By Majeed Ahmad, contributing writer
In 2019, millions of vehicles are already using safe and enjoyable connected motoring with on-board telematics units, Wi-Fi hotspots, and Bluetooth devices. These vehicles are using connected services ranging from content streaming to location-based assistance and intelligent emergency support to remote software updates of electronic control units (ECUs).
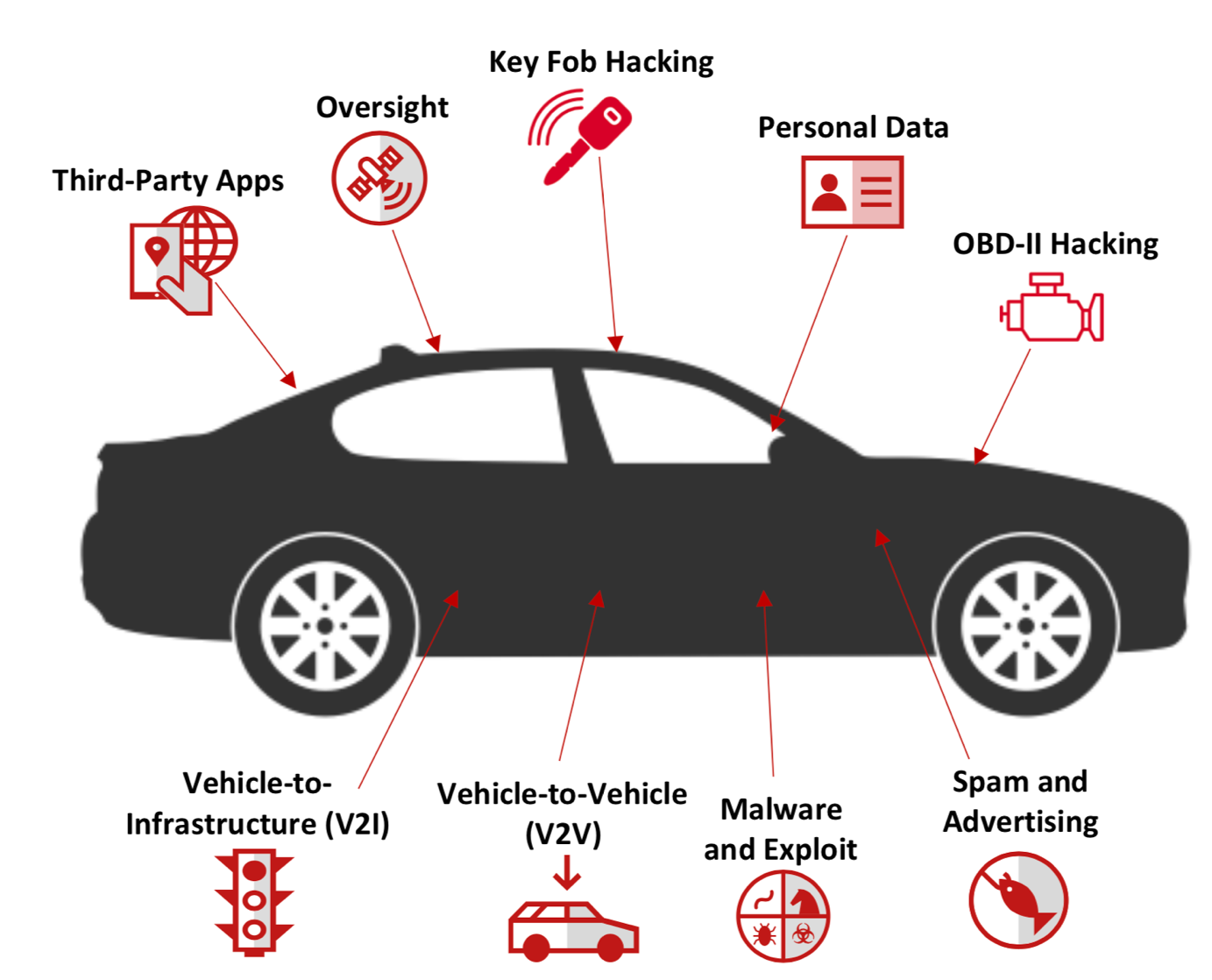
Industry observers forecast that there will be more than 250 million connected vehicles by 2020. But while connected cars represent the next stage in the evolution of driving efficiency and productivity, they are also a hacker’s dream. Therefore, at a time when the connected car ecosystem is quickly evolving, it’s worth pondering how to protect vehicles against cyber-threats.
Here, at this technology crossroads, the role of processors is central in preventing hackers from exploiting the vehicle connections. Here is a look at three major design considerations to offer strong protection against these cyber-attacks. And it begins with vehicle-to-everything (V2X) communications, the technological embodiment of connected cars.
1. Securing V2X processors
The V2X standard, based on dedicated short-range communications (DSRC) technology, is getting ready for deployment after years of development, testing, and prototyping. The DSRC-based V2X standard and its major manifestations like vehicle-to-vehicle (V2V) communications and vehicle-to-infrastructure (V2V) communications rely on public key infrastructure (PKI) for connected car security.
