
By Maximilian Teodorescu
On Tuesday, March 7, 2017, WikiLeaks published the first in a series of data dumps encompassing the largest number of confidential documents ever leaked from the intelligence community. Code-named “Vault 7 ,” the preliminary leak contains 8,761 documents and files originating from the CIA, confirming what many have long suspected: Yes, the CIA really can listen in on your phone calls.
Vault 7 presents an in-depth look at the CIA's cyber-weapon arsenal and how it uses these tools to gain surveillance capabilities over a host of end-user mobile devices and desktop computers. Internal documents reveal that the agency uses zero-day bugs, malware, and Trojan to infiltrate mobile devices and record keystrokes, circumventing encryption altogether — meaning that the CIA can gain access before that encryption has even taken place. So why does this matter to you if “you've got nothing to hide?”
Whether you've followed the story in its entirety or gleaned piecemeal information here and there, there's a high likelihood that you’ve got unanswered questions. To help make sense of it all and sort through the disinformation, we're bringing you all of the pertinent facts in a streamlined format below.
Why does this matter?
By outlining the state's cyber-warfare strategies, Vault 7 effectively establishes the global standard in shadow war as it's very probable that the other highly motivated actors in this space — China, Russia, Israel, and the UK — have independently arrived at similar conclusions.
How is this different from the Snowden leak?
Edward Snowden's 2013 leak exposed the blanket surveillance tactics used by the NSA to spy on citizens, immigrants, and foreign governments. Vault 7 reveals the updated list of tools and strategies used by the CIA in response to the world becoming aware of online privacy and embracing end-to-end encryption as a measure of security.
Who leaked the data?
There are two narratives in circulation: In the first, WikiLeaks alleges that the hacking tools circulated among U.S. government hackers and contractors in an unauthorized manner and that one of the said hackers provided WikiLeaks with portions of the archive and soon plans to make a public declaration.
The second, as perpetuated by prominent cyber-security researchers like Bruce Schneier , suggests that the leak is more likely to have originated from a Shadow Broker than a whistleblower for one obvious reason: “The documents are a few years old, making this more like the Shadow Brokers than Edward Snowden. An internal leaker would leak quickly. A foreign intelligence agency — like the Russians — would use the documents while they were fresh and valuable and only expose them when the embarrassment value was greater.”
