By Garrett Yamasaki, product marketing manager, industrial automation, Renesas Electronics America Inc.
The widespread push to increase network connectivity, machine productivity, and security for interconnected devices on the factory floor has forced hardware companies to adapt to the increasing advancement toward the industrial internet of things (IIoT), better known as Industry 4.0.
In theory, the ultimate goal of Industry 4.0 is to make networks that are fully interoperable, completely secure, cloud connected, and able to communicate in real time. However, these aims pose some major technology challenges for Industry 4.0 in the near term.
How will Industry 4.0 designers address interoperability, security, and the growing trend for IIoT gateways?
Interoperability of real-time & deterministic networks
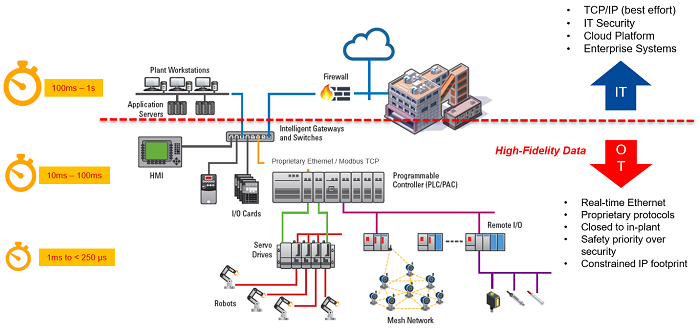
Fig.1: Various time domains of the factory floor.
Within the operational technology (OT) layer of the factory, the number of real-time connected devices is rapidly expanding to meet evolving market needs. Industrial Ethernet protocols such as EtherNET/IP, EtherCAT, and PROFINET provide the real-time control and deterministic latency for automation technology in Industry 4.0 that allows factories to reduce overall latency delays. However, given that both sides of a network need to be interoperable with each other, which protocol do you choose in a market that is constantly changing?
The main challenge is to create a heterogeneous solution capable of handling multiple industrial Ethernet protocols. Using a multi-protocol processor helps to mitigate this issue, but there is a clear need in the convergence of proprietary industrial Ethernet protocols to support interoperability between devices.
Time-sensitive networking (TSN) is a relatively new IEEE 802.1Q standardized technology that allows for new levels of connectivity and optimization. TSN takes standardized Ethernet and adds functionality that includes features like unique time synchronization and deterministic network communication. This allows industrial automation equipment to leverage traditional Ethernet to meet timing and control needs.
Since TSN operates in the data link layer of the OSI model, all other industrial protocols, such as EtherNET/IP, EtherCAT, and PROFINET, can be implemented in the upper layers of the OSI model above TSN. The coexistence of such different protocols in one network is a big advantage of TSN. Ultimately, the goal of TSN is to enable customers to consolidate multiple protocols over a single standardized network. The future of TSN looks promising.
Hardware security
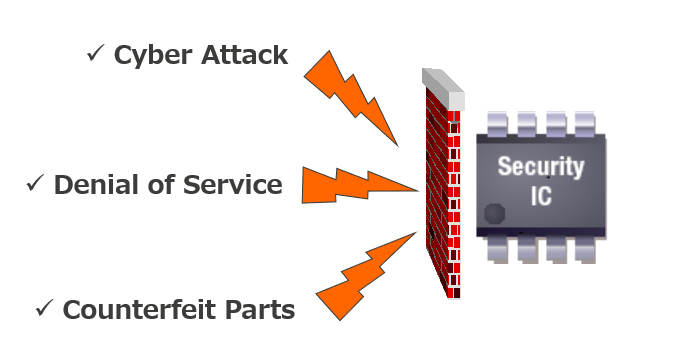
Fig. 2: Secure hardware picture.
A major Industry 4.0 challenge is that devices are not secure from network attacks. From a hardware perspective, there are three main security threats. First, the threat of cyber-attacks can damage entire network systems. Second, denial-of-service attacks can disrupt networks by making them unavailable, due to unauthorized access or tampering from expanded cloud connections. Third, supply chain threats come from damaged or counterfeit parts, which can contain different types of malware.
The International Electrotechnical Commission (IEC) provides security standardization to address and mitigate security vulnerabilities for Industry 4.0. The industrial automation equipment security certifications fall under IEC62443-4.
From a hardware perspective, it is extremely important to protect the starting point of the operation: the microprocessor embedded in the IIoT endpoint. Hardware security that protects the starting point of the operation is called hardware root of trust. There are two main aspects to hardware root of trust — securing a specific area and strengthening it with tamper-resistant technology.
