By Kelly Casey, Mouser Electronics
Engineers are being asked to connect absolutely everything to a network. The network protocol of choice is Ethernet or one of the myriad variations. Some of these assignments can look great on paper but suffer serious setbacks once realized in the modern world.
The original designers of the Ethernet could not have imagined what we have done with their “baby.” The original intent was to connect various computers together. The data rate was 10 Mbit/sec, which was fast enough for the processors in the computers they were using at the time. The computers were all located in a single room or data center. The cables could be no longer than 10M. The conditions in that data room were controlled so that ESD was a minimal threat and once the computers were wired in, they stayed physically connected for very long periods.
Today, we regularly run Gigabit Ethernet – or at least 100Base-T over hundreds of meters. The buildings we work and live in have miles of cables buried in their walls and ceilings. We use Power over Ethernet (PoE) to power as well as communicate with devices located on rooftops, in kiosks, on light poles, and even radio towers. When the boss tells you to replace the IEEE-488 links in the factory with Ethernet, he/she may not understand the inherent robustness of the IEEE-488 link and the engineering you will need to do to keep your new Ethernet network up and running in an industrial environment. You will need a network circuit protection scheme that will provide trouble-free service for years, and hope it is not a scheme!
To be fair, the vast majority of Ethernet runs require no special protection. The first electrical component behind most RJ-45 Ethernet jacks is an isolation transformer that will provide some protection. This, paired with the ESD protection built into most Ethernet PHY transceiver IC's, provides adequate protection in most home and office environments. The problem is the low percentage of Ethernet ports that are exposed to more serious threats. Long cable runs inside buildings become long-wire antennae that can couple energy from nearby lightning strikes into the network. Those “antennae” are even better at collecting lightning energy if they are run outdoors to kiosks, or up to rooftop or pole-top security cameras.
When reliability issues first surfaced, circuit protection companies developed protection “dongles” that provided additional ESD overvoltage protection. At the time, the dongle plugged into the troubled RJ-45 jack and provided a “protected” RJ-45 jack of its own. These were added to the routers or other equipment that was experiencing failures and were effective up to a point.
As data rates climb and with the advent of PoE, custom solutions are needed and the “one-size-fits-all” dongle approach is often inadequate. PoE brings on even more issues as the DC voltages present can trip the overvoltage protection in dongles designed only for the 2V Ethernet signal. Gigabit data rates can suffer significant data errors due to the capacitive loading of protection schemes designed for 10Base-T or 100Base-T networks.
Unlike 10Base-T, Gigabit Ethernet uses a complex coding scheme (see Figure 1) that requires a very linear channel to successfully propagate long distances. Silicon diodes and thyristors exhibit a non-linear capacitance dependence on the applied voltage.
Gigabit Ethernet also uses a clock rate more than ten times faster than 10-BaseT, which makes the signal more sensitive to the capacitance of the cable and any protection devices used.
Building a robust Ethernet network usually requires a “layered” approach (see Figure 2) consisting of Primary, Secondary and, sometimes, Tertiary layers. Each layer performs a specific task:
Primary Layer: Borrowing technology developed for telecommunications outside plant applications, Gas Discharge Tubes (GDT's), such as the Epcos 871-T83-A90X, or a silicon technology device like the Littelfuse SDP3500Q38CB SIDACtor® Protection Thyristors (which require a bias voltage to linearize their capacitance – easily obtained by using the PoE power voltage) can provide the needed surge-handling capabilities with minimal capacitance loading. The primary layer will let through voltages that are still too high but it does limit the duration of the surge as most of the energy is shunted to ground. For PoE applications, the breakdown voltage of the protection devices must be higher than the PoE power supply voltage. Also, the design engineer must assure that the primary protection system will “delatch” or “reset” while connected to the power supply after the protection is activated. Often, this requires a fold-back current limited PoE supply and protection devices with high holding currents.
Secondary Layer: The isolation transformers not only provide DC isolation to the PHY transceiver IC, their tiny magnetic cores easily saturate and limit the amount of energy that is coupled into the transceiver circuit. However, isolation between the windings must be able to withstand the let-through voltages of the primary layer without breaking down. Keep in mind that a GDT may have a DC breakdown voltage of 90V, but may overshoot to as high as 500V under fast dv/dt lightning surge conditions. The inter-winding capacitance can also couple energy across the isolation barrier, but this is usually quite small compared with the magnetically coupled energy.
Tertiary Layer: The primary and secondary protectors have removed the PoE power and limited the maximum voltage and current to levels that can be managed by a wide range of technologies, many of which borrow technology from ESD protection devices. Some examples:
Differential overvoltage protection, such as that provided by a ST Microelectronics SLVU2.8, is a simple and elegant solution but provides no protection from energy coupled through the transformer inter-winding capacitance. This is often a very acceptable solution.
ON Semiconductor's NUP4114 series offers longitudinal grounded protection for the inter-winding capacitance let-through energy.
Bourns offers TCS (Transient Current Suppressors) DL Series devices that protect by limiting the maximum current in the PHY transceiver inputs and outputs to a safe level rather than the overvoltage scheme of shunting the current around the protected load. These can only handle 40V, so well layered protection is a must for exposed Ethernet.
One additional resource that should be noted is the Bourns library of PortNote™ Solutions. These are simple “starter” solutions that provide some good examples of protection for Ethernet and a host of other communications ports.
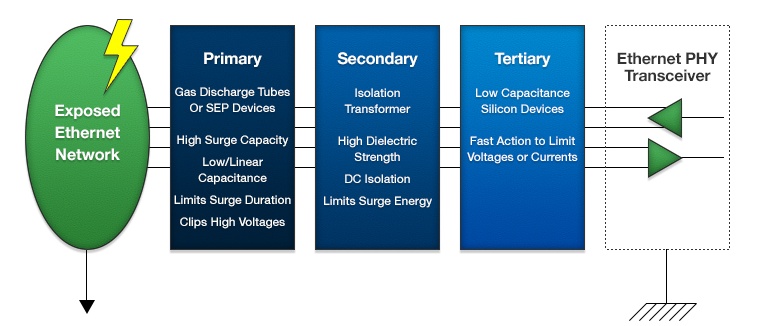
Image via mouser.com.
Today's demanding Ethernet applications go far beyond the scope of the original Ethernet concept – in distances, data rates, and exposure to surge threats. With careful engineering, robust Ethernet networks can be deployed into very challenging environments.
Advertisement
Learn more about Mouser Electronics





