The latest security accusation against the United States National Security Agency declares that the agency has been hiding day-zero spying tools within the firmware of hard drives made by Western Digital, Seagate, Toshiba, Samsung and other manufacturers, allowing it to eavesdrop on the majority of the world’s computers, suggests an analysis performed by Kaspersky Labs , the Moscow-based security software manufacturer.
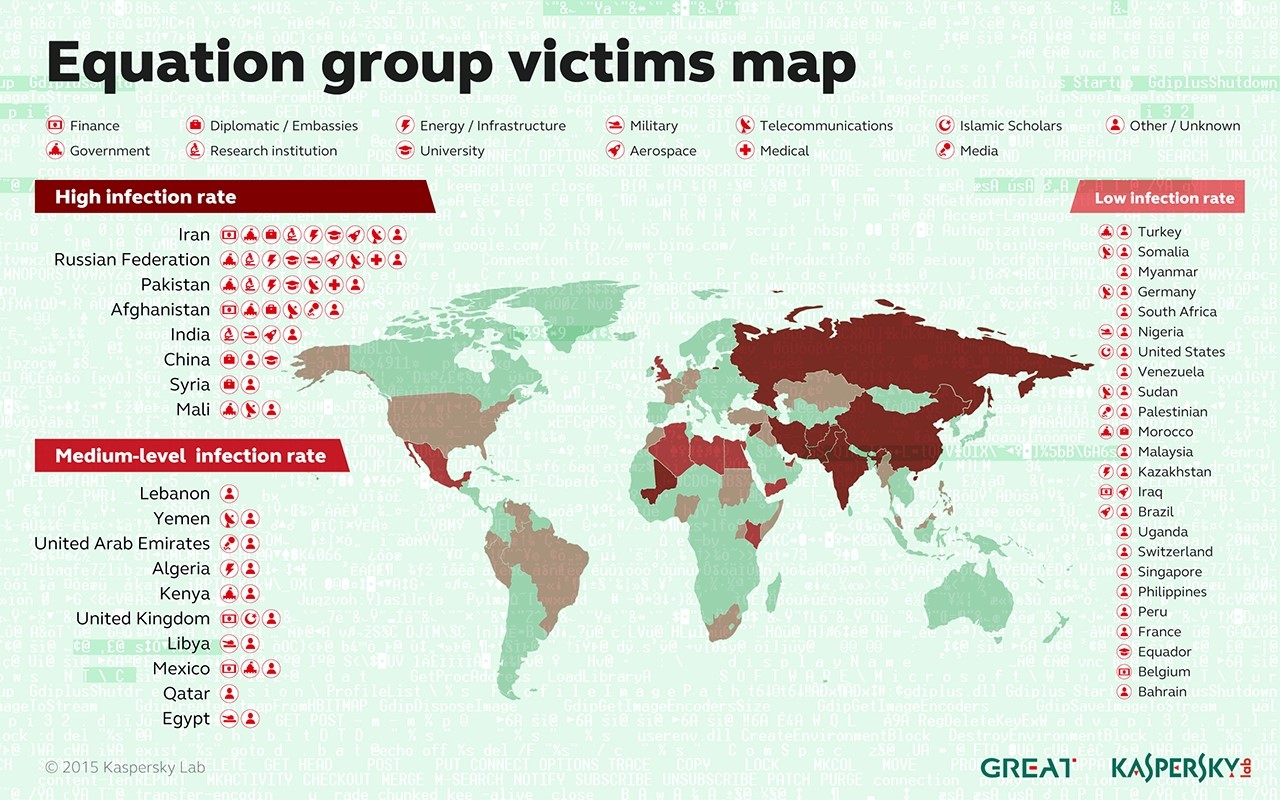
The firm claims it found that tens of thousands of computers across 30 countries were infected with spying programs originating from the same shadowy source, whom they’ve dubbed “The Equation Group.” The infections were primarily concentrated in Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen, and Algeria and in Windows computers belonging to government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists. What’s more, the campaign is said to date back as far as 14 to 20 years.
Kaspersky avoided publically naming the country responsible for the program, but insinuated it was closely linked to Stuxnet, the NSA-led cyber offensive used against Iran’s uranium enrichment facility.
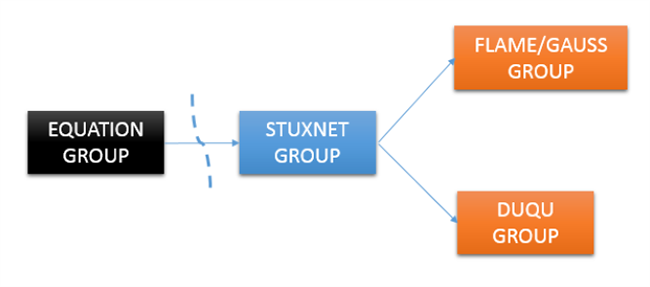
Speaking with Reuters , a former NSA intelligence operative confirmed Kaspersky’s analysis, claiming the agency had developed the means of storing spyware on hard drives, but was unsure of which initiative relied on it. A similar source added that there were authorities within the agency that valued these spying programs as highly as Stuxnet.
According to the analysis, inserting malicious software onto the hard drive’s firmware is a technological breakthrough, and considered by cybersecurity experts as one of the most valuable real estate on a PC for hacking, second only to the BIOS code. As such, the malware discovered by Kaspersky — known only as “nls_933w.dll” — is able to persist and re-infect the targeted computer even as after a hard drive wipe. To make matters worse, the shadow group responsible for the malware must’ve had access to the firmware’s proprietary source code before the hard drives were manufactured.
It’s unclear exactly how the source codes are obtained, but Reuters asserts its inside sources have stated that the NSA would occasionally pose as software developers to trick manufacturers into willingly supplying the code, or could easily obtain a copy when the agency performed code audits on behalf of the Pentagon.
Kaspersky points out that the espionage campaigned is “still-active” and the actors responsible could easily form a remote botnet made of thousands of computers and extract any information they need, considering the majority of hard drives in world-wide use originate from the brands that are allegedly compromised. Nevertheless, the Equation Group has chosen to direct the brunt of its efforts on acquiring data from a few highly desirable foreign targets.
Advertisement
Learn more about Electronic Products Magazine





