
Have you ever been so affronted by something you read online, that you metaphorically wished you could vanquish the offending website with a botnet army 500,000 units strong? Well now there’s an app for that, and anyone can download it—although we don’t advise it.
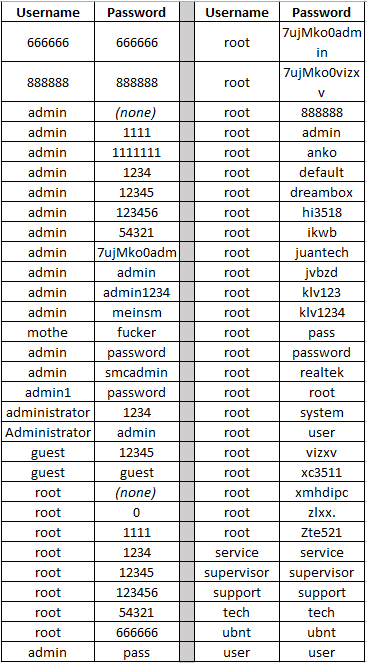
With the public release of the Mirai botnet’s source earlier this month, anyone can download and hijack the more than 500,000 IoT devices that are currently vulnerable to a specific set login of default credentials. The code features 60 default usernames and password combinations backed right in, granting it immediate control over devices protected by factory default or hard-coded usernames and passwords.
Mirai first gained notoriety after flooding the blog of cybersecurity expert Brian Krebs with bandwidth exceeding one terabyte per second (TBps), in what is considered the most massive distributed denial-of-service (DDoS) to date, knocking both the blog and its hosting provider (OVH) offline. The accompanying software continuously scans the Internet for all the vulnerable devices existing at any moment, before spreading its malware like wildfire, creating a collective army of compromised devices that can then be commanded to launch the DDoS attack.
Cybersecurity experts originally traced the highest concentration of afflicted products stemming from the video surveillance equipment produced Dahua Technology; but on closer inspection, intelligence firm Flashpoint observed that most of these items, along with other hacked devices, contain software and hardware manufactured by a single vendor — a Chinese company called XiongMai Technologies.
According to Security Week, XiongMai shipped vulnerable software that has ended up in at least half a million components used by DVR, NVR, and IP camera manufacturers worldwide. Default credentials wouldn’t ordinarily pose a major security risk so long as the device isn’t Internet accessible. In this case, the situation is exacerbated by the fact that the default username and password are hardcoded into the firmware provided by XiongMai, preventing users from even changing should they care. What’s worse is that the firmware also includes an active built-in telnet service, making it easy to access the devices remotely once there’s an Internet connection.
The inability to change a default username and password on an Internet-enabled device is the same as having no password. As long as consumers continue tolerating reckless manufacturer behavior, security will remain an afterthought. In this case, there isn’t much you can do except to avoid products with seedy reputations and make an active effort to employ password best practices. Also, make sure your new password doesn’t coincidence with the 60 hardcoded into Mirai’s source code.
Source: GrahamCluley and SecurityWeek
Advertisement
Learn more about Electronic Products Magazine





