Two experts at the Chinese University of Hong Kong unveiled an exploit affecting Android apps that could potentially leave more than 1 billion installed applications susceptible to attack. It relies on a man-in-the-middle (MitM) attack of the mobile implementation of the OAuth 2.0 authorization standard.
So what exactly is OAuth? It’s an open standard used by several websites and apps, allowing users to log into a third-party app or website by using an account from one of the OAuth providers. The most well-known examples are Google, Facebook, and Twitter.
The Single Sign-On (SSO) button grants users access to account information. After you click the Facebook button, the third-party app or website searches for an access token and gives it permission to view your Facebook information. If the token is not found, you’ll be asked to allow the third party access to your Facebook account. Once you’ve authorized this, Facebook receives a message from the third party, requesting an access token. The social media platform responds with a token, giving the third party access to the information specified.
For example, you can grant Facebook access to your basic profile information and friends list, but not your photos. The third party receives the token and lets you log in with your Facebook credentials. As long as the token doesn’t expire, it will have access to the information approved.
While it seems like an ideal system, there is a problem. The most recent OAuth 2.0, released in October 2012, was not designed for mobile apps. This required app developers to implement OAuth on their own, without the guidance on how it should be securely done.
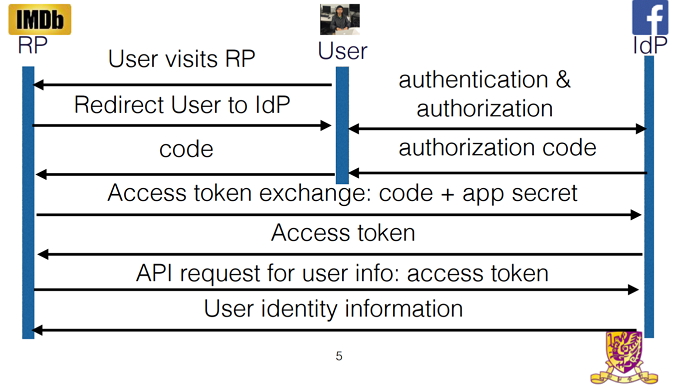
OAuth on websites uses direct communication between the third party and SSO provider’s servers, but mobile apps do not. Instead, they communicate with each other through your mobile device.
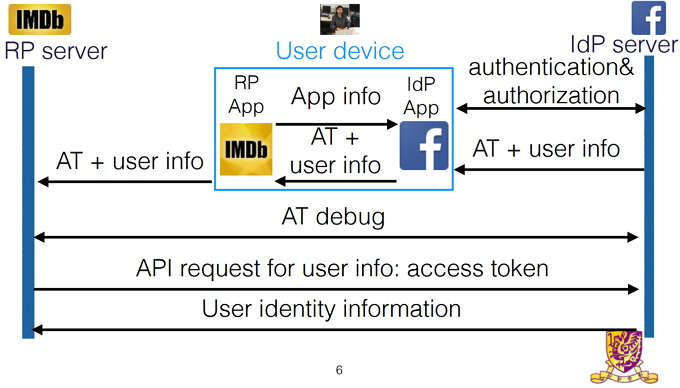
When using OAuth on a website, Facebook delivers the access token and information directly to the third-party servers. The information can be validated before the user logs in or before it accesses any personal data. However, the researchers found that a huge percentage of Android applications are missing this confirmation.
Instead, Facebook’s servers send the access token to the Facebook app. Then, the access token is delivered to the third-party app, which then allows you to log in without verifying with Facebook’s servers that the information is correct.
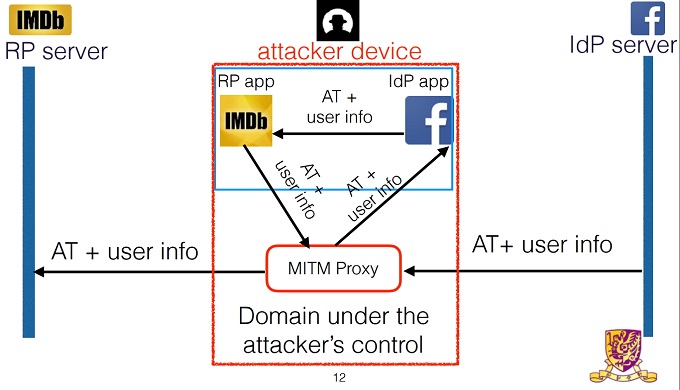
The attacker could then log in as themselves and trigger the OAuth token request. And once Facebook has authorized the token, the hacker can insert themselves in between Facebook’s servers and the app. From there, he could change the user ID on the token to the victim’s ID. The username is made public, leaving few blockades for the attacker. Once the user ID has been changed and authorization is granted, the third-party app will log in under the victim’s account. In the MitM attack, the attacker intercepts and alters data while the two parties believe they are communicating directly with one another.
If an attacker can trick an app into believing it’s you, he gains access to all of the information you store in that service. Here is a list of some of the information that may be exposed on different types of apps:
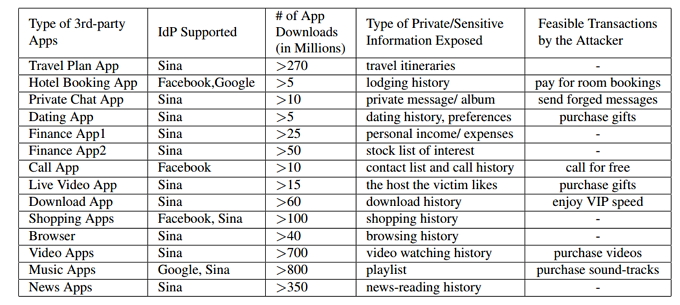
The researchers discovered that 41.21% of the 600 most popular apps that support SSO on the Google Play Store are vulnerable to the MitM attack. While the team conducted their research on Android, they believe it can be replicated on iOS, which would leave millions of apps on the two largest mobile operating systems vulnerable to attack.
Source: MakeUseOf
Advertisement
Learn more about Electronic Products Magazine





