A group of researchers have successfully developed a new software encryption method referred to as “software obfuscation”; that is, a system designed to encrypt software so that it only allows someone to use a program as intended while preventing any attempts at deciphering the code behind it.
“The real challenge and the great mystery in the field was: Can you actually take a piece of software and encrypt it but still have it be runnable, executable and fully functional,” explained UCLA computer science professor Amit Sahai, who worked with a group of researchers on this project. “It's a question that a lot of companies have been interested in for a long time.”
Previous techniques for obfuscation have, more or less, only acted as a speed bump for hackers trying to reverse-engineer software. The best performing programs would hinder a hacker for a few days at a time. Sahai’s new system, on the other hand, acts as an “iron wall,” making it impossible for someone to reverse-engineer a program without first solving mathematical problems that take hundreds of years to work out on today’s computers.
“You write your software in a nice, reasonable, human-understandable way and then feed that software to our system,” Sahai said, explaining how the obfuscation system is applied to software. “It will output this mathematically transformed piece of software that would be equivalent in functionality, but when you look at it, you would have no idea what it's doing.”
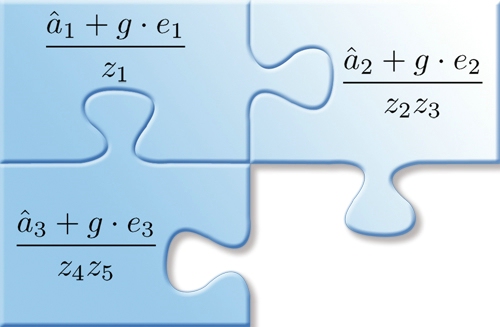
The secret to their program can best be described as a new type of “multilinear jigsaw puzzle”, wherein any unauthorized attempt at figuring out why and how the software works is automatically met with a nonsensical jumble of numbers.
“The real innovation that we have here is a way of transforming software into a kind of mathematical jigsaw puzzle,” Sahai said. “What we're giving you is just math, just numbers, or a sequence of numbers. But it lives in this mathematical structure so that these individual pieces, these sequences of numbers, can only be combined with other numbers in very specified ways.
“You can inspect everything, you can turn it upside-down, you can look at it from different angles and you still won't have any idea what it's doing,” he added. “The only thing you can do with it is put it together the way that it was meant to interlock. If you tried to do anything else — like if you tried to bash this piece and put it in some other way — you'd just end up with garbage.”
Additional purpose
The group’s breakthrough led to another software obfuscation technique called “functional encryption”. It’s meant to replace the sending of encrypted messages. Instead, this technique protects sensitive information by allowing recipients of these messages to only see a particular part of a message.
“Through functional encryption, you only get the specific answer, you don't learn anything else,” Sahai said.
The group said that a good example would be sending a single message to a group of people in such a way that each receiver would receive different information depending on characteristics of that person. Another example: a hospital could share the outcome of treatments with researchers without identifying patient information.
The group’s paper will be presented at the 54th annual IEEE Symposium on Foundations of Computer Science. Sahi has already presented the group’s study at Stanford University and MIT.
Story via: ucla.edu
Advertisement
Learn more about Electronic Products Magazine