Creating a secure area involves a crypto engine as well as a highly secure key, while tamper-resistant technology entails abnormality detection (circuit voltage, current, frequency, etc.) and different types of secure circuit technology. The benefits are that root of trust significantly reduces attack risk and verifies system integrity.
Among the latest security trends for hardware are implementations of secure boot functionality and security lifecycle management functionality. Secure boot prevents unauthorized program execution by checking in advance whether or not a program has been tampered with. When executing a program stored in the built-in flash or external memory, secure boot checks whether the code is authenticated by security credentials you trust prior to the actual boot process. Ultimately, this prevents another party from loading another operating system or bootloader onto the device.
Security lifecycle management achieves robust and advanced security management at all stages of industrial automation equipment lifecycle — design, manufacturing, operation in the factory line, and disposal. Examples of security lifecycle management are a debugger connection permission function at each stage and a program deletion and key revocation function at the time of disposal. These significantly help to prevent counterfeit products at all stages of the lifecycle.
Intelligent endpoints
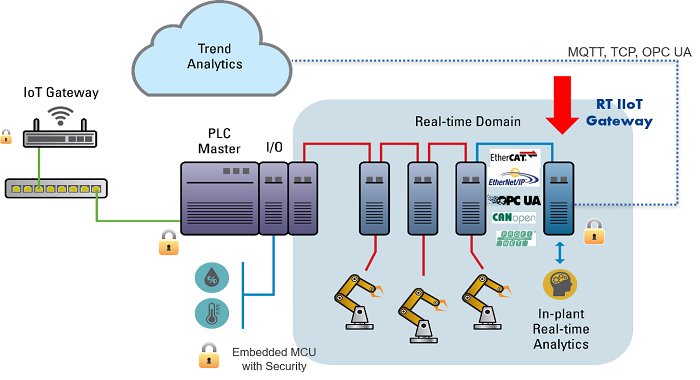
Fig. 3: Industry 4.0 use case for an IIoT gateway.
Another growing trend in Industry 4.0 is the creation of intelligent endpoint nodes by using a real-time IIoT gateway. These intelligent endpoint nodes have an IIoT gateway embedded on-chip so companies can aggregate their data up from the OT layer to the information technology (IT) layer in order to process the data via applications like cloud analytics. There are tremendous benefits to an embedded IoT gateway at an endpoint, such as access to real-time data, analytics on-chip and in the cloud, active command and control, and creation of a secure endpoint.
Since industrial plant systems have different time domains at every level of the factory floor, the best microprocessors to use are those with an application network to bridge the IT level and a real-time network to access the OT level. Having an application core lets you connect to the cloud via newer protocols like OPC UA or MQTT, and a real-time network core allows you to process industrial Ethernet protocols that are deterministic. One such microprocessor with both capabilities is the Renesas RZ/N.
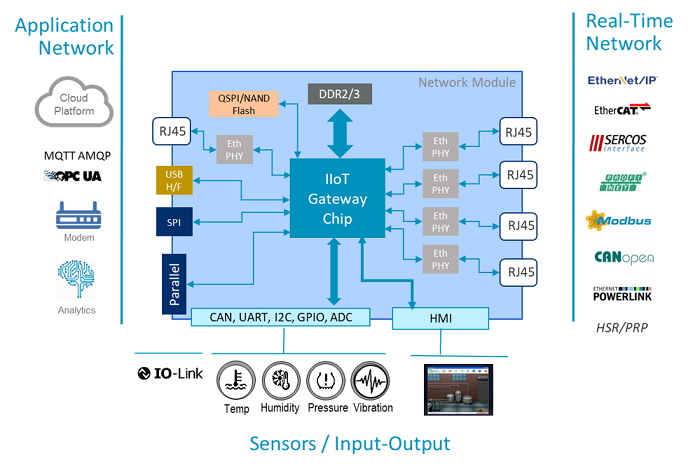
Fig. 4: Building an IIoT use case with a real-time gateway solution.
Industry 4.0 is creating many different technical challenges as industrial automation devices become more interconnected and demand real-time data. The main challenges moving forward will be designing industrial networks to be interoperable, like TSN; increasing hardware security to prevent network attacks; and creating more intelligent endpoint devices that can act as IIoT gateways.
Advertisement
Learn more about Electronic Products MagazineRenesas Electronics America





