Last year, the FBI was accused of illegally paying Carnegie Mellon University (CMU) to hack the Tor project. Now, a federal judge in Washington confirms what has always been strongly suspected: experts at CMU’s Software Engineering Institute (SEI) were hired by the federal government to look into hacking Tor in 2014.

But not all the details surrounding the accusation were correct: The research was actually funded by the Department of Defense, not by the FBI as previously suspected. However, judge did indicate that the research was then subpoenaed by federal investigators.
In November of 2015, Tor director Roger Dingledine posted an explanation stating that a number of malicious nodes had been operating on Tor for approximately six months in early to mid-2014. He accused the FBI of paying CMU $1 million to hack the Tor project; the news came out as part of the ongoing case against Brian Farrell, believed to be one of Silk Road’s top administrators. Farrell was arrested in Washington State over a year ago and is scheduled for a trial on April 25, 2016.
U.S. District Judge Richard A. Jones’ issued last week’s court order in response to a sealed motion filed by Farrell’s lawyers for discovery of evidence used to identify the defendant’s IP address. After being identified, Farrell was arrested and charged with conspiracy to distribute cocaine, heroin, and methamphetamine. The document explains that CMU was in fact subpoenaed for the data collected by SEI while running those Tor nodes to test its hack.
The filing also explained why the FBI can legally use the information collected in court. In short, Farrell’s IP address does not violate the Fourth Amendment because Tor users do not expect any privacy. Many have argued that that claim is audacious considering Tor’s primary motive is to provide anonymity. The FBI refutes this, arguing that Tor users must disclose their IP addresses to program nodes before being routed to a destination. These nodes are supposed to be encrypted, but they are run by individuals unknown to the user, which is therefore a “significant risk.”
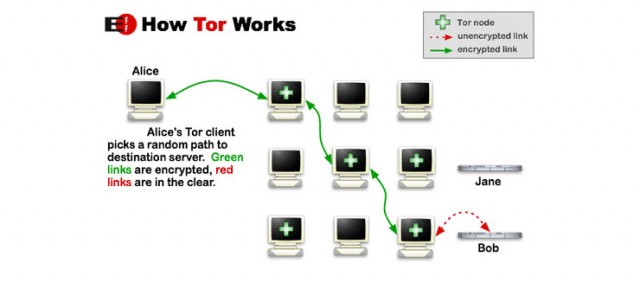
While the information here is based on documents that are part of the public record, sealed ones continue to exist. Farrell’s lawyers are working to get details on the communication between SEI and the government as there may be other documents suggesting the agreement was more of a hack-for-hire than academic research. If the goal was to prove that Tor is hackable, why specifically monitor IP addresses accessing the vendor section of Silk Road?
Source: ExtremeTech
Advertisement
Learn more about Electronic Products Magazine





