Now that we’ve finished discussing the merits of securing Smart Grid enabled devices throughout their entire life cycle, the time has come to highlight how to actually do it. Recall that data encryption methods play a pivotal role in Smart Grid security by protecting information as it enters and exits the communication pipeline. But even more imperative are the encryption keys located on either side of the pipes (on the embedded endpoints) as they encrypt, decrypt, authenticate or validate the data before it actually enters and exits the pipe.
The advent of the Smart Grid has placed a heavy focus on mounting an impenetrable end-to-end encryption defense between data collection devices on the grid, such as smart meters, and the control acquisition systems that analyze and react to the data. Regardless, the best cryptography standards amount to nothing if there is lack of security on the embedded device itself. There is a substantial risk to the entire system if a single encryption key is compromised.
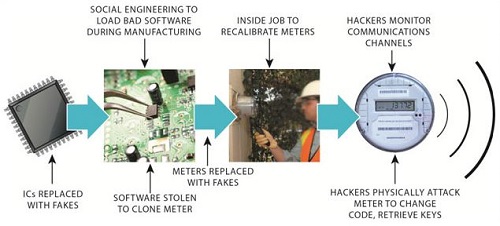
Skilled hackers can cause havoc throughout the life cycle
Securing the life cycle:
Step 1 : Ensure your designs exclusively incorporate microcontrollers and smart grid products procured from an authorized source; the ideal component will be preprogrammed with a customer’s key or certificate to prevent unauthorized access and ensure only the intended customer can program that IC.
Step 2 : Protect your intellectual property from reverse engineering and cloning when sending software to the hardware manufacturer by protecting your IP. Use an encrypted bootloader for your system’s microcontroller unit to decrypt and authenticate the software once its supplied to the chip.
Step 3 : Do not deviate from scheduled code; only run what was planned. Secure bootloaders will protect against unknown signatures by validating the authenticity of the code prior to loading the application.
Step 4 : Ensure that all incoming firmware updates or new configurations are encrypted, signed and delivered from a trusted source.
Step 5 : It is of paramount importance that Encryption keys are not be stored separately from where they will be used. In the event of having a separate secure microcontroller and applications processor, then permanently enclose the keys within the MCU. Storing them on an external EEPROM, electrically erasable programmable read-only memory, opens the avenue of potential exploit.
Step 6 : Internally safeguard security keys within your organization by requiring multiple users to authorize their access and use. The inclusion of development keys will permit engineering to further design security features into the product going forward.
Step 7 : The entire system is as strong as its weakest link; one exploited smart meter can provide access to the entire system. As countermeasure, use unique keys and/or asymmetric cryptographic schemes such as elliptic curve digital signatures. This effectively eliminates the threat of a hacker decapsulating the IC package to launch microprobe memories that seek out keying material.
By diversifying and expanding security efforts beyond IT, to include embedded devices, we elongate the entire life cycle of smart grid enabled devices and protect to very foundation of the grid itself. Maintaining a functional grid is a mutual responsibility.
Visit Maxim Integrated for the complete comprehensible guide.
Advertisement
Learn more about Maxim Integrated