Both on-board units (OBUs) inside vehicles and road-side units (RSUs) outside vehicles are registered to PKI systems using digital signatures and certificates. Here, the security credential management system (SCMS) , mandated by the U.S. Department of Transportation (DOT) in January 2017, is tasked with establishing the PKI for V2X security.
The SCMS provides services to sign and verify the over-the-air (OTA) messages to secure V2V and V2I communications while protecting the anonymity of the vehicle. And it’s becoming a de facto security standard for issuing digital certificates to OBUs in V2X environments.
Security for the connected car demands a multi-layered approach to protect vehicles on multiple fronts. (Image: McAfee)
Take the example of Autotalks, which claims that its Craton2 chipsets are ready for the V2X bandwagon. The Israel-based developer of V2X processors is employing Commsignia’s V2X software stack to interface with SCMS services.
Autotalks has also embedded the cryptographic accelerator from Athena to authenticate incoming packets. That allows its V2X processor to incorporate an outer protection layer that authenticates all messages. Athena’s security processor TeraFire EC Ultra also bolsters cybersecurity by supporting advanced security algorithms. The multiple defense layers in Autotalks’ Craton2 chipset encompass secure boot, secure low-latency signing, line-rate verification of the entire V2X communication link, and secure V2X firewall.
The Craton2 connected car processor from Autotalks is based on a hardware security module (HSM), and that brings us to a fundamental shift in automotive designs: automotive processors incorporating dedicated, built-in security instead of relying on software patches.
2. Hardware-centric security
The current connected car designs lack the dedicated hardware-based security. However, new telematics and connectivity processors like STMicroelectronics’ Telemaco3P are integrating an HSM, which acts as an independent security guard to monitor data exchanges and encrypt and authenticate messages.
For a start, HSM securely checks the authenticity of received messages and any external devices that try to connect. And that’s how it ensures protection against eavesdropping. Next, HSM runs advanced security algorithms, reducing the load on the main CPU significantly.
The Telemaco3P connected car processor is based on a dual-core Arm Cortex-A7 processor, and the HSM is an isolated subsystem within the Telemaco3P, which is based on an Arm Cortex-M3 processor.

STMicro’s Telemaco3P connected car processor supports both symmetrical and asymmetrical cryptography. (Image: STMicroelectronics)
STMicro is positioning the Telemaco3P family of automotive processors as communication gateways, securely linking to infotainment systems as well as to ECUs connected via CAN bus to door controllers, engine or transmission management systems, and body electronics. The processors comply with the automotive functional safety standard, ISO 26261, supporting up to Automotive Safety Integrity Level B (ASIL-B). They also meet the AUTOSAR specification for safeguarding communications across the CAN bus.
Here, it’s worth mentioning that the HSM-based approach can be costly and cumbersome because it mandates the maintenance of a sophisticated database for storing and commissioning the security keys. Therefore, only large outfits can amortize HSM costs while building a high volume of devices or systems.
Another vital consideration in establishing whether a connected car processor is secure enough is the software ecosystem built around it. Take, for instance, the Telemaco3P automotive processors that run on POSIX-compliant operating systems. That, in turn, provides designers with the flexibility to choose the optimum operating system software for a variety of intended use cases.
3. Software complement
Microprocessor vendors like Autotalks and STMicro are joining hands with software houses to bolster security features in the connected car ecosystem. For example, the V2X software stack from Commsignia makes use of the HSM and cybersecurity firewall in the Craton2 chipset to ensure support for SCMS and PKI services.

STMicro is collaborating with automotive software experts ESCRYPT and ETAS to ensure that its connected car processors offer full protection against malicious attacks. (Image: STMicroelectronics)
ST’s Telemaco3P processor has also added another layer of security via Karamba Security’s ECU protection solution “Carwall” that detects modifications and prevents any behavior that falls outside of accepted normal limitations. Carwall enables the hardening of a vehicle´s ECU safety from attempts to manipulate or compromise the commands and hack into the car.
The Telemaco3P processor also integrated the Connectivity Protection software suite from Argus Cyber Security. This allows the connected car processor to prevent malicious software, like viruses, from propagating through the in-vehicle network. The processor adds this software suite on top of the cryptographic and key-generation accelerators, enabling the processor to detect and block cyber-attacks on vehicles in real time.
Next, embedded software firms are joining hands with processor suppliers to boost the security of connected car platforms. Case in point: Green Hills Software is a strategic partner of Autotalks and Commsignia for ensuring that connected car processors can transmit and process secure messages.
The V2X OBU Security Toolkit from Green Hills ensures that the firm’s Integrity RTOS isolates the OBU-related critical software functions from less critical application software so that the basic safety messages (BSMs) in V2X communications are protected against malicious attacks.
BlackBerry is also joining the connected car security fray by enabling SCMS services in automotive embedded systems. The company’s Certicom technology, earlier used to offer PKI solutions in mobile, smart metering, and telematics, is now being deployed in SCMS services for V2X certificate issuance and lifecycle management.
2019: the year of connected cars
Connected car technology represents the next stage in the evolution of vehicle safety and productivity, and it’s finally ready for deployment after almost a decade of work. But it’s still early when it comes to the development of connected car processors and the security features that they offer. This year will show how successful these processors are in preventing hackers from gaining access to a vehicle’s infotainment and telematics systems.
Advertisement





