
Security researchers at Israel’s Ben Gurion University have developed a proof-of-concept exploit (an attack against a computer with the intention of proving its possibility) that allows them to convert headphones into microphones that would be used to record conversations. Named “Speake(a)r,” the design entails turning headphones connected to a PC into microphones. Then, the PoC can oversee differences in sound quality based on the recording coming from a microphone or headphones. In the security researchers’ initial test, the headphones’ quality of the room’s recorded sound was just as strong as that of an unpowered microphone.
To achieve this, researchers essentially just had to explore the capabilities of the RealTek audio codec chip output that common desktop computers usually have. The PoC’s success means that someone can simply plug headphones into an output-only jack and be susceptible to hackers tuning into their conversations. Besides proving that the sound can be transmitted lengths up to several feet away, researcher Mordecai Guri said, “In addition, we showed that the same setup achieves channel capacity rates close to 1 Kbps in a wide range of frequencies.”
Apparently, nearly anyone willing to tinker with the technology could have reached a similar outcome. “Most of today’s built-in sound cards are to some degree retaskable, which means that they can be used for more than one thing,” wrote Linux sound engineer David Henningsson. “The kernel exposes an interface that makes it possible to retask your tasks, but almost no one seems to use it, or even know about it.”
If this information startles you, there may not even be a way to prevent your conversations from being overheard. An embedded chip doesn’t allow for any prevention, and even if you disable your computer microphone, any computer with a RealTek chip is a potential victim of hacking. Charts displaying the differences in sound quality between random microphones and ones meant for experimentation have similar strength.
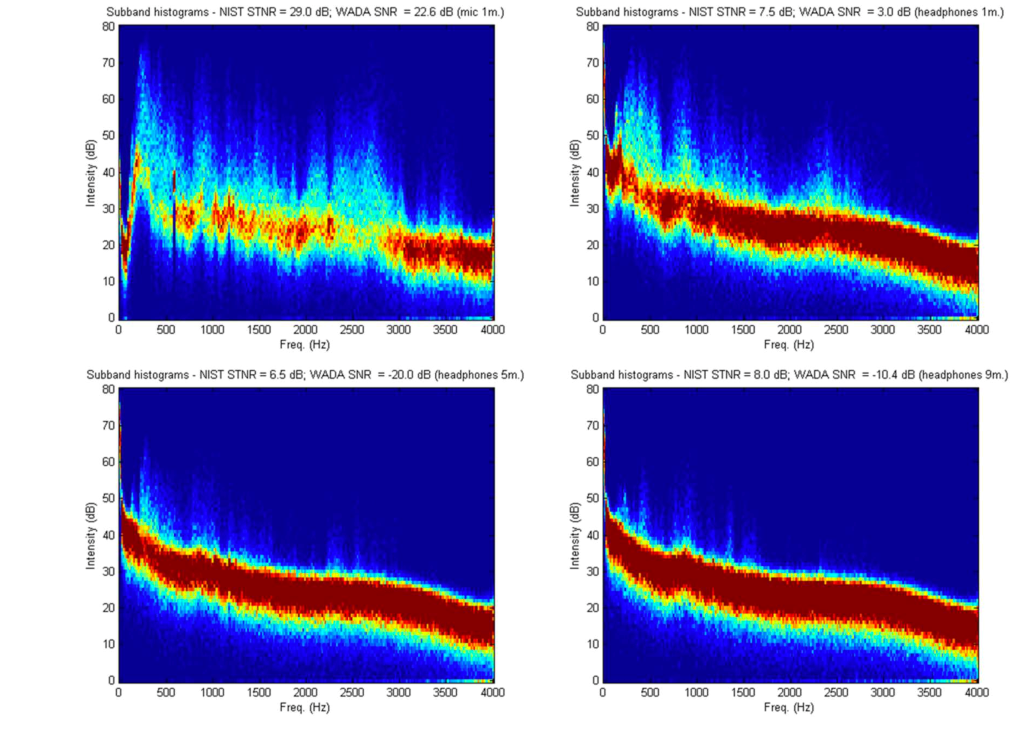
“The fact that headphones and earphones are physically built like microphones, coupled with the fact that an audio port’s role in the PC can be altered programmatically from output to input, creates a vulnerability which can be abused by hackers,” the researchers’ final paper reads. Luckily, Speake(a)r isn’t a finalized design, but the security infringements that the study suggests are definitely concerning.
Sources: TechCrunch, SPEAKE(a)R: Turn Speakers to Microphones for Fun and Profit
Advertisement
Learn more about Electronic Products Magazine





