removed, the files remain locked, putting pressure on victims to pay up.
While Reveton was easily vanquished, the advent of crypto-ransomware, which employs near unbreakable encryption to entomb users’ files, cannot be so easily deciphered. Even after the malware is removed, the files remain locked, putting pressure on victims to pay up.
The first widely-recognized crypto-ransomware, CryptoLocker, premiered in 2013, and according to ZDNet, generated an estimated $27 million in bitcoin ransom. Distributed through infected email attachments propagated through spam networks, as well as through the Gameover ZeuS botnet , CryptoLocker would systematically encrypt document and media files on an infected device with a strong RSA public-key cryptography. The victim would then have 72 hours to pay a $400 ransom, either through Bitcoin or GreenDot MoneyPak — another pre-paid cyber voucher system — or the operators would threaten to delete the private key, making decryption impossible.
In June 2014, Operation Tovar, a coalition of academics, security vendors, and law enforcement agencies, was able to take down the CryptoLocker distribution servers and release a service which allowed victims to decrypt their files for free.
CryptoLocker, while short-lived, proved to security vendors and criminals alike that the crypto-ransomware model could be lucrative, and resulted in a digital arms race between cyber crooks and cyber guards to enhance and mitigate sophisticated ransomware variants.
Ransomware gets smarter:
TorrentLocker emerged shortly after the fall of CryptoLocker as its rapacious successor. Using malicious email attachments, especially Word documents with malicious macros, the crypto-ransomware encrypts the usual assortment of media and office files using AES encryption. What’s more, TorrentLocker increases its criminal legitimacy by displaying the ransom notes in the victim’s local currency.
CryptoWall 4.0 pushed the ransomware game up a level by changing the way it infects systems. By renaming all infected files, it prevents users from determining what has been encrypted, making it harder to restore the device from backup.
New targets:
Most ransomware developers target computers and devices running Windows or Android platforms, simply because the large market share of users makes for more alluring targets. Now, developers are slowly staring to shift to niche platforms, including KeRanger ransomware that targets Mac computers and Linux.Encoder.1, which was discovered in November 2015 targeting Linux users.
The future of ransomware:
In the past few years, the development of ransomware has become a small franchise, with developers now working with ransomware distributors to increase reach and impact.
Furthermore, while many ransomware strains have earned name recognition, some manufacturers are aiming to white-label ransomware so that it can be rebranded. By making products as anonymous and generic as possible, it is feasible to create hundreds of variants of ransomware from one main strain.
In the first quarter of 2015, over 725,000 ransomware samples were collected by McAfee Labs, meaning law enforcement and security industries have been under constant stress in an effort to quell the surging tide. In July 2016, a group of computer science researchers from the University of Florida developed a blockade-type software called CryptoDrop that can inoculate computers against a ransomware attack.
There are also a number of simple measures one can take to properly prepare a system against a ransomware attack. Keeping OS and antivirus software up-to-date and practicing smart browsing habits are among the easiest ways to prevent ransomware from infecting a device. With the digital world established as component of daily life, it is imperative users are able to identify and mitigate the threats of ransomware.
Sources: MakeUseOf
Advertisement
Learn more about Electronic Products Digital





