By Jim Harrison
Building security into a MCU circuit design has many facets and many types of solutions. Keeping in mind that it’s the system-level security that is certifiable, you will need to start with some necessary hardware in or attached to the microcontroller to have a chance at getting good, and maybe certifiable, security. And, while connected systems have the most critical need for security, even standalone designs may need tamper protection for your important IP.
NXP
The Kinetis K63FN1MOV MCU from NXP fits cost-sensitive applications requiring low-power, USB and 100 Ethernet connectivity, and security. The 120-MHz Cortex-M4-based MCU has 1 Mbyte of flash and 256 Kbytes of SRAM. Security and integrity features include:
- A hardware CRC module
- Tamper detect and secure storage
- A hardware random-number generator
- Hardware encryption supporting DES, 3DES, AES, MD5, SHA-1, and SHA-256 algorithms
- A 128-bit unique ID number for each chip
Run-time power consumption is 250 μA/MH, typical. Static power consumption is 5.8 μA with full state retention and 5-μs wakeup. Tamper detection includes active/passive pin, temperature, clock, and supply voltage monitoring. The chip runs from a 1.71- to 3.6-V supply and operates up to 105°C. The IC has a CAN port, dual 16-bit A/D converters, dual 12-bit D/A converters, a reference, and comparators. It has two eight-channel Flex-Timers (PWM/Motor control), two two-channel FlexTimers (PWM/Quad decoder), and a PLL, an FLL, and multiple internal oscillators.
This chip costs $6.02 ea/10,000. Other NXP devices with the same security features, but without an Ethernet port and with 50-MHz clock speeds have prices as low as $2.45 ea/10,000 (MK11DX128AVLK5).
Texas Instruments
The MSP430 low-power 16-bit MCUs provide embedded security systems that allow designers to prevent, detect and respond to unintended or malicious behavior, including MCU reverse-engineering. The MSP430FR5 and MSP430FR6 versions provide a 256-bit AES accelerator to verify the integrity of data as well as repudiate the credentials of any untrusted participant.
The chips can protect code from external readout attacks using the standard debug or firmware upgrade channels. They provide the means to either secure JTAG using a password or to disable it completely by programming a fuse signature in FRAM. In cases where the JTAG is disabled, access to the device is possible only using bootstrap loader (BSL). The BSL requires a password to read out or receive data. This password is the content of the interrupt vector table — which is a list of addresses or locations for interrupt service routines used in the application. Providing an incorrect password will result in the entire FRAM code area being mass-erased.

Encryption algorithms need secure storage of a key. This can be achieved easily in the MSP430 since you can generate a new key for every session and quickly store it in internal NV FRAM. The chips also have a 128-bit true random seed that can be used to implement a deterministic random-number generator for key creation.
Atmel
Atmel offers the ATAES132A EEPROM crypto element device with secure hardware-based key storage. It provides both authentication and confidential nonvolatile data-storage capabilities. The 32-Kbyte serial EEPROM memory has 16 user zones of 2 Kbytes each. High-security features include:
- AES algorithm with 128-bit Keys
- AES-CCM for authentication
- Message authentication code capability
- Guaranteed unique die serial number
- Secure storage for up to 16 128-bit keys
- Encrypted user memory read and write
- A high-quality FIPS random number generator
- 16 high-endurance monotonic EEPROM counters
- User zone access rights independently configured
- Authentication prior to zone access
- Read/write, encrypted, or read-only user zone options
The chip uses a 10-MHz SPI (Mode 0 and 3) or 1-MHz Standard I2 C Interface and needs a 2.5- to 5.5-V power supply. Authentication is often used in financial transaction products and to verify a product is genuine. It is priced from $0.72 ea/1,000.
Maxim
The MAX32550 DeepCover secure Cortex-M3 based microcontroller from Maxim Integrated offers all of the essential functions for secure mobile payment and pin pads. The IC is based on a Cortex M3 processor with 1 Mbyte of flash, 256 Kbytes of RAM, and 8 Kbytes of battery-backed AES self-encrypted NVSRAM. It includes all of the essential functions of mobile POS terminal:
- AES, DES, and SHA crypto hardware acceleration
- A secure boot loader with public key authentication
- A 256-Bit flip-flop-based battery backed up AES key storage
- A true random-number generator
- A battery-backed RTC
- Environmental and tamper detection circuitry
- A magnetic stripe reader
- A smart card controller with embedded transceiver to support 1.8-, 3.3-, and 5-V cards
- A secure keypad controller
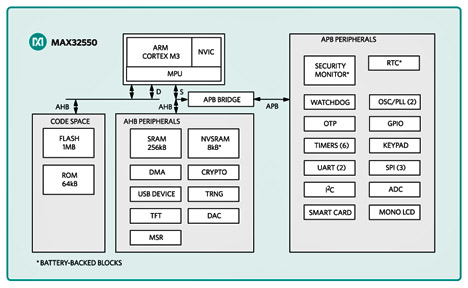
The chip also provides a seamless interface to TFT displays and includes a vast array of peripherals, SPIs, and UARTs.
Inside Secure
You can also obtain security hardware in the form of IP for your SoC design. VaultIP from Inside Secure gives designers a tool to secure IoT devices. The family’s synthesizable IP includes fixed-function cryptographic accelerators, secure lockboxes for key storage, secure policy-based key usage, and secure boot capability. It ships in three flavors targeting different security features and available die areas. The light version, called the VaultIP-100, includes strong device authentication, secure key storage, and a true-random-number generator. The company estimates this version consumes about 50,000 gates, or about 0.05 mm2 in a 40-nm technology.
Advertisement
Learn more about AtmelINSIDE SecureMaxim IntegratedNXP SemiconductorsTexas Instruments