James Lewis, another cyber-expert on cyber-security at the Center for Strategic and International Studies in Washington, agrees that a foreign state — most likely Russia — stole the documents and delivered them to WikiLeaks.
Who built the tools?
The CIA hacking tools were developed by an agency subsidiary known as the Engineering Develop Group (EDG), a software development group with the Center for Cyber Intelligence (CCI) — a department belonging to the CIA's Directorate for Digital Innovation. Confused yet? Don't worry; we've provided an agency org chart, which WikiLeaks also released .
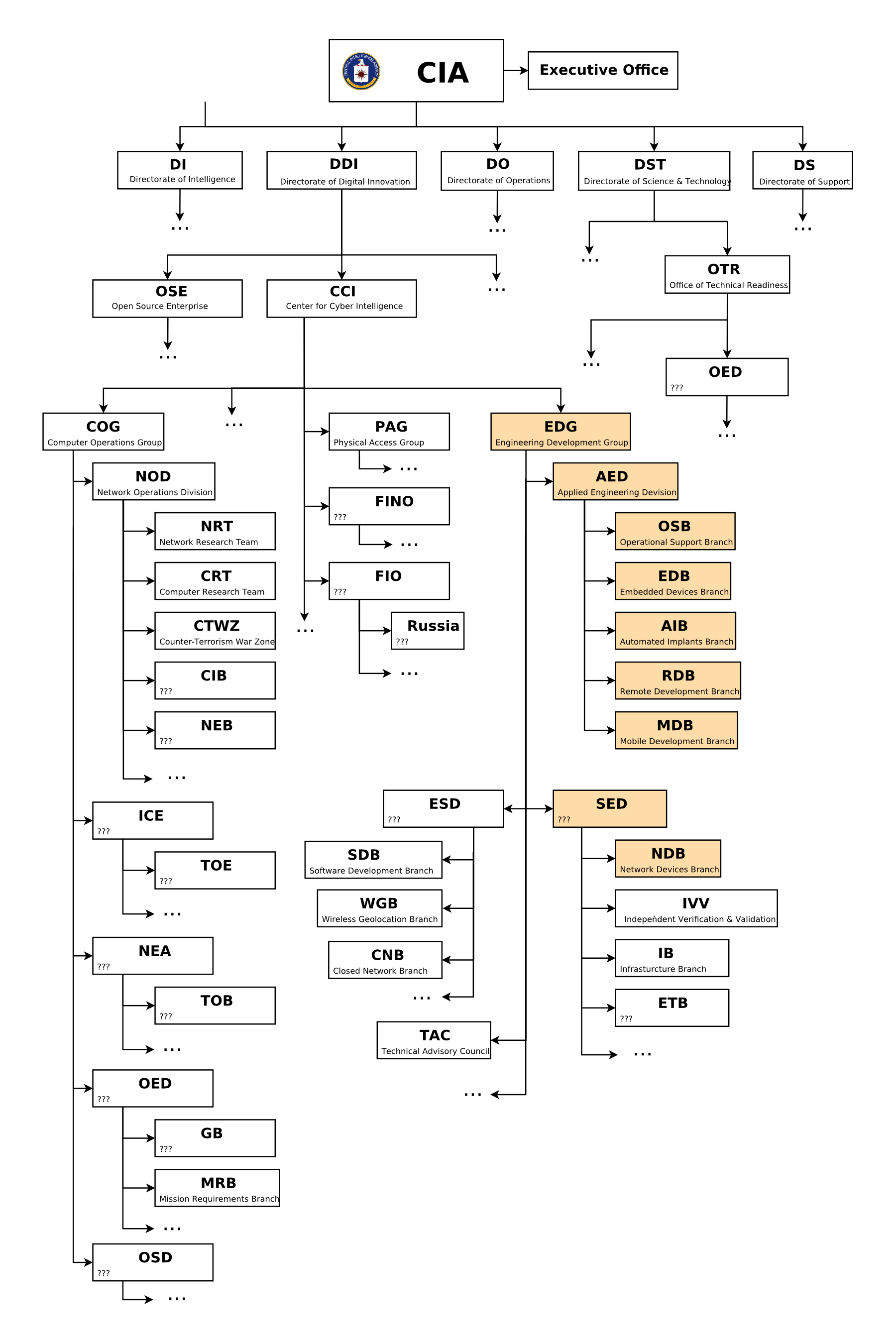
What period does Vault 7 cover?
The documents date from approximately 2013 to 2016.
What are the CIA's capabilities?
The CIA's technical arsenal can be summarized as a combination of malware that attacks Windows, MacOS, Linux, Android, and iOS end-user devices, backdoors, Trojans, zero-day exploits, and even a sophisticated virus that turns Samsung Smart TVs into covert listening devices.
1. Smartphones
According to Vault 7, the CIA possesses the ability to remotely hack and seize control of smartphones unbeknownst to the user. Compromised phones may be mined for data; instructed to send the CIA geolocation, audio, and text communications; or turned into surveillance cameras by secretly activating their microphone and camera.
Infiltration relies on zero-day exploits — security holes unknown to the vendor — acquired from GCHQ, NSA, and cyber-arms contractors. Zero-day exploits permit the CIA to circumvent end-to-end encryption in Whatsapp and Signal by extracting the data in real time before encryption takes place.
WikiLeaks reports that 24 Android zero days are named within documents, meaning that any number of the 1.15 billion Android-powered devices sold last year may be vulnerable. iPhones, which occupied only 14.5% of the global smartphone market in 2016, fared no better. Despite the brand's reputation for security, a specialized unit within the CIA's Mobile Development branch built malware that controls and extracts data from iPhones.
- So are zero-day vulnerabilities available online?
Given the gravity of the situation, WikiLeaks withheld publishing the zero-day vulnerabilities until developers can patch them. - Did the CIA share zero-day vulnerabilities with the tech sector?
