BY KRIPASAGAR VENKAT
Smart Grid Applications Manager
Texas Instruments, www.ti.com
Energy meters have gone through several changes with respect to design and functionality in the last decade. A variety of improvements such as lower cost, increased accuracy, tamper detection, less bulk, bigger feature set, no moving parts, digital display, etc. were incorporated in the newer electronic meters. In most developed nations, traditional electronic meters are being replaced by smart energy meters. Smart meters can communicate (one-/two-way) to the outside world through various wired and wireless communication methods. However, looking into the global landscape, the adoption of these improvements is inconsistent due to a lack of investments in grid infrastructure, challenging environments, and prioritized feature sets. For example, most meters are electronic in India, but are far behind the concept of smart meters (two-way communication) due to poor grid conditions. However, India’s meters are the most advanced with respect to tamper detection and protection.
Meter tampering in the broadest sense is an illegal method employed by consumers to gain entry, break in, or some cases break the meter to deplete key functionalities, with the goal of reducing or completely eliminating the cost of energy usage. Traditional electricity meters have no ability to detect or deal with tampering because they only measure energy based on the voltage and current flowing between the inlet and outlet terminals. In such meters, tampering has become very easy and detection is harder. Just as metering and anti-tamper technologies have improved, in parallel, bad consumers continue to get smarter with newer methods to tamper and combat existing anti-tampering schemes.
All electronic meters have a digital processor, microcontroller, microprocessor, or mixed-signal IC that performs energy measurement. These devices, collectively referred to as processors, are very powerful and directly contribute to the robustness of any meter. Energy is the instantaneous product of ac voltage and ac current averaged over time. Separate sensors for voltage and current will convert ac-mains voltage and current to a reduced and acceptable input for analog-to-digital converters (ADCs) processing in the digital domain. Figure 1 shows the signal chain inside an electronic meter from ac inputs to ADCs.
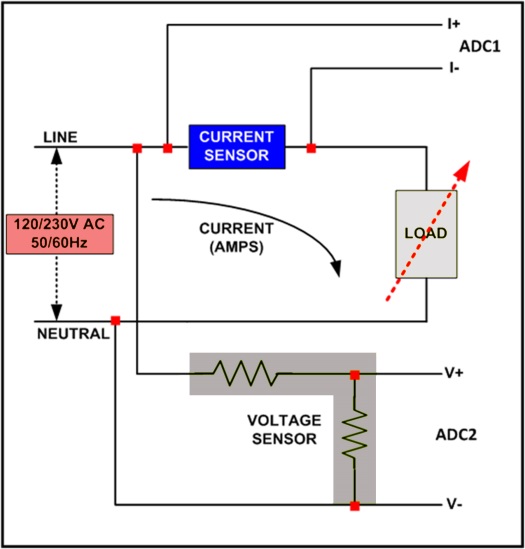
Fig. 1: Front end of an electricity meter.
Sensors are external to the processor and are probably the easiest targets for tampering. It is important to establish that the ac-mains voltage is always fixed, whereas ac current varies with loads being turned on/off. Therefore, voltage sensors are minor targets since they are easily replaced with fixed values in the event of voltage sensor tampering. In comparison, current sensors are the most critical part of an energy measurement system. In any electronic energy meter, current sensors play an important part in energy accuracy, cost, size, and safety. Current sensors can be shunt resistors, current transformers (CT), Rogowski coils, Hall-effect, and others, with choices primarily made based the accuracy requirement of the meter. However, the sensors’ susceptibility to tampering varies and must be understood by metrology engineers worldwide in order to design a tamper-proof meter that can cater to worldwide needs.
Various methods of tampering have been identified, including physical tampering, magnetic interference, bypassing currents, removing wires, adding passives to cause interference, and electroshock technologies (including electrostatic discharge) to break meters. Predictably, single-phase meters used in most residential complexes are targets for tampering and anti-tamper techniques for these are most needed. Physical tampering includes trying to break the case, inserting metal objects to prevent measurement, etc. Magnetic interference is the most common and easiest way to tamper with a meter. Typical sources of magnetic interference are powerful magnets and strong ac fields. Magnetic core-based components in meters such as CTs and transformer-based power supplies saturate in such conditions, resulting in a complete shutdown of metering.
