By Gary Elinoff, contributing writer
Almost all of our modern internet-connected devices, smartphones, tablets, and gaming systems have built-in cameras. They are great fun, often quite useful, and life wouldn’t be the same without them. But they also represent a great danger because it is shockingly easy for even unsophisticated actors to gain control of them through malware.
Malware for dummies is a reality
It is absurdly simple for even the most unsophisticated cyber-criminals, or “script kiddies,” to launch attacks with products like NanoCore Rat. RAT stands for Remote Access Trojan, and DigiTrust describes how, for example, a fraudulent Adobe Flash Player update might contain this plague. Once a computer is infected, the cyber-criminals who launched it will have access to anything the web camera sees. Shockingly, instructions for its use are actually available, as of this writing, on YouTube. As pictured below, you can get your own copy on the Dark Web for $10.10. Yes, it’s that simple.
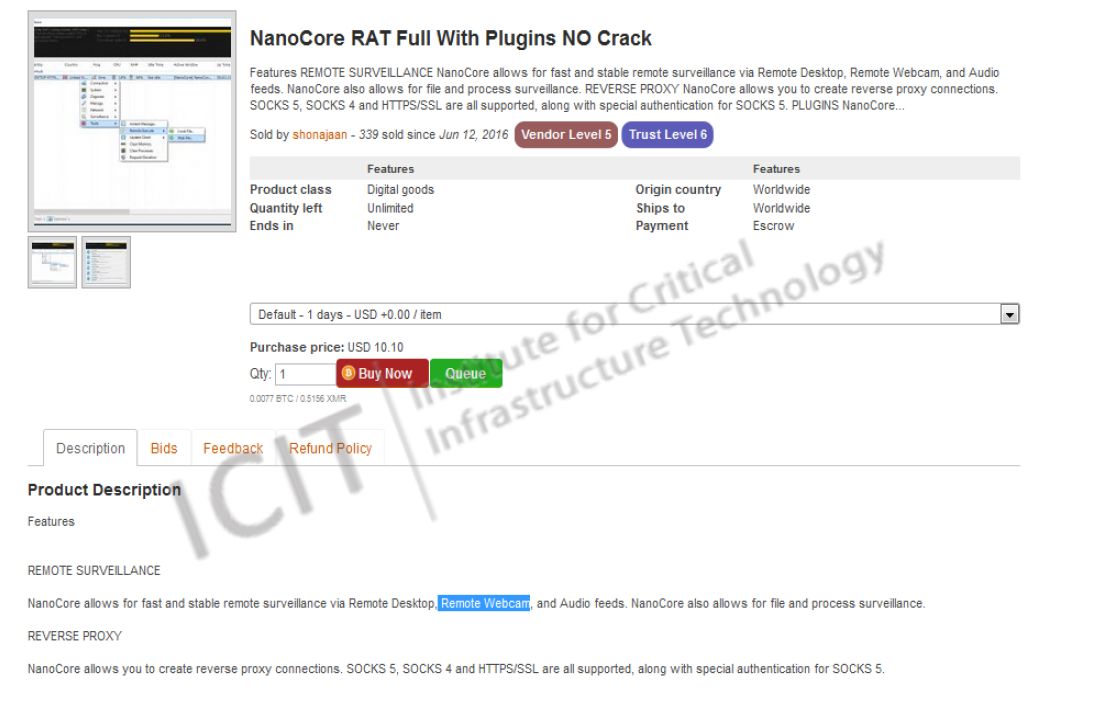
Nanocore RAT. Source: ICIT.
Anything linked to the internet
Anything that communicates over the internet is vulnerable. That includes not only computers and smartphones but also game consoles and TVs. Many of the devices designed for the IoT are also enabled with a camera and microphone, making them vulnerable to the same kinds of attacks that can affect smartphones, but with far more tragic results. Even if there isn’t a train crash or a power plant failure, more localized damage is also a possibility. Even if there is no data to steal, microphones can pick up conversations. Cameras can be turned on, and the LED light that’s supposed to signify that the camera is active can be disabled.
State actors
Sometimes, it’s the good guys who win. Without dropping a bomb or firing a shot, “someone” caused a malware attack that crippled the Iranian centrifuges that were busily at work purifying uranium for that nation’s nascent nuclear weapons program, setting it back for many months or maybe even for years.
Ominously, China’s 13th five-year plan stipulates that the manufacture of anything that gets built in China, including computer chips destined for the U.S. market, is subject to government control. They can use this control to insert backdoor openings into those chips that can be exploited later, often by malware that will target those openings. Cameras and microphones can be turned on to steal images and voices, and data can be directly copied and stolen. Images can be captured without a clue, and important people can be caught in situations that expose them to blackmail. Worse still, devices, documents, and procedures can be exposed to enemies with disastrous results.
In this manner, military as well as industrial secrets are routinely stolen by various governments as well as by others. The process is, by now, so routine that there is a name for it: advanced persistent threats (APT).
Security can’t be an afterthought
It can readily be seen that modern electronic devices are vulnerable to attack by outsiders on many fronts, so security cannot be an afterthought, and designers must adhere to a regime of security by design. But even now, there is one precaution that anyone can take, and that’s simply to cover your web camera when it’s not in use, because if no image is taken, there is no image to steal. As described in an Institute for Critical Infrastructure Technology (ICIT) article, no less a personage than James Comey simply tapes over his devices’ lenses, even if it does appear as “unprofessional” to some.
Cyber Shield Act
Help may be on the way. The Cyber Shield Act now being proposed in Congress is designed to provide information on the net-security of IoT devices, here defined as anything connected to the internet. One of the main goals of the Act, as described in a Cylance blog, is to “drive manufacturers and vendors to compete on the basis of providing better security.” There are difficuties. How does one score security? And the standards will most certainly have to evolve, and just as fast as the threats, to serve any purpose.
The regime that this bill proposes will be entirely voluntary. It’s expected that consumers will vote with their pocketbooks and opt for devices based not only on price and performance, but on security as well. If devices from foreign sources do not permit evaluation, however, manufacturers who wish to participate in the Cyber Shield Act may not be able to buy anything more complicated than a resistor from these quarters. The Act may well turn out to be a boon to U.S. electronics manufacturing as well as to cybersecurity.
Advertisement
Learn more about Electronic Products Magazine





