Real-time location system (RTLS) solutions got their start in government and the military during the 1990s, and have since been adopted in manufacturing, logistics and aerospace, among other applications. More recently they are seeing growing use in healthcare consignment inventory management and retail item tracking. In both applications, RTLS must be implemented with a security-by-design mindset to mitigate cyber risks that threaten to nullify their benefits.
Healthcare industry gets serious about security
RTLS is being deployed in the healthcare industry amid growing attention to cybersecurity. Mandatory cybersecurity regulations and frameworks in U.S. healthcare include the National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure, and the Health Insurance Portability and Accountability Act (HIPAA). Medical device security is also being strengthened with the recent passage of the $1.7 trillion Omnibus Appropriations Bill that includes new rules for submitting applicable medical devices that “meet cybersecurity requirements” as defined in the bill.
As for RTLS solutions in the hospital, one of the most popular applications is tracking the precise location of emergency medical carts and other life-critical assets and controlled substances inside the hospital facilities, in real time. These systems are also used by hospital administrators and their vendors who own and store consignment inventory on the hospital premises until these items are used and invoiced. RTLS solutions enable the two parties to collaborate on the process of identifying, storing and managing these assets (Fig. 1).

Figure 1: In hospital consignment inventory applications, both the supplier and the hospital need maximum asset visibility and the confidence that all automated item ordering and invoicing is secure. (Source: Shutterstock)
For regulatory compliance, all RTLS solutions must be HIPAA compliant across all local sensors, beacons and infrastructure, including cloud servers, and must implement measures such as multi-factor authentication and encrypted backup, storage and VPNs. But healthcare organizations should extend their defenses with a multi-layered security-by-design approach, enabling them to defend against such threats as adversary-in-the-middle (AitM) attacks that exploit the inherent vulnerabilities of wireless communication protocols and open the door to location data tampering.
Retail RTLS requirements
For retailers, RTLS solutions bring new levels of inventory-management visibility to every step of the item’s journey – from the shipper to the receiving dock and all the way to the retail shelf, at the cash register, and after it has been purchased. RTLS also enables retailers to identify a product that has been returned from the customer or retail shelf into the distribution channel. Other benefits include deploying over-the- air firmware updates to electronic products while they are on the retail shelf, and helping retailers conduct product recalls for specifically identified lots.
With an RTLS solution, a retailer can minimize stockouts and improve sales velocity by providing suppliers with real-time item location status information. In applications where cold-chain tracking is required, RTLS solutions can go beyond simply providing serial numbers and expiration dates to include whether certain items are being maintained to temperature and other environmental requirements. Adding environmental sensors to the item tags provides this visibility, from an item’s temperature-controlled distribution and on to its storage on the retail store floor.
Retail RTLS applications are as much at risk from cyberattacks as healthcare applications, and particularly those that target the solution’s communications layer. If not properly designed and deployed, IoT-based technologies like RTLS can be compromised through a variety of attacks.
For instance, the Z-Wave wireless communications protocol was targeted in 2018 by an attack codenamed Z-Shave that relied on tricking two smart devices that were pairing into thinking one of them did not support the latest security features. This forced each to go back to an older security standard and a widely known decryption key. Attackers could later decrypt all traffic exchanged between the two devices and use Z-wave devices as point of entry into the larger network. At the time, it was estimated that this vulnerability could impact over 100 million IoT devices,
More recently, researchers at Black Hat 22 presented zero-day vulnerabilities found in ultra-wideband (UWB) RTLS systems that they said could lead to workers being outside a geo-fencing area when dangerous machinery restarted. They also showed how hackers could tamper with RTLS used for COVID-19 contact tracing to falsify the identities of people coming into contact with COVID-positive personnel.
A holistic security strategy ensures that these kinds of vulnerabilities in a specific wireless protocol are less relevant to the overall security of the system. Whether its Z-wave, UWB, Bluetooth Low Energy (BLE), Wi-Fi or another protocol, an end-to-end, “security by design” approach provides greater assurance that RTLS deployments will be successful, and that data will be safe. Every element of the RTLS system must be trusted, including item tags, communications gateways and multiple layers of software. The entire solution must be cryptographically secure and deliver high-reliability IoT-based, tagged item tracking. This requires a multi-layered, security-by-design approach.
