LATEST ARTICLES
With so many security cameras installed, and being installed, the need for constant monitoring and detection continues to rise. An abundance of screens with so few people watching often leads to...
Continued breakdowns in password-based security systems have led to increased use of more sophisticated authentication systems by financial institutions and other potential high-value targets of...
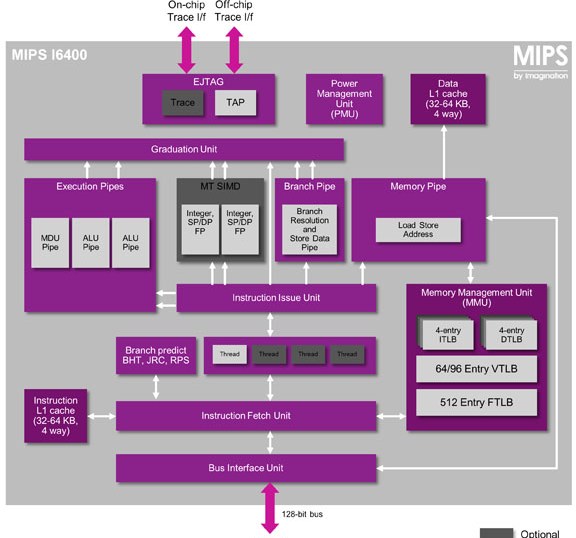
MIPS I6400 CPU IP combines 64-bit architecture, hardware virtualization, coherent...
A low-cost machine vision camera includes a software development...
Social networking sites are beginning to clamp down on the extremist rhetoric being posted by Islamic State militants, but one site is having more difficulty than all the...
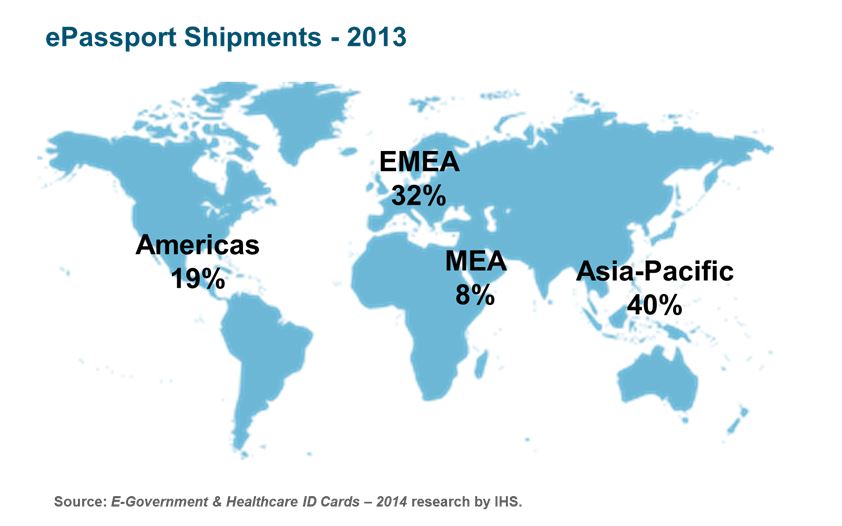
According to research conducted by IHS Technology, ePassports are set to experience weak shipment growth in the years ahead, despite their capability to address security concerns at airports and...