Design engineers are thinking more about security these days, no matter what type of system they are designing. I think of security in two basic flavors — secure communications and making things tamper-proof/theft-proof.
Looking at the communications aspect, I talked with Alan Grau, president of Icon Labs (ww.iconlabs.com), who says there are a number of myths that engineers have about security in embedded systems. He said, “Many EEs think that they are safe if their designs are special purpose and only process packets they are expecting. They reason that since the device is not listening for packets on general-purpose ports like a PC, they are safe from attack.” Alan says that embedded designs are becoming increasingly complex and the argument for security by simplicity is frequently no longer valid.
There are often services provided by the OS that developers are not aware of. “Many systems are designed by large teams or even multiple teams where no one person has a complete view of everything happening on the system and future releases of the design may include additional features not envisioned by the original design group. Some embedded designs are now a used as a platform on which 'apps' developed by third parties can run. In these cases the engineer has little or no control over the possible uses of the device,” Alan said.
Icon Labs provides portable embedded software for device protection, secure access, and network management. One of their products, Floodgate Defender, is a compact firewall appliance providing drop-in protection for networked industrial devices against cyber-attacks.
I asked Bill Joll, president and CEO of ISC8 (www.isc8.com) to comment on security. Let's say we are talking about an industrial-control system — a system connected to the Internet. Engineers really wants to know how much security is enough. They don't want to overdo it, and they don't want have a security problem bringing their system down some time in the future. What would you suggest to this design engineer?
Mr. Joll replied, “Jim, that is a very difficult question, since there are many type of security threats aimed at either exfiltration or sabotage. I would add further that the defense strategy has to be multi-layered. A layered approach is one that protects the perimeter, protects the actual host devices, and also addresses the long, slow, stealthy attacks known as Advanced Persistent Threats. Here at ISC8, the Cyber adAPT product addresses this complex, sophisticated malware type of attack, often launched by a nation state. The design engineer should look at this layered defense, with best-of-breed solutions at each of the layers.”
One component of security is a unique ID, which will help identify or trace a specific device or item (such as an item for a surgical procedure) within a system. The unique ID can be used as a key to help generate random numbers needed by authentication engines in secure authentication applications.
Scott Jones, executive director at Maxim Integrated Products (www.maximintegrated.com), says that “secure authentication ICs are being adopted into a broad range of end equipment. In turn, efforts by hackers to break the authentication security have escalated. In the typical host-peripheral secure authentication application, the host can be the weak point in terms of protecting the authentication key. Maxim Integrated now offers a secure authenticator that uses ECDSA public-key cryptography, which eliminates the need for the host side key protection. With this and our broad portfolio of symmetric-key authentication products, including a key management service for all products, we've put into place total solutions.”
An example from Maxim is the MAXQ1850, a high-performance 32-bit RISC microcontroller for the financial terminal market. Part of their DeepCover embedded security solutions series; the device has security supervisory features, advanced encryption acceleration, and 8 Kbytes of NV SRAM. It features the lowest pin count and smallest footprint available for applications that require a high level of physical and logical security.

The CC2538 system-on-chip targets ZigBee wireless connectivity and features a Cortex-M3 MCU, memory, and hardware acceleration. The 8- × 8-mm QFN56 packaged chip has a 2.4-GHz IEEE 802.15.4 transceiver, 128 to 512 Kbyes of flash, and up to 32-kbytes of RAM. The IC supports ZigBee PRO, ZigBee Smart Energy, and ZigBee Home Automation and lighting standards, along with and 6LoWPAN IPv6 networks, and features a receiver sensitivity of –97 dBm. The chip has an AES-128/256, SHA2 hardware encryption engine, with optional ECC-128/256, and RSA hardware acceleration for secure key exchange. It operates at up to 125ºC, takes only 1.3 μA in standby, and costs under $3 in high volumes.
Texas Instruments www.ti.com
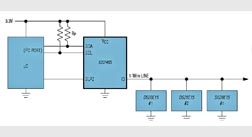
The DS2465 secure coprocessor and the DS28E15/DS28E22/DS28E25 1-Wire secure authenticators form a security chipset that provides the strongest levels of security for authentication of peripherals. Priced from $0.66 each in lots of 1,000, the DS2465 SHA-256 coprocessor receives I2 C data and provides a 1-Wire master output with SHA-256 encryption. The three authenticator chips have 0.5, 2.0, or 4.0 Kbits of EEPROM, a 1-Wire Interface, and additional secure memory for the secret/key. Each authenticator has its own guaranteed unique 64-bit ROM identification number. All devices work over -40° to 85°C and have ±8-kV HBM ESD protection and comprehensive physical tamper protection. (.)
Maxim Integrated www.maximintegrated.com

The SAM4E 32-bit Cortex-M4 based micrcocontroller has up to 1 Mbyte of flash memory, 128 Kbytes of SRAM, and safety and security feature including a AES 256-bit key algorithm. The device has a 10/100 Ethernet IEEE1588 MAC, USB 2.0, and dual CAN ports. The MCU has two 16-bit A/D converters with dual sample and hold, offset and gain error correction, and a programmable-gain amplifier. The 144-lead LFBGA or LQFP-packaged chip has a 12-bit D/A converter, and a four-channel 16-bit PWM. Typical active current is 16 mA at 1.2 V and 120 MHz. and prices start at $5.10 each in lots of 1,000.
Atmel www.atmel.com
Advertisement
Learn more about Atmel, USAIcon LabsMaxim IntegratedTexas Instruments