Multi-layered security, by design
Like all IoT-based systems, RTLS solutions need three basic layers of security to protect communication integrity and availability while ensuring that all elements in the system can be trusted. These elements include all tagged items that now must become trusted IoT devices, as well as any other elements connected to the communication system. Figure 2 shows these elements as well as the gateways and servers that comprise a multi-layered security platform.
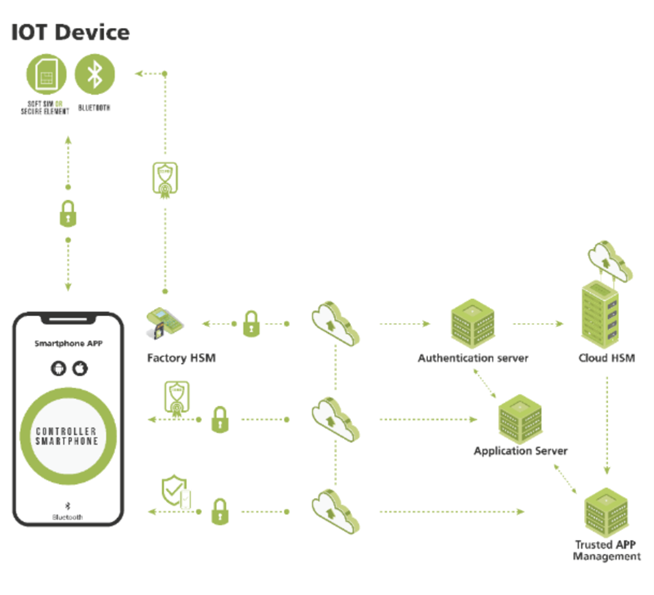
Figure 2: Key components of a multi-layered RTLS security platform include: software and/or hardware gateways to ensure continuous communication availability; a means for protecting the communications channel against malware and wireless channel cybersecurity attacks; and an authentication layer that brings trust to all elements with cryptographic security. (Source: Thirdwayv Inc.)
To ensure continuous communication system availability, a security platform must enable any tagged item to be tracked at any time. This is vital for always knowing the status of all items, all the time. Continuous real-time item location awareness leverages trusted gateways that enable any tagged item to be tracked and located to within a distance of no more than five meters, even inside a multi-thousand-square-foot, multi-level hospital storage area or large retail store. Smartphones can serve not only as command-and-control devices but also software gateways alongside traditional fixed gateways. This improves cost efficiency when implementing this security layer.
A security platform also must protect the system’s communication channel from cybercriminals. This layer is especially important for RTLS applications that use gateways and smartphones. Both are at risk from the vulnerabilities inherent to their Bluetooth, Wi-Fi and other communication links. These protocols mitigate some, but not all, threats. Additional measures are required to fully protect the communications channel between the gateway, smartphone app, tagged item, and the cloud from malware and wireless channel cybersecurity attacks. Otherwise, hackers can access item data via these system elements.
Finally, a security platform must bring trust to each system element through mutual authentication. Adding security at this authentication layer validates the integrity of the user, smartphone app, cloud, item tag, and any associated devices that are connected to the RTLS communication systems. Digital cryptographic identities are applied to all system elements so they can mutually authenticate each other and validate they are allowed to work together. This ensures that hackers cannot gain “root access” to any privileges, while also defending against counterfeiting.
In settings where item authenticity can be life-critical, such as a hospital consignment inventory application, hardware security modules (HSMs) can be used to provision medical devices at the factory. This gives both the medical device and any consumables all necessary cryptographic keys and digital certificates to behave like secure elements in the system. These keys and certificates must be properly managed using an authentication server so that, when RTLS system elements are on-boarded, they’re already pre-programmed to interact only with approved gateways in the field. The security platform also must include an application server containing all required business logic and provide trusted app management to ensure that only privileged smartphone apps may connect with IoT devices.
RTLS solutions with these protections can be built or retrofitted one layer at a time, as needed, with today’s software modules. Deployments can be improved anywhere in their lifecycle, whether to add gateways for improved coverage, or incorporate the use of an HSM for greater security. Today’s third-party software development kits (SDKs) also speed and simplify deployment, whether to add secure smartphone control to the RTLS solution, or extend coverage and accuracy with either software or hardware gateways.
RTLS solutions are of as much interest to hackers as any other IoT application, whether in the hospital or a retail supply chain. A well-designed and properly deployed multi-layered security solution is vital for protecting these systems against today’s cyberthreats.
Advertisement





