In some instances, the term “research” has become a free get-out-jail card, sanctioning all manner of otherwise illegal or questionable experiments. But in other circumstances, term connotes a benevolent activity aimed at benefiting mankind through either innovation or increased awareness. The case of security consultant Mark Burnett happens to be one if the latter. Or so he claimed was his motivation for publishing 10 million passwords alongside their corresponding username.
“I typically decline to share the passwords but for quite some time; I have wanted to provide a clean set of data to share with the world. A carefully-selected set of data provides great insight into user behavior and is valuable for furthering password security,” writes Burnett.
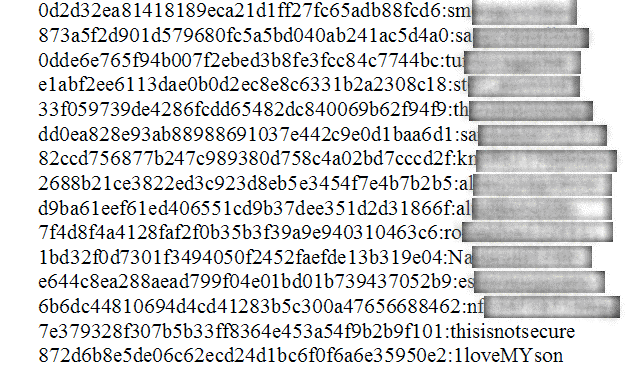
Password caches exposed in hacks are normally devoid of usernames, preventing researchers from studying the possible relationship between the two fields to determine whether a link exists — and if so — to what extent. Burnett fears that while his motivation seeks to further psychological understanding of how and why people choose passwords, his actions may land in the same legal hot pot as writer Barrett Brown, who was sentence to five years in prison in part due to publishing data obtained by hacker groups he investigated. Eventually, most charges against Brown were dropped, but that’s a story for another day.
Nonetheless, Burnett accompanied his post with what appears to be a 2,000 word decree, outlining to the FBI why his actions not illegal. It includes the following message:

Burnett adds that all the data was publicly available at one point, and there’s a possibility it may still be found via search engine. He reassures us that the data has up for to ten years, long enough for most companies to have reset the passwords and notified users. Burnett goes as far as to call any organization that has not reacted to these leaks, in light of being aware of them for the last ten years, “grossly negligent.” Worth noting, is the fact that the data itself has been legally obtained from websites such as haveibeenpwned and pwnedlist — Burnett simply consolidated it within a single source.
“Having said all that, I think this is completely absurd that I have to write an entire article justifying the release of this data out of fear of prosecution or legal harassment. I had wanted to write an article about the data itself but I will have to do that later because I had to write this lame thing trying to convince the FBI not to raid me,” writes Burnett.
As far as password dumps are concerned, Burnett’s package of 10 million is large sample, but pales in comparison to the 80 million social security numbers stolen in the Anthem hack.
Regardless of where you stand, I advise you to visit haveibeenpwned and pwnedlist and run a search on all your emails and/or registered usernames to verify their security status; the sites aggregate the names of a significantly larger sample, including from the top ten leaks listed below.
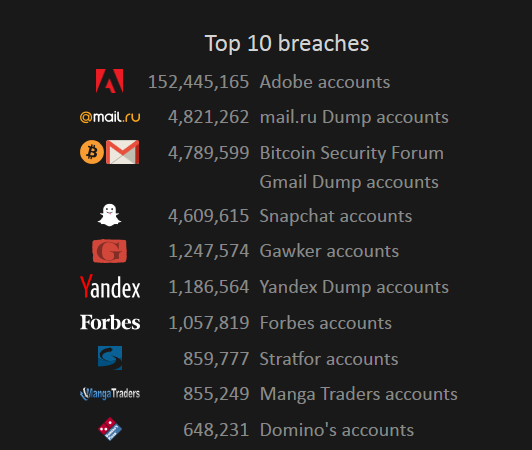
Source: Xato.net
Advertisement
Learn more about Electronic Products Magazine





