By Judith M. Myerson, contributing writer
The Department of Defense’s (DoD’s) Cybersecurity Maturity Model Certification (CMMC), which goes into effect later this year, unifies a set of cybersecurity standards, from Levels 1 to 5, that requires defense contractors to mitigate risk from cyber-threats. In response to increasing cyber-threats and attacks aimed at the defense industrial base (DIB) and the DoD’s supply chain, all contractors will need to comply in order to bid on contracts that contain controlled unclassified information (CUI) and covered defense information (CDI). The DIB sector has more than 300,000 suppliers that support the warfighter as well as research, engineering, development, and other operations of the DoD, according to CMMC documentation.
DoD contractors have used self-assessments, under the Defense Federal Acquisition Regulation Supplement (DFARS) to implement cybersecurity standards. With the new CMMC certification, it now requires third-party assessments to verify compliance in order to bid on certain contracts. Starting in fall 2020, some requests for proposal (RFPs) will state which of the five CMMC levels are required for a particular contract, according to consultancy PwC.
In January 2020, the DoD’s CMMC version 1.0 was approved for public release, followed by CMMC version 1.02 in March. The CMMC Accreditation Body (a nonprofit organization) signed a Memorandum of Understanding with the DoD to begin training third-party CMMC assessors in early May.
CMMC requirements will appear in the request for information (RFI) by June 2020 and RFPs by September 2020. Contractors and subcontractors must pass the audit from certified third-party assessors to verify that they have implemented and complied with specific levels of processes and practices on mitigating risks of cyber-threats from adversaries. They are required to renew a CMMC certificate every three years. If the manufacturers are found to be compromised, a recertification may be required sooner than three years.
The DoD specifies that as long as a subcontractor does not solely produce commercial off-the-shelf (COTS) products, it will need to obtain a CMMC certificate, according to the DoD’s website. The level of the CMMC certificates for subcontractors depends on what types of information they get from a prime contractor.
Five levels
The CMMC model builds on current regulation (DFARS 252.204-7012 ) and is based primarily on NIST Special Publication (SP) 800-171 controls. The model consists of five maturity levels.
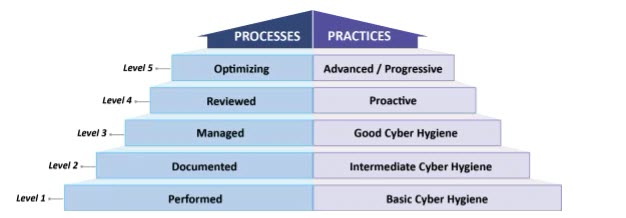
Fig. 1: CMMC levels and descriptions (Image: U.S. Department of Defense, CMMC documentation)
The CMMC starts with basic safeguarding at Level 1, moving to more compliance requirements on protecting CUI at Level 3, and reducing the risk from advanced persistent threats (APTs) at Levels 4 and 5.
The certification ensures that the contractor can adequately protect CUI commensurate with the level of risk. It also ensures that subcontractors in a supply chain of several tiers can provide the protection of CUI flowing down from a prime contractor. Sometimes the relationships of subcontractors between tiers can be non-linear and complex. A prime contractor in one contract could be also a subcontractor for a different contract.
Manufacturers need to be CMMC-certified in order to be reimbursed for the cost of certification. Small manufacturers will find that they can afford to perform practices and processes at the first two maturity levels. However, the costs of assessing project maturity are higher at Level 3 and beyond.
At each level, there is a specific number of practices (a specific technical activity or activities that are required to achieve a specific level of capability within a domain) and processes (specific procedural activity that is required to achieve a capability level). For example, the number of practices and processes that must be assessed at Level 2 are cumulatively less than those at higher levels. Process maturity at Level 1 is not assessed.
The following are examples of what a large manufacturer or supplier must do to comply with CMMC requirements from Level 1 through Level 5. A small manufacturer needs to comply with only the first two levels.
Level 1: A manufacturer must perform basic cyber-hygiene practices, such as using antivirus scanners or limit access to authorized users to protect federal contract information (FCI) residing in the information systems on solicitations, requests for proposals, and contracts. FCI is not intended for public release. The manufacturer must work with the IT/security department or security consultants to ensure it is compliant with all 15 FAR 52.204-21 cybersecurity requirements. All manufacturers are responsible for implementing critical cybersecurity requirements.
