By Alan Grau, Sectigo VP of IoT/Embedded Solutions
More and more cars are rolling off the lots using key fobs to handle a variety of operations, from simply unlocking the vehicle and remotely starting it up to using a simple button push to have your smart vehicle automatically drive from where it is parked to where you are waiting.
These car fobs can be wonderful — and very convenient — until it all goes bad. That is, until a cyber-crook manages to hack your car’s key fob and attempts to wreak havoc, costing you time, money, and potentially safety.
Automotive key fobs are proving to be easy targets for hackers. Automotive system developers and OEMs need to implement a platform of security technologies to protect vehicles from being stolen, immobilized, or controlled by hackers.
Modern cars are essentially software on wheels — complex and often interrelated collections of automotive systems like braking, power locks, steering, entertainment, window controls, and so on. In addition to those cool capabilities, next-generation cars are adding a plethora of emerging autonomous and ADAS features to this complexity.
And as a result, as the number of electronic control units (ECUs) in vehicles explodes, so does the number of lines of code, thereby presenting a rich field of opportunities for hackers.
Even though key fobs use built-in authentication to control and secure access to the vehicle, they are proving to be easy targets for cyber-criminals looking to attack vehicle systems. In addition to functions mentioned earlier, key fobs can also be used to raise and lower windows, open a sunroof, fold in mirrors, and set seat locations and radio channels. Recent Tesla Model S and Model X key fobs can even be used to initiate automated parking and unparking sequences. Hit “Summon” on the key fob and your Tesla comes to you!
This abundance of interconnected control features makes key fob encryption a very attractive target for cyberattacks. The increased functionality results in more data being transmitted over this interface, which means more data for hackers to intercept and analyze when trying to break the encryption scheme and clone the key fob.
How key fob security works
Most key fobs use a radio frequency identification (RFID) transponder to enable it to communicate to the vehicle. First, the key fob sends encrypted data to the vehicle; this is often a rolling code that allows the vehicle to ID the key fob. The vehicle then decrypts this data and uses the decrypted data to authenticate that this particular key fob should unlock this vehicle.
The authentication is performed by the vehicle immobilizer, an anti-theft system within the car. The car cannot be started until the immobilizer successfully authenticates a key fob to prevent thieves from starting the vehicle.
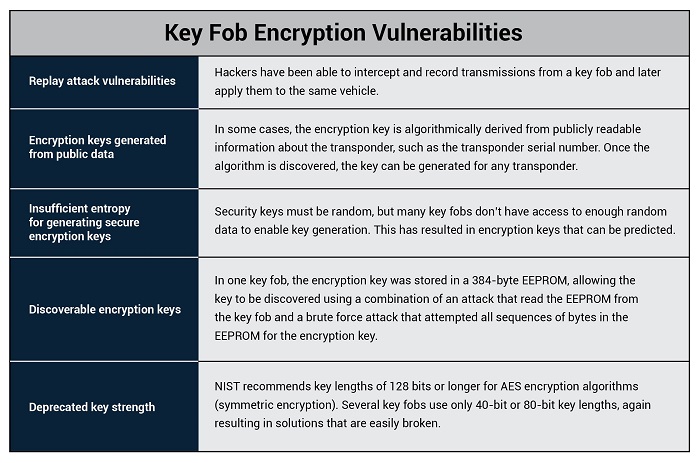
Unfortunately, there is a variety of attacks that have demonstrated how this encryption can be broken, allowing the key fob data to be duplicated by an unauthorized party who can then unlock the vehicle and drive it away.
These attacks defeat the encryption used between the key fob and the immobilizer, resulting in a serious security breach. While there are many key fobs in use, most use similar underlying encryption technologies.
Key fob encryption failures
A Google search will quickly reveal a large number of key fob encryption failures. Because automakers often reuse technology across model years, an attack found in one vehicle may impact other vehicle make and model. Many auto manufacturers even use the same chipsets in their vehicles as other manufacturers, making it even easier for hackers to figure out how to hack the vehicles.
How to make automotive key fobs secure — it starts with hardware
Hardware must be robust enough to support generating the strongest possible encryption algorithms for authentication. To achieve strong security with key fobs, automakers must invest in hardware that will support asymmetric encryption, ensure that proper key lengths and algorithms are selected, and verify that all keys are generated using sufficient entropy (lack of order or predictability) to ensure they are truly random.
Improving key fob encryption — the right software and PKI
An appropriate hardware solution is a first step toward building a secure authentication solution for automotive key fobs. This solution must be paired with an authentication solution that is not easily defeated. Use of asymmetric encryption with certificate-based authentication provides a strong defense against hacking. Certificate-based authentication requires a PKI solution to issues and managing certificates.
Solutions such as Sectigo’s IoT Identity Management platform enable automotive OEMs to quickly and easily implement a PKI solution that is scalable, easily managed, and cost-effective.
The Sectigo IoT Identity Platform is an automated PKI management solution that removes the complexity associated with securing and authenticating connected devices so that businesses can protect their infrastructure in an easy, scalable, cost-effective way. The platform enables enterprises and OEMs to ensure the integrity and identity of their devices and maintain that security by managing certificates over the life cycle of the car and its key fob.
Unique approaches to vehicle authentication
One OEM that is taking a leadership role in proving automotive key fob security is Apple. Available to developers since February 2020, Apple’s iOS release 13.4 includes a new “CarKey API.” This new API works with the Apple Wallet to enable the Apple iPhone to communicate securely with a vehicle’s authentication app.

One way that drivers can prevent key fob hacks is to use a smartphone app to lock and unlock their car.
Because the phone will be authenticating to the vehicle app, the strength of the authentication still depends on the car manufacturer’s implementation of the vehicle app. This approach, however, helps solve the problem introduced in many low-cost key fobs with minimal processing hardware.
An iPhone has the built-in processing power and security capabilities to enable strong authentication without driving up the cost of the key fob. Additionally, Apple’s products have consistently offered strong built-in security and are unlikely to be easily hacked. As you would expect, many other companies are also working on smartphone applications as well as implementing biometric authentication solutions to replace or augment key-fob–based solutions.
Summary
Automobiles are an essential part of our lives. Imagine what could happen if a cyber-terrorist was able to take control of a moving vehicle. Imagine the financial damage that could ensue if a bad actor was to hack an entire fleet of vehicles and prevent them from operating unless a suitable ransom was paid.
When adding security to a complicated device like a car, it is imperative that the system developers ensure the vehicle is resilient to common attacks and utilize a crypto-scheme that is consistent with the protection needs of that device. Using a crypto-algorithm because it is low-cost or convenient is simply not good enough — especially for the next generation of smart, autonomous vehicles.
References: Gizmodo, The Parallax, The Kim Komando Show, CNET, International Association for Cryptologic Research (IACR) Transactions on Cryptographic Hardware and Embedded Systems, and Engadget
About the author
Alan Grau has 30 years of experience in telecommunications and the embedded software marketplace. He is VP of IoT/Embedded Solutions at Sectigo, the world’s largest commercial Certificate Authority and provider of purpose-built, automated PKI solutions. Alan joined Sectigo in May 2019 as part of the company’s acquisition of Icon Labs, a leading provider of security software for IoT and embedded devices, where he was CTO and co-founder, as well as the architect of Icon Labs’ award-winning Floodgate Firewall. He is a frequent industry speaker and blogger and holds multiple patents related to telecommunication and security.
This article was originally published at sister publication EEWeb.
Advertisement
Learn more about Electronic Products Magazine





