The worldwide power consumption of approximately 20 trillion kilowatts of electricity is slated to grow over 50% in the next 15 years, and Smart Grid proliferation plays a vital role in reducing the material impact on government and utility spending. Yet, connective distribution automation and smart meters are only half rolled out in the United States, according to Executive Director at Maxim Integrated, Kris Ardis. One of the primary business opportunities many may miss regarding the proliferation of the t Grid, which is an extension of the Internet of Things, lies in security.
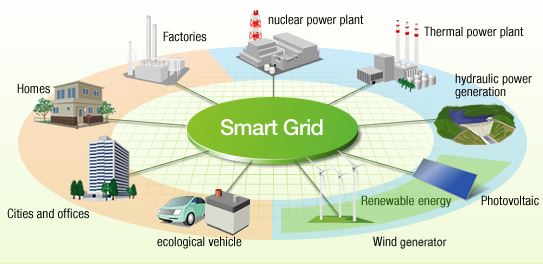
Ardis says that we are merely scratching the surface; the infrastructure needed to propagate this technology is just starting out, but once the Internet of Things infrastructure is in place, new levels of functionality will exponentially rise. Embedded sensors will grant access to never before quantified data, allowing the automation and fine tuning of tasks. For example, a smart motion sensor can work in tandem with temperature controls to determine a suitable temperature based on the number of workers present and avoid excess heating.
Challenges to design
From a Smart Grid perspective, the biggest challenge an engineer has to account in building a consumer device is how to balance cost effectiveness with the three key standards needed to create a functional Internet-of-things network; how to accurately and securely measuring and communicating data while establishing a standardized way of doing so.
Once it's been decided whether or not a particular technology is worth its return on investment, the engineer has to consider potential security risks and ways to counter them. With each additional object joining a network, you're creating extra gateways from which a malicious hacker can enter a larger network.
Security is the biggest concern
Taking into consideration that the Internet of Things permeates into the Smart Grid itself, the very infrastructure providing power is a potential target. For this reason, the biggest debate utility companies are undergoing is whether to use ZigBee, Wi-Fi, proprietary protocols, or simply an extra layer for security. Kris Ardis tells us that while there's plenty of discussion on securing the communication pipe, there isn't much talk on the security of the embedded device itself.
“If you think about two devices communicating together, a smart meter and the head end of the utility, as long as the data is encrypted you're still providing decent level of security.” But what Ardis says is not now discussed, is the other ways one can get into the device, such as through a serial port.
Companies such as Maxim Integrated are taking a slightly more robust approach by securing the entire life cycle of the embedded nodes of the Internet of Things, regardless of whether they're used in a smart meter, smart plug, or lighting control.
Maxim provides a lot of security tools for handling these potential threats, such as a random number generator to make the communication encryption none repetitive and secure booth loading. The idea behind secure booth loading is to only the chip recipient, a contracted manufacturer for example, to load their code on it and protect the code from being altered throughout its entire life cycle, thus preventing any hacking. Maxim is taking the technology and body of knowledge it has acquired from providing security in the financial sector for 20 years and applying it into their energy products.
Security applications are much easier to implement if designed in synchrony with the smart device they will inhabit. The most important consideration a system designer is to make is: what are all the possible ways my device can be entered based on its connectivity to everything else.
Story via Podcast on Power System Design
Visit Maxim Integrated for a complete solution listing
Advertisement
Learn more about Maxim Integrated