Level 2: A manufacturer must document certain intermediate cyber-hygiene practices to protect any CUI through implementation of some security requirements in NIST SP 800-171 Rev 2. Implementation of partial requirements help relieve the high-cost burden on small and mid-sized manufacturers when implementing all security requirements in NIST SP 800-171. The manufacturer must ensure that a policy exists for all activities.
Level 3: A manufacturer must institutionalize, manage, and maintain a plan of implementing good cyber-hygiene practices to increase protection of CUI. All security requirements in NIST SP 800-171 must be met. The DFARS clause 252.204-7012 (to safeguard covered defense information and report cyber-incidents) specifies additional requirements.
Level 4: A manufacturer must review the implemented processes, including security requirements from Draft NIST SP 800-171B, and measure them for the effectiveness of proactive practices of providing the protection of CUI contained in a critical program or high-value assets. The manufacturer must establish additional enhanced practices to detect and respond to changing tactics, techniques, and procedures of APTs. The results of the review should be shared with higher-level management.
Level 5: A manufacturer must use a standardized, documented approach to optimize processes across all applicable organizational units. Advanced, progressive practices must be established to provide more sophisticated capabilities to detect and respond to APTs.
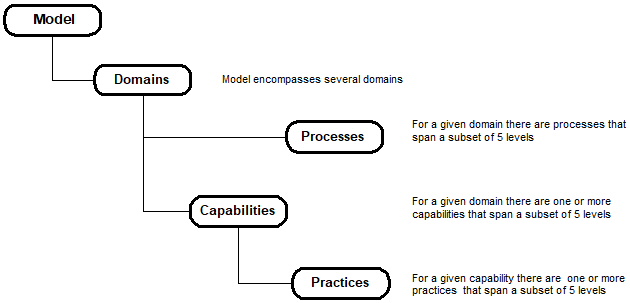
Fig. 2: CMMC model framework (Image: U.S. Department of Defense, CMMC documentation)
The framework
The CMMC model framework organizes processes and cybersecurity best practices into a set of domains. There are 17 domains; each consists of a set of processes and capabilities and, in turn, practices across the five levels. The 43 capabilities associated with the 17 domains are itemized in CMMC v1.02.

Fig. 3: CMMC’s 17 domains (Image: U.S. Department of Defense, CMMC documentation)
As an example, for access control (AC), the manufacturer must be capable of establishing system access requirements, controlling internal system access, controlling remote system access, and limiting data access to authorized users and processes.
Most of the domains are based on the security standards in FIPS 200 (Federal Information Processing Standards Publication 200) and the related security requirement families from NIST SP 800-171. The distribution shows that six domains of AC, audit and accountability (AU), incident response (IR), risk management (RM), system and communications protection (SC), and system and information integrity (SI) make up the majority of all practices.
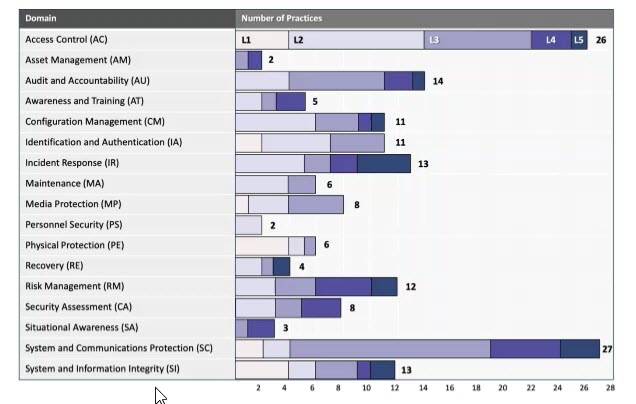
Fig. 4: CMMC practices across domains per level (Image: U.S. DoD, CMMC documentation)
References:
- Cybersecurity Maturity Model Certification (CMMC) Model v1.0, January 31, 2020
- Cybersecurity Maturity Model Certification (CMMC) Model v1.02, March 18, 2020
- CMMC Appendices v1.02, March 18, 2020
- NIST Special Publication 800-171 Revision 2 Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
- Draft NIST Special Publication 800-171B Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations — Enhanced Security Requirements for Critical Programs and High Value Assets
- DFARS 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting (Basic Dec 2019)
- FAR 52.204-21 Basic Safeguarding of Covered Contractor Information Systems
- FIPS 200 Minimum Security Requirements for Federal Information and Information Systems
- CMMC FAQs Office of the Under Secretary of Defense for Acquisition & Sustainment Cybersecurity Maturity Model Certification
- Cybersecurity Maturity Model Certification (CMMC) for defense contractors, PwC U.S.
Advertisement
Learn more about Electronic Products Magazine





