
Machine automation threatens to eliminate any residual human element left in mass surveillance, distilling it down to algorithms and search tools watching for keywords. Depending on where you stand on the issue, the constant scrutiny may feel like an infringement upon your freedom of speech. After all, some studies present correlated NSA leaks with a significant decline in Google Traffic involving terms people may feel will get suspiciously flagged by mass surveillance software.
Whether you’re a law-abiding citizen or otherwise, encryption is paramount in protecting your privacy against shifting values and prying eyes. Below you’ll find a quick guide on how to encrypt your entire digital footprint, more or less, within an hour. Everything recommended is 100% free, and 100% legal. As Quincy Larson from FreeCodeCamp.com puts it, if you bother locking your door at night, then you should bother encrypting.
Tip #1: Use two-factor authentication on your inbox
Chances are, if an attacker — anyone trying to access your data — gets a foothold into your inbox, then they’ll be able to reset your password for anything linked to the email: online bank accounts, credit cards, social media accounts, video game accounts, etc. Two-step verification drastically reduces the likelihood of inbox hacking by acting as a second layer of security when signing in. The process involves receiving a text message on your mobile phone with a unique code that’s inputted in addition to the password, ensuring the account remains protected even with a compromised password. Gmail users can activate their two-factor authentication here .

Tip #2: Encrypt your hard drive
We’ve already discussed hard drive encryption in length. Check out our all-in-one Windows, Mac, Android, and iOS encryption guide.
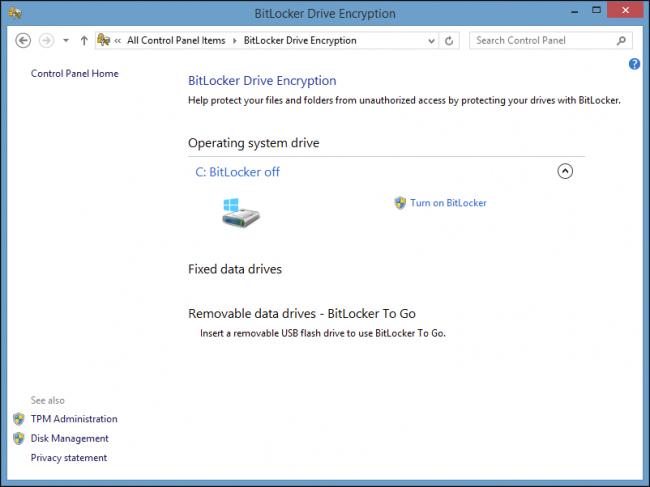
Tip #3 : Enable your phone’s password protection
Just like the Fifth Amendment legally allows you to remain silent to avoid self-incrimination, it also allows you to withhold your password. Thumbprints, on the other hand, are not subject to the same rights; courts can order you to unlock your phone with a thumbprint. And once attackers obtain your thumbprint, they’ll remain in possession of it.
Reinforcing your phone with a password gives attackers only 10 tries to guess the password before it completely locks them out, whereas fingerprints are used indefinitely.
The ten passwords below are among the most common. Make sure yours isn’t one of them.

Tip #4: Use different passwords for each service & remember them with a password manager
The fourth tip may sound incredibly obvious, but most people disregard it, thinking the law of averages will protect them. Guess what? That’s incorrect. It’s very common for password data dumps to contain millions of passwords. Just last September, Yahoo revealed that 500 million of its users’ passwords were compromised in a state-sponsored breach. A few months earlier, hackers seized control of Mark Zuckerberg’s LinkedIn, Twitter, and Pinterest accounts because he used the password “dadada” across all three accounts.
Remembering 10−15 passwords made up of randomly assigned unique characters is impossible, so simplify your life with a password manager. That way, all you need to remember is a single password. Also, ensure that you use an on-screen keyboard whenever you input the manager’s password to hedge against any potential keyloggers that may be hiding about, ready to intercept your keystrokes.
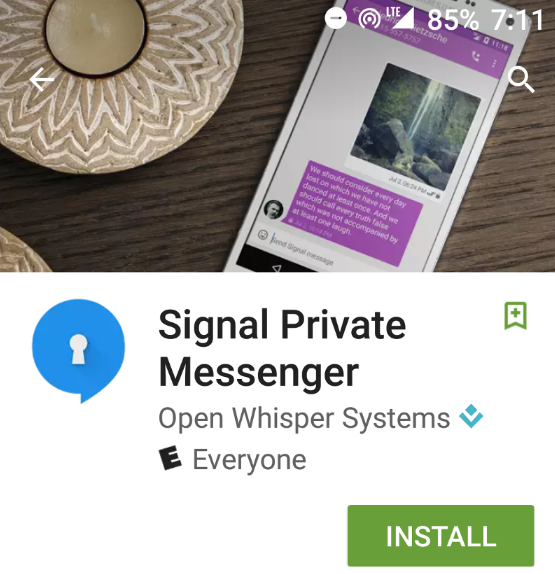
Tip #5: Use encrypted chat services
My encrypted chat app of choice is Whatsapp. The app is encrypted on both ends so Facebook can’t read my conversations; it’s convenient, easy to use, and lets me seamlessly transition between a browser-based plugin and a phone app, depending on my needs.
Others prefer a messaging service called Signal because it received a perfect score from the Electronic Frontier Foundation for having an open-sourced code that’s open to independent review. Signal is free and available for both Android and iOS.
Tip #6: Stop trusting your browser’s incognito mode; it’s not private enough
Even if you trust Chrome’s “Incognito Mode” or Firefox’s “Private Browsing,” network activity remains visible to Internet Service Providers (ISPs); system administrators at school, work, or wherever you get online; and to Google, or whoever made the browsers.
Internet Explorer, Safari, and Opera are no exception.
Tip #7: Install TOR for private browsing
While there’s no guarantee that any system is 100% secure, TOR’s onion-like layering masks network activity significantly more than most. It’s free, open-source, and easy to use. Download it here .
Tip #7.5: Install TOR on your mobile device
A few extra steps are needed to install TOR on Android. First, install Orbot , the free proxy app that lets mobile phone users access the web, instant messaging, and email without being monitored by the telecom provider. Next, install the Orweb browser for anonymous and safe web browsing. Remember, privacy-enriched browsers disable most ads, preventing malicious code hidden in ads from infecting your phone.
Once you’ve installed both apps, open Orbot to connect to the TOR network, and Orweb to start browsing.
Tip #8: Search the web using DuckDuckGo
If TOR seems inconvenient or overly complicated, a simple, yet effective, solution is to replace Google.com with DuckDuckGo or another search engine that doesn’t track you. If you’re not satisfied with DuckDuckGo’s search results, simply insert the “!google” prefix to get encrypted Google search results.

Follow the steps above, and you’ll be in good digital shape. Encryption isn’t only about privacy, but about safety.
Those interested in taking things to the next level — yup, there’s such a thing — may find our idiot-proof email encryption guide useful.
Source: Quincy Larson (FreeCodeCamp) via Medium
Advertisement
Learn more about Electronic Products Magazine