Figure 2 shows magnetic interference using magnets and/or application of strong ac fields to disrupt measurements in a single-phase meter.
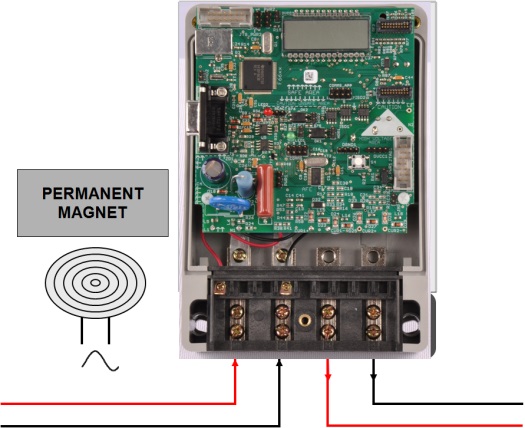
Fig. 2: Magnetic interference applied to an e-meter.
Bypassing current or an unbalanced current condition occurs when a consumer tries to bypass some of the current consumed so the meter reports less usage. This condition can easily go undetected as these changes can be reverted quickly when the meter is due to be read by the utility. Reversing current falls under this category as well, where the meter leads are reversed to negate the true readings so the meter counts backward. Although this maneuver sounds simple, it is a complicated process that involves rewiring the meter. The process is a significant safety risk to the perpetrator and difficult to perform if the meter is sealed and/or installed in a cramped location.
Physical tampering can be eliminated by using costly polycarbonate cases, secondary casing, hermetic sealing, or simply by welding it shut to provide isolation and protection against foreign objects. Magnetic tampering can be prevented by using less magnetics in a meter. Current sensors such as shunt resistors and Rogowski coils have no magnetic elements and are immune to this type of attack. However, shunt resistors have limitations such as reduced accuracy due to self-heating and provide no isolation to the processor. Rogowski coils are coreless in their design, therefore cheaper, smaller, and harder to tamper with. They have to be customized for electricity meters, which increases manufacturing challenges in comparison to shunt resistors or CTs. Simple power supplies like the resistive capacitive type are designed without magnetics to ensure uninterrupted system power during tampering, but lack the capability to source large currents. Hence, electricity meters equipped with processors requiring lower power are a benefit, and are more resilient, during attacks. Bypassing current tampering can be quickly combatted by measuring current in both the line and neutral, and checking for balance. Any significant difference between the two is a clear indication of tampering. However, this calls for an additional sensor and an ADC channel to measure the return current. Two shunt resistors will not work due to high ac voltage between line and neutral applied directly to the processor, whereas two CTs are an option, but with a bigger increase in cost. In such meters, a shunt resistor CT combo would ensure the best accuracy, isolation, balanced cost, and ability to remain tamper resistant.
Reversed current tampering is easily resolved by firmware that indicates negative energy readings. Measures can then be taken to report tampering, make the readings positive and continue or bill the consumer at a very high rate under these conditions.
This article provided a brief outline into the various types of energy meter tampering and methods to detect them. Most of these methods are adaptive over time, and processors must have programmability and flexibility to combat the newest means of tampering. With the introduction of smart e-meters, reporting of tampering is now available in real time. With a remote disconnect feature on these meters, utility companies can now cut off power to bad consumers almost instantly. This is a huge benefit and savings in terms of energy and revenue lost due to tampering, which justifies the roll-out of smart meters for yet another good reason. An important practical conclusion is that microcontrollers with mixed-signal capabilities are best suited to provide systems-on-chip for smart meters. The low-cost, low-power, powerful analog and digital peripherals, and firmware flexibility, allow for robust tamper-free meters.
Advertisement
Learn more about Texas Instruments





