Certified high-assurance operating systems can reduce cost by reducing the time and complexity of certifying devices and by reducing the cost relating to security vulnerabilities and their associated repercussions
BY DAVID KLEIDERMACHER
Green Hill Software
Santa Barbara, CA
http://www.ghs.com
There is no denying the increased worldwide consumer adoption of mobile devices, driven by the emergence of many killer applications, including mobile e-mail, Internet browsing, digital identity and commerce applications, and the enjoyment of multimedia anytime, anywhere.
As the mobile device becomes ubiquitous, however, it presents an attractive target for hackers. Mobile-borne viruses, Trojans, and other subversions have been steadily increasing, exceeding the quantity of such malware found on PCs not so long ago. Mobile phones run complex multimedia operating systems Symbian, Windows Mobile, Linux, iPhone OS containing the same types of vulnerabilities that afflict our laptops, desktops, and servers.
In September 2008, Google released its first Android-based phone, the G1. Google’s Web site touts the platform’s security: “A central design point of the Android security architecture is that no application, by default, has permission to perform any operations that would adversely impact other applications, the operating system, or the user.”
Days after the phone’s release, a well-publicized severe vulnerability was found in the phone’s web browser software. But the G1’s security woes haven’t ended there. In November, hackers discovered a way to install arbitrary programs on the phone, prompting this lament from Google: “We tried really hard to secure Android. This is definitely a big bug. The reason why we consider it a large security issue is because root access on the device breaks our application sandbox.”
To say that technology from Google, Microsoft, Apple, and IBM has done a lot to improve our society would be an understatement of epic proportions. And Google’s phone is undoubtedly an excellent PDA, chock full of bells and whistles. But these systems were simply not designed to meet a high level of assurance. Why should we trust our digital identities and our money with technology that is unable to provide protection against sophisticated attackers?
The good news is that it is possible to use Google Android or any other popular phone operating system and still attain the level of security needed for next-generation applications. This can be accomplished with a platform based on a certified high assurance microkernel, such as Green Hills Software’s Integrity. The microkernel controls the mobile device’s applications microprocessor, memory, and I/O devices, and a secure virtualization layer hosts one or more instances of “guest” mobile operating systems, such as Linux or Windows Mobile. The platform also includes a software development kit (SDK) that enables device manufacturers and service providers to incorporate secure applications and manage critical data that cannot be compromised regardless of the state of the guest environments.
Evaluating security
ISO/IEC 15408, more commonly known as the Common Criteria, is the international standard for evaluating security.
Common operating environments, such as Windows, Linux (upon which Android is based), and VMware come in at EAL 4, which according to the Common Criteria, “is the highest level at which it is likely to be economically feasible to retrofit an existing product line.” The vast body of enterprise software in the world simply has not had security designed in from the beginning.
Table 1. Common criteria security levels
The world has become accustomed to the fail-first, patch-later mentality of insecure software. The security specifications of EAL 4 products admit that they are not appropriate when “protection is required against determined attempts by hostile and well funded attackers.” Thus, our mobile devices are open to compromise by determined individuals, corporations, and nation states that wish to infiltrate our networks and devices with nefarious intent.
What is ‘secure’?
Recently, an operating system was certified to EAL 6+, the highest level of assurance under Common Criteria ever achieved for an operating system or hypervisor technology. The product evaluation and certification was performed under the auspices of a U.S. government program to protect national secrets in environments with high risk of exposure to hostile, well-funded attackers. The certification was performed on a Power Architecture-based processor, although the certification includes provision for maintaining assurance across ports to other hardware platforms.
Requirements include an extremely rigorous design, development, and testing process, continuous validation of security-relevant hardware during execution, secure maintenance and delivery mechanisms, and formal methods to mathematically prove the system security policies. Finally, the certification required withstanding penetration testing by the U.S. National Security Agency’s expert hackers who have access to the source code.
This security evaluation milestone represents independent affirmation that it is indeed possible to create a system that is hacker proof. It also may be reassuring to know that the same operating system that controls critical mission systems, displays, communication/navigation/identification, and cryptographic security systems aboard the latest fighter jets is managing and securing the critical information and applications on the mobile device.
Leveraging security in the mobile device
A platform for secure mobile devices leverages the high assurance protection of a secure operating system, embedded virtualization technology, and the latest security hardware capabilities, including Trusted Platform Modules (TPM). Promisingly, hardware virtualization acceleration is now making its way from higher end computing systems (e.g. servers) into embedded and mobile devices. For example, the Power Architecture 2.06 ISA’s embedded profile includes a hypervisor mode and related virtualization extensions. Freescale Semiconductor delivered the first 2.06-compliant and virtualization-enabled product, the P4080, a member of Freescale’s QorIQ processor family. Hardware virtualization support enables virtualization software to host guest operating systems with little or no modification while achieving excellent performance.
Regardless of the hardware platform, typical software virtualization solutions suffer from the same scope of defects and vulnerabilities that plague general purpose operating systems. Furthermore, hypervisors have been shown to actually reduce platform security due to attacks like Blue Pill and other virtual machine “escapes” that put all operating systems, applications, and data on a computer at risk.
