By Warren Miller, contributing writer
Cybersecurity specialists have been using digital hacking traps called honeypots almost since the idea of internet hacking itself was born. Basically, honeypots are decoy databases intended to lure in attackers and siphon information from them while the interlopers think they’re getting the goods. Now, researchers at the Georgia Institute of Technology have developed a robot designed to act as a decoy if and when hackers try to take control of industrial robotic systems — and they call it the HoneyBot.
Small enough to fit in a shoebox and bearing a passing resemblance to the robot from the 1986 film “Short Circuit,” the HoneyBot intends to mimic certain (non-dangerous) robot behaviors in hopes of making hackers believe that they’ve gained access to networked industrial machines. While the attackers are occupied, the HoneyBot is targeting them in a fashion similar to the one employed by its non-corporeal predecessors. In large automated factory settings where industrial machines are all connected to a network, a hacker with malevolent intentions could do serious damage.
“Robots do more now than they ever have, and some companies are moving forward with not just the assembly line robots but free-standing robots that can actually drive around factory floors,” said Raheem Beyah, interim Steve W. Chaddick School Chair in Georgia Tech’s School of Electrical and Computer Engineering. “In that type of setting, you can imagine how dangerous this could be if a hacker gains access to those machines. At a minimum, they could cause harm to whatever products are being produced. If it’s a large-enough robot, it could destroy parts or the assembly line. In a worst-case scenario, it could injure or cause death to the humans in the vicinity.”
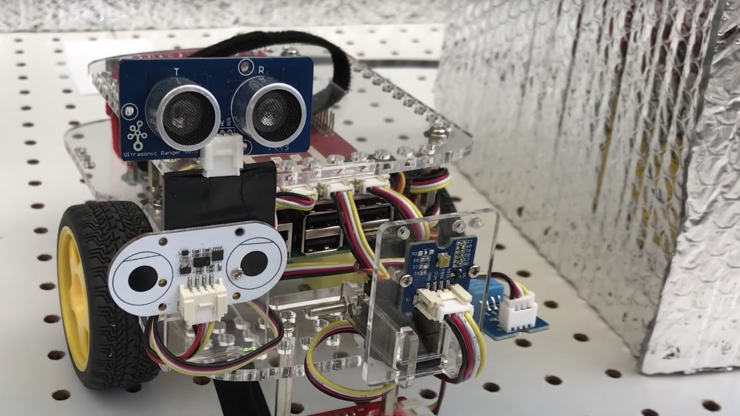
The HoneyBot is designed to defend factories against cyberthreats. Image source: Georgia Tech.
In experiments, the HoneyBot allowed volunteers to control it so long as they didn’t command it to do anything that violated a predetermined set of rules. When asked to break those taboos, the HoneyBot relayed false sensory information designed to make the user believe that it was carrying out those commands, when, in fact, it remained perfectly still. Whether the HoneyBot was actually performing the tasks or sending false information, users couldn’t tell the difference.
Perhaps virtual HoneyBots will be the next innovation. Why actually implement real robots when you could deploy virtual ones instead? Any number of virtual HoneyBots could inhabit a “make-believe” factory that could look very attractive to hackers. Would hackers be able to tell the difference between a real robot and a virtual HoneyBot? The virtual versions would cost much less and could be deployed en masse quickly and easily during a suspected attack.
While it seems like the hacking of massive corporate databases has become an everyday occurrence lately, imagine what could happen if hackers could find their way into networks of machines designed to assemble automobiles or move cargo containers. Having your social security number stolen is scary enough, but at least your life won’t be in danger if it is. The HoneyBot comes along at a time when the confluence of digital and robotic technology could result in some potentially disastrous outcomes. Maybe this bite-sized robot will be our salvation.
Advertisement
Learn more about Electronic Products Magazine








