
Social media and cloud security are very real issues that have pervaded the lives of many users long before the infamous Jennifer Lawrence hacking. In truth, auditing these services to ensure they’re running up to snuff may seem like a daunting task on the surface, but the inconvenience of being hacked is infinitely worse. Compromised social media accounts run the risk of losing valuable content, such as years of accumulated photos, and can also provide hackers with enough personal information to enact identity theft. In truth, nothing on the web is completely safe — as the NSA will attest — but there are precautions that can be taken to significantly reduce the likelihood of being hacked.
1. Enable two-step verification
Although two-step verification may sound like a dance featured in a rap video, it’s actually a dance between your e-mail/mobile device and the log-in page. The process adds an extra layer of security by requiring the input of a security pin in addition to your standard password when logging on to your social media or cloud from an unrecognized device. In the event that a hack steals your password, he or she will be denied access if not in possession of the randomly generated pin.
To enable two-step verification on Facebook, visit the Login Approvals section under Security page of the settings screen. Gmail and Google+ feature this option under the security tab of the Google Account page. Similarly, Twitter’s login verification can also be found under the service’s Security and privacy section of its settings. As for Dropbox, this can be found under Account, Security, and Two-factor authentication.
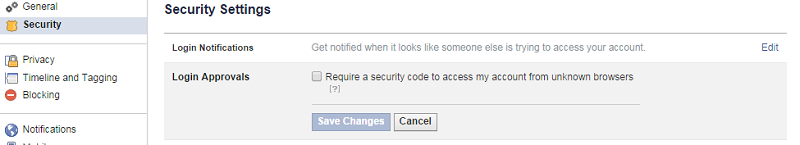
Enabling two-step verification in Facebook
2. Avoid phishing trips
Phishing is one of the most surefire ways to get hacked, but it’s also one of the most avoidable. Avoid all notifications informing you that you’ve won free iPods or that single people of the opposite gender want to meet you. These are blatant sources of malware, and realistically, most folks know this; yet, more refined phishing techniques will disguise malicious sources in e-mails from companies and services we’re very familiar with. For example, customerservice@gmail.com may appears to be authentic, yet official Google e-mails come from @google.com. Other common phishing attacks are browser-based popups that ask you to update said browser or the Adobe version.
Fortunately, most up-to-date browsers and antivirus programs can intercept these attacks, so it’s good practice to manually update these things from their official websites, or in the case of the antivirus program, from the program’s UI. Similarly, it’s good practice to avoid clicking links in e-mails or messengers unless absolutely certain the source is legit.
3. Lock your device
Don’t shy away from password-protecting your mobile devices. It’s minor inconvenience for certain, but according to a study by Trend Micro, 60% of people avoid. Do this especially if you’re the type to fancy work expeditions to the coffee shop.
4. Disconnect third-party apps
It’s a good idea to verify which third-party apps you’ve linked to your Facebook, Twitter, Google, and Instagram over the years and disconnect them. These services can easily function as a backdoor to your account even if the account itself is protected. As long as they retain access, they maintain a record of your password and if their databases were ever hacked, then your credentials will leak.
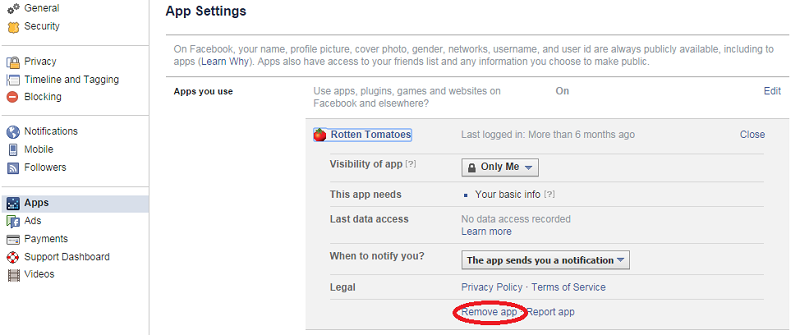
Click the Apps section under “See More Settings” to remove apps connected with Facebook as shown above.
5. Take advantage of the latest security features
If you’re a Dropbox users who shares access across your entire suite of connected devices, it’s a good idea to familiarize yourself with the new Pro Tools. My favorite of these features is the remote wipe, which allows you to remotely disconnect computers/mobile devices from your Dropbox account and automatically delete the files on them. In this way, if your laptop is ever lost, you can simply delete the entire Dropbox virtual storage from the device. Other useful features include password protecting shared folders, setting an expiration date, and password-protecting links shared with trusted users.
Advertisement
Learn more about Electronic Products Magazine





