By Brian Santo, contributing writer
Microchip Technology announced a line of ICs that will secure the communications systems in connected vehicles. The idea is to create chips that will pair with the communications system processors that automobile manufacturers are already using and provide the security functionality that those processors lack. Because different automotive companies use different processors (and must also conform to different safety requirements from one geographical market to the next), creating a standard part makes no sense, so Microchip is offering a development kit that vehicle manufacturers can use to design security ICs that suit their specific needs.
If it’s connected, people will try to hack it, and eventually, someone will succeed. Many already have. Meanwhile, automotive manufacturers are rushing headlong to add connected systems to their vehicles. Cars and trucks already sport connected infotainment systems, navigation systems, and advanced driver assistance systems (ADAS). More and more varied connectivity is coming, and there are few extant solutions for securing those systems against hacking attempts.
Conceptually, there aren’t a lot of ways to do that. The most obvious one is to create a minimal number of secure nodes through which vehicle-based connected systems would route.
One approach available to an automotive manufacturer would be to integrate security functionality, requiring a complete redesign of the electronic control unit (ECU). That’s an expensive and time-consuming proposition. Another approach would be to create a security node that would be an add-on. That’s the approach that Microchip is pursuing.
To that end, Microchip has just made available its CryptoAutomotive In-Vehicle Network (IVN) TrustAnchor/Border Security Device (TA/BSD) development kit. The company said that it is the only security-specific automotive tool in the industry.
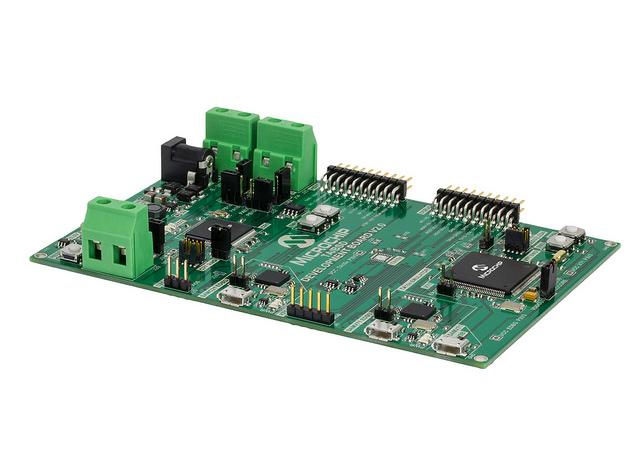
The automotive customer uses Microchip’s development kit to emulate a secure node to complement the microcontroller (MCU) that they are already using. The tool allows manufacturers to configure the node to conform to various specifications and industry standards. Microchip will take the design and implement it as a companion chip, fully programmed and complete with security.
According to the company, the tool demonstrates secure key storage, ECU authentication, hardware-based crypto accelerators, and other cryptographic elements. When used with a host microcontroller, it enables designers to implement functions such as secure boot and controller area network (CAN) message authentication, including conversion of CAN 2.0 messages to CAN Flexible Data rate (CAN-FD), with appended message authentication codes (MACs) when appropriate.
Microchip said that its approach can be adopted with only a modest amount of disruption to the design and manufacturing process.
Nicolas Schieli, Microchip senior manager of strategic and product marketing and application engineering, told Electronic Products in an email exchange, “OEMs around the globe are focused on adding secure boot and CAN message authentication to multiple nodes within the vehicle, typically focused first on ECUs that have a safety rating. Ideally, they would like to make these ECUs resistant to someone remotely changing their firmware without changing anything in their design.”
“However, most existing ECUs are based off of microcontrollers that do not have any cryptographic capability and would not be able to run a trustable firmware validation process in an acceptable amount of time after power-on,” continued Schieli. “Therefore, adding such protection would typically lead to a disruptive change (e.g., changing the kind of microcontroller in their design and consequently rewriting the majority of the firmware). Our proposed approach is much less invasive as it relies on adding a cryptographic companion to the unchanged microcontroller along with limited scope firmware modifications resulting in reduced customer design cost, risk associated with secure firmware development, and reduced time to market.”
“Similarly, CAN message authentication requires support for cryptographic key management including key generation and secure storage of private keys, key agreement, and crypto acceleration for CAN message authentication code calculation, all of which are supported by our crypto companion device,” he added.
Automotive manufacturers are, of course, working on models of their vehicles years in advance. Retrofitting can be a daunting proposition. “The ECU board would have to be modified and the host microcontroller firmware modified to add the necessary security checks,” said Schieli. “The scope of changes being small, it is conceivable to ‘upgrade’ existing ECU designs.”
ADAS systems will get more sophisticated and infotainment services are likely to expand. Soon enough, vehicles will be able to communicate with each other, and on-board systems will end up linking to the cloud.
Asked if it is likely that all connected systems in each vehicle will be able to run through these companion chips, Schieli said, “It is not likely that all connected systems in the car will use this proposed architecture. There will naturally be a mix of solutions (fully upgraded microcontrollers with on-chip cryptographic capabilities and lower-end/lower-cost microcontrollers assisted by crypto companion chips). CAN MAC interoperability of multiple implementations is easily achieved by standardized payload frame format, MAC type, and key agreement scheme, which is defined by each OEM. Our companion solutions are highly configurable to support variances in OEM requirements.”
He added that “some emerging vehicle-to-edge and vehicle-to-vehicle communication standards require more specialized crypto functions, and the proposed devices would not address all of these future requirements.”
Microchip said that the tool can be used with any ECU, architecture, configuration, or bus. The tool provides an online graphical user interface (GUI) program with pre-configured options to simplify and facilitate implementation.
The CryptoAutomotive Security ICs TA/BSD development kit (DM320112) is available today for $250. Schieli said that companion chips are likely to cost about $1 each in volume. The kit can be purchased via microchipDIRECT.
Advertisement
Learn more about Electronic Products Magazine