In the wake of the Snowden leaks, the Obama administration consented to mounting pressure from the tech sector to share zero-day vulnerabilities and established government policy to disclose any new vulnerabilities. However, if an agency wished to maintain the secrecy of a zero-day bug to keep the channel open, it had to argue its case through the Vulnerabilities Equities Process (VEP) to an Equities Review Board under very limited circumstances.Tech capabilities cited in the “Year Zero” documents suggest that the CIA breached the commitment; otherwise, how else would the agency continue to retain the ability to breach and infest as many Android devices and iPhones? The danger in hoarding such vulnerabilities is that if the CIA could discover them, then there's a high likelihood that its rivals, or even cyber-criminals, can as well.
2. Smart TVs
Back in February 2015, a consumer reading through the privacy policy of a Samsung Smart TV spotted a strange legal clause which read: “If your spoken words include personal or other sensitive information, that information will be among the data captured and transmitted to a third party.” Experts initially assumed that the aforementioned “third party” referred to the company providing speech-to-text conversion for Samsung, although the name of the third party handling the natural language processing hadn't been disclosed.
Incidentally, the Vault 7 Leaks contain a document from June 16, 2014, referencing a program called Weeping Angel , which transforms the microphone of voice-activated smart TVs into listening devices. Implying that the CIA is the “third party” is an anecdotal fallacy at best, but a noticeable coincidence nonetheless.
3. Cars
A separate document within Vault 7, dated October 23, 2014, indicates that the CIA investigated how to infiltrate vehicle-control systems used in modern cars and trucks. The purpose is not specified, but WikiLeaks speculates that such capabilities could permit the agency to engage in nearly undetectable assassinations.
Many suspected that the car crash that ended journalist Michael Hastings's life on June 18, 2013, is consistent with car cyber-attacks. Richard A. Clarke, the former U.S. National Coordinator for Security, Infrastructure Protection, and Counter-terrorism, told the Huffington Post that “there is a reason to believe that intelligence agencies for major powers — including the United States — know how to seize control of a car remotely. So if there was a cyber-attack on Hastings's car — and I'm not saying there was — then I think that whoever did it would probably get away with it.”
The story gets stranger: Right before his death, Hastings indicated that he was “onto a big story” about the CIA and needed to “go off the radar.” On the night of his death, Hastings asked to borrow his neighbor Jordanna Thigpen's vehicle for fear of using his car, reported LA Weekly.
So are Signal and Whatsapp compromised?
Despite what some publications report, Signal and Whatsapp are not technically compromised, nor do the documents claim to have broken encryption. Quite the contrary; it would take billions of years to brute force a 256-bit AES encryption key using binary logic. But possessing a backdoor is the equivalent of looking over someone's shoulder as they type.
Other things of note?
- WikiLeaks censored names of tens of thousands of CIA targets and attack machines throughout Latin America, Europe, and the United States.
- The quantity of published pages in “Vault 7” already eclipses the total number of pages published over the first three years of the Edward Snowden NSA leaks.
- CIA's Remote Devices Branch, called the UMBRAGE group, “collects and stores an extensive library of attack techniques stolen from malware produced in other states, including the Russian Federation.” In other words, the agency uses malware.
- UMBRAGE components cover keyloggers, password collection, webcam capture, data destruction, persistence, privilege escalation, stealth, anti-virus (PSP) avoidance, and survey techniques.
- WikiLeaks writes: “With UMBRAGE and related projects, the CIA can not only increase its total number of attack types but also misdirect attribution by leaving behind the 'fingerprints' of the groups that the attack techniques were stolen from.” This means that the agency can “plant evidence” to control which nation is portrayed as the attacker.
Why should this matter to you?
It matters because the enormous data flow that each person generates is recorded and stored, allowing database owners to study human psychology on an exponential scale like never before. Because the road to hell is paved with good intentions, and those who control the data can break the art of persuasion into a science and use it to goad population segments into serving a specific interest. After all, we've already seen this happen.
Source: WikiLeaks & ProtonMail
Advertisement
Learn more about Electronic Products Magazine





