Security is a big concern across the medical, industrial, automotive, and communications segments. Industries are adopting intelligent networking of machines and processes to optimize processes and flow, erected on connected, smart machines and systems. These systems are susceptible to malicious attacks, unknown software bugs, and remoteness. They can even cause physical security issues and must be protected from unauthorized access or illicit control.
The newest chapter in industrial development, commonly known as the Fourth Industrial Revolution (or Industry 4.0), establishes a new epoch of innovation and development, but not without its own set of hazards and challenges. It defines communications and interconnectivity between systems, networks, machines, and humans, including the internet of things, weaving in new levels of complexity. While the benefits of connectivity include enhanced efficiencies, real-time identification and rectification of defects, predictive maintenance, and improved collaboration between various functions, they can also significantly increase the security vulnerabilities in a smart factory or an automated manufacturing site.
Cybersecurity is no longer confined to a specific operation or system but has propagated to every device on the factory floor or an industrial network. There has been a global rise in security threats to control systems in smart factories, including PLCs, sensors, embedded systems, and industrial IoT devices. Remote management from the cloud also poses risks of physical attacks such as tampering, injection of malicious content, etc.
This article outlines how FPGAs can advance the defense-in-depth approach to developing secure applications necessitated by the demands of the burgeoning growth in IoT and edge computing, driven by the Fourth Industrial Revolution (Figure 1). It describes the role of security in hardware, design, and data while enabling applications to be built upon the three pillars of security: confidentiality, integrity, and authenticity.

Figure 1: The burgeoning growth in IoT and edge computing demands security at every layer on an industrial network. (Source: Adobe Stock)
An infallible security system must necessarily offer three core components:
- Trust: Guarantee that your data source is dependable, authorized, and authenticated.
- Tamper protection: Affirm that your device has not been meddled with in any way.
- Information assurance: The data in your systems is used, processed, and transmitted securely.
Hardware-based security with FPGAs
Employing a single, software-based security approach is insufficient to achieve adequate security levels within the current Industry 4.0 landscape for lack of longevity, programmability, efficient power consumption, form factor, etc. Defense-in-depth security mechanisms must be adopted, fortifying hardware with layers of security.
Today, a majority of security frameworks are software implementations with cryptographic libraries compiled to run on general-purpose controllers or processors. These software implementations expose a more extensive vulnerable space for attacks with numerous potential points of attack, such as operating systems, drivers, software stacks, memories, and soft keys.
Furthermore, software implementations may not be optimized for performance over power and can cause design challenges. Long-term maintenance of these systems with frequent updates to stacks, libraries, etc., throughout the life of an industrial system can also be burdensome and expensive. Principally, the underlying hardware must integrate security into its fabric to prevent static and dynamic reverse-engineering, tampering, and counterfeiting attacks.
Consequently, programmable hardware-based security has emerged as a comprehensive, robust solution for power-efficient industrial IoT and edge applications, especially with FPGAs. In addition to improving the security performance of a system, FPGAs also enhance the security level of an application. An FPGA must integrate key security components in hardware, design, and data to offer a truly robust solution, discussed in the following sections (Figure 2).
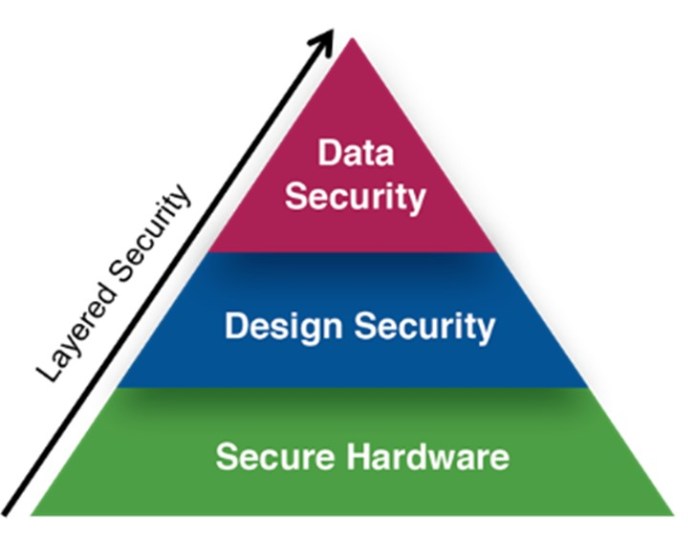
Figure 2: Securing the edge requires a robust, layered approach to security, incorporating hardware, design, and data. (Source: Microchip Technology)
Secure FPGA hardware
The hardware could be attacked pre-deployment or pre-programming at the manufacturing location or during transit through the supply chain. A secure production system, which enables encrypting and provisioning an FPGA in a less trusted manufacturing environment, controlling the number of devices programmed, and auditing the manufacturing process in a cryptographically controlled manner, must be constructed to avoid clones, maliciously programmed FPGAs, and unauthentic parts.
Secure FPGA design
Design security builds on top of a secure hardware platform to provide confidentiality and authenticity to a design while monitoring the environment for physical attacks. A side-channel attack (SCA) can pose a grievous threat to FPGAs that integrate cryptographic systems by corrupting bit streams programmed into the device. An SCA attempts to extract secrets from a chip or a system by measuring or analyzing various physical parameters such as supply current, execution time, and electromagnetic emission. The process for programming or “loading” FPGAs needs to be side-channel–resistant, regardless of whether they are nonvolatile or SRAM FPGAs.
Active monitoring of the device environment is another technique to protect the FPGA design from semi-invasive and invasive attacks. Fluctuations in voltage, temperature, and clock frequency may suggest an attempt to tamper. A tamper-resistant FPGA provides customizable responses to counter the attack, including completely erasing the device and rendering it useless to the attacker.
Secure FPGA data
Finally, FPGAs must provide techniques to secure application data on top of the secure hardware and design, comprising a combination of different methodologies. These include the following:
- A true random-number generator builds secure protocols that meet the NIST standard and offer a source of randomness to generate secret keys for cryptographic operations.
- A root key is generated from a physically unclonable function (PUF). PUFs utilize submicron variations that occur naturally during semiconductor production and give each transistor marginally random electric properties and unique identity. They are analogous to human fingerprints, with no two being alike.
- Secure memory is protected by a secret key.
- A cryptographic function is capable of performing industry-standard asymmetric, symmetric, and hashtag functions.
Conclusion
Industry 4.0 is a progressing revolution, and its widespread adoption relies upon robust end-to-end security solutions. Software-based implementations of security and cryptographic functions are prone to weaknesses and malicious exploitations.
In contrast, today’s hardware-based security solutions leverage FPGAs with advanced secure programmable features that are built into them along with layers of security in hardware, design, and data. This delivers hardware designed to protect customer IP from theft or overbuilding.
Examples of these data-security features include DPA protection to counter SCAs, which is generally a licensed, patented capability. Also important is a secure key management solution based on PUFs and a software-programmable side-channel–resistant cryptoprocessor that supports industry-standard asymmetric, symmetric, and hashtag functions.
Hardware-based solutions pave a path for truly flexible and secure systems. Hardware-based security using FPGAs is emerging as the choice for vital security necessities, chiefly because of the programmability, performance, and significant power advantages it offers. FPGAs that integrate side-channel–resistant cryptographic accelerators include anti-tamper/countermeasures to protect customers’ intellectual property and offer trusted supply chain management for developing secure systems.
Advertisement
Learn more about Microchip Technology





