Mac users typically believe only that Windows clients are prone to viruses. A huge fallacy is that Macs aren’t vulnerable to malware. In 2015, ransomware attacked Mac users, and now, a similar, yet worse, virus has been found.
Deemed OSX/Dok malware, the virus is so powerful that is can take complete control over your machine without you even realizing it. We’ve put together a guide on how to prevent it and how to remove it if you’re a victim.
What OSX is and how it works
The OSX/Dok malware comes as an email attachment in a ZIP file labeled Dokument.zip. If you download it and attempt to open it, the file will say “package is damaged” while, at the same time, copying itself to the /Users/Shared folder with install permission from a signed developer.
From there, the malware replaces your “AppStore” login with itself, thus making the virus run every time your system reboots. Then it notifies you that a security issue was found and an update is required. Before you can update, you need to enter your admin password.
After you enter your password, the malware is granted administrative rights to your entire system, thus having full control. It then alters your network settings in two ways: 1. All traffic is routed through a proxy server, and 2. All traffic can be intercepted. As a result, the virus can impersonate any website using fake security measures. Additionally, the malware uses obfuscation tactics, which bypasses anti-virus software, meaning that users can be infected and not even realize it.
OSX/Dok is noteworthy for two primary reasons. For one, it has the highest potential for damage ever seen on a Mac thus far. And second, it exposed a weakness in Apple’s system of signed developer attacks. It’s also important to note that this is the first widespread Mac-only malware attack.
While Apple revoked the fake developer certificate on May 1, the malware creators immediately resumed under a new developer ID that was also withdrawn. However, viruses from unidentified developers can still be installed, making this malware still an issue.
Steps to remove the OSX/Dok malware
If you realize that your Mac has been infected by OSX/Dok, there are steps that you can take to remove it right at this moment. Before beginning, be sure you Quit or Force Quit all open apps, especially Safari.
1. Remove the proxy server
• To do so, open System preferences
• Click Network
• Select your current internet connection from the left, and then click Advanced (bottom right)
• Click the Proxies tab
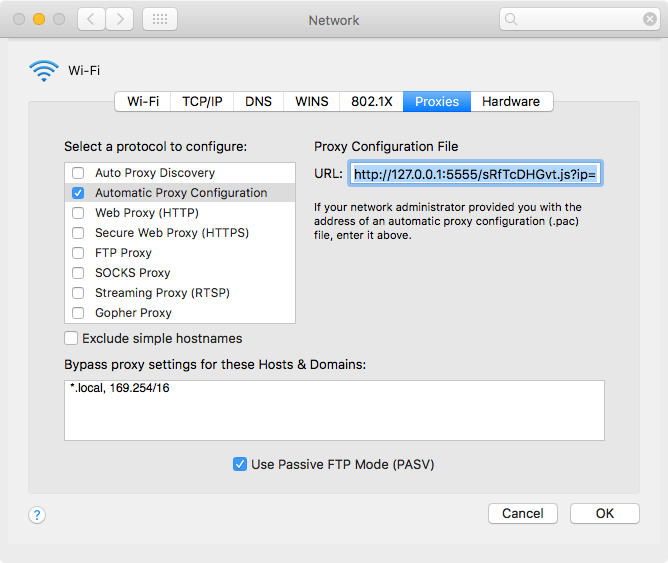
• Select the Automatic Proxy Configuration on the left. Under Proxy Configuration on the right side, delete the URL beginning with http://127.0.0.1:5555… for machines infected.
2. Remove the LaunchAgents
• Be sure that you enable hidden files and folders
• Open Finder
• Navigate to Macintosh HD
• Select Users
• Search for your username
• Go to Library (a hidden folder)
• Find LaunchAgents
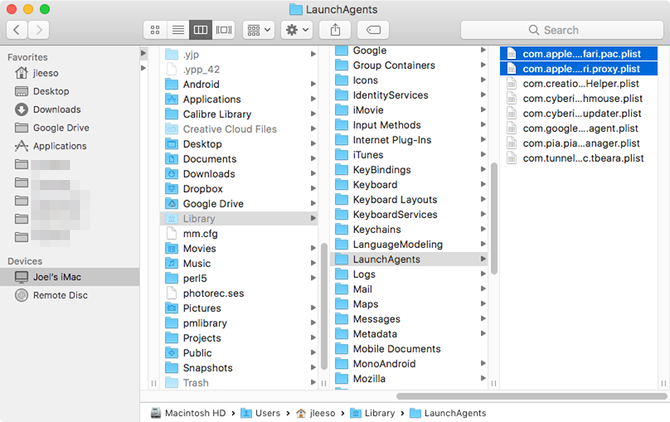
• Delete the file titled com.apple.Safari.proxy.plist
• Delete the file titled com.apple.Safari.pac.plist
3. Delete the fake developer certificate
• Open the Keychain Access utility app (quickest way is via Spotlight)
• Under Category on the left hand side, select Certificates
• On the right, select COMODO RSA Secure Server CA 2, and right-click and Delete
• Confirm by clicking Delete
How to prevent malware from attacking your Mac
A positive side to the OSX/Dok virus (and others similar) is that you can protect yourself against it 100%. Because it arrives through a phishing email, you simply can learn how to spot phishing emails to never fall for them again.
Additionally, it’s useful to learn how to spot dangerous email attachments. As a standard practice, you should never download email attachments unless you were expecting one prior to the email arriving. And remember, just because an email came from a trusted contact does not mean that it’s safe because their email could have been compromised.
Via MakeUseOf
Advertisement
Learn more about Electronic Products Magazine