A better approach avoids all of these problems by using proven separation between virtual machines and by ensuring that the virtualization software itself is unable to circumvent the security policies of the certified operating system. In addition, such a platform supports the development and deployment of high assurance secure applications that cannot be trusted to run on top of guest operating systems. A software development kit (SDK) is provided to enable OEMs, anti-virus and other security software vendors, and end users to incorporate trusted, application-specific software.
With this platform, device manufacturers and service providers can leverage traditional operating systems and software, such as Windows Mobile, Symbian, and Linux, while guaranteeing the integrity, availability, and confidentiality of critical applications and information (see Fig. 1 ).
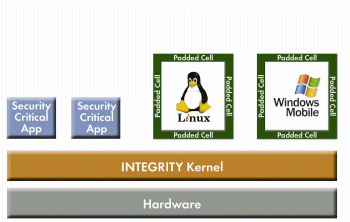
Fig. 1. Secure operating system, with embedded virtualization technology, supports one or more “guest” mobile operating systems alongside security-critical applications and data.
Mobile virtual appliances
A few years ago, the “Metal Gear” Trojan infected Symbian-based mobile phones. Metal Gear did not merely damage the infected phone. The malware disabled the antivirus software running on Symbian and then wormed itself (for example, via Bluetooth) to other phones.
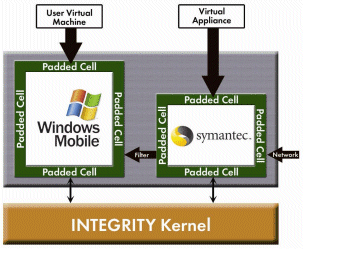
Fig. 2. Secure mobile virtual appliances.
There is a simple solution to this type of malware. Security applications, such as the antivirus program, can be placed into a dedicated virtual machine so that it cannot be affected by software running on the user’s primary operating system (see Fig. 2 ). Access to the antivirus program is controlled by a secure channel governed by the certified kernel. Many other types of security software applications can be protected and hardened in this manner.
Mobile security applications
We bring our cell phones wherever we go. How awesome would it be if our cell phone also acted as the key to our automobile, a smart card for safe Internet banking, our virtual credit card for retail payments, our ticket for public transportation, and our driver’s license and/or passport? There is a compelling world of personal digital convenience awaiting us. The lack of a high-security operating environment, however, precludes these applications from reaching the level of trust that consumer’s demand. High assurance secure platform technology enables this level of trust. Furthermore, security applications can be incorporated alongside the familiar mobile multimedia operating system on a single SoC, saving precious power and production cost.
Mobile device certification
As mobile devices are increasingly used for security-critical functions, such as mobile banking, the certification time and cost weigh heavily on developers who must convince banks and certification authorities that transactions and private information can be secured at the mobile endpoint.
By providing a separate compartment for security-critical processing and information, protected memory operating systems and virtualization can reduce the cost and time to market for mobile devices. With secure partitioning, the bank (or certification authority) can limit certification to the security-critical applications and avoid the complexity (if not infeasibility) of certifying the multimedia phone environment. For example, a bank may require certification of the cryptographic functionality used to authenticate and encrypt banking transaction messages, but the bank will not care about certifying a multimedia DRM system, that while critical for the overall phone, is not used in banking transactions and guaranteed by the secure operating system not to interfere.
Secure mobile Internet browsing
With secure virtualization technology, the mobile device can host multiple instances of mobile operating systems. For example, the device can incorporate one instance of Windows Mobile that the consumer uses for the phone function, office e-mail, and other “critical” applications. A second instance of Windows Mobile can be used specifically for browsing the Internet. No matter how badly the Internet instance is compromised with viruses and Trojans, the malware cannot affect the user’s critical instance. The only way for files to be moved from the Internet domain to the critical user domain is by using a secure cut and paste mechanism that requires human user interaction and cannot be spoofed or commandeered. A simple key sequence or icon is used to switch between the two Windows Mobile interfaces.
Secure virtualization can also be used to provide a smart phone with multiple operating system personalities, enabling service providers, phone manufacturers, and consumers to provide and enjoy a choice of environments on a single device. Furthermore, by virtualizing the user environment, personas (personal data, settings, etc.) can be easily migrated across devices, in much the same way that virtual machines are migrated for service provisioning in the data center.
Toward a secure mobile world
In a recent article discussing the growth of smart phones in corporate environments, USA Today stated that “mobile devices represent the most porous piece of the IT infrastructure.” The same problems that plague desktops and servers are afflicting mobile devices. Billions of dollars, national secrets, medical records, and human lives have been lost as a direct result of software security failures. Due to recent technological and process advances, truly secure solutions, finally, exist.
Proven, certified development process and technologies enable breakthroughs for many of the world’s long unresolved security problems, including the ability to safely browse the Internet and use e-mail, trust the execution of antivirus and other firewall and network filtering solutions, protect sensitive personal and medical records from compromise, and guarantee the authenticity and integrity of cash withdrawals, wire transfers, point-of-sale transactions, and other high-value financial enterprises. And certified high-assurance operating systems can reduce cost by reducing the time and complexity of performing device certifications and by reducing the cost relating to security vulnerabilities and their associated repercussions. ■
Advertisement
Learn more about Green Hills Software





