By Alan Grau, VP of IoT/Embedded Solutions, Sectigo
Our world, our society, our homes, and our factories are all becoming more automated and connected. IoT sensor networks continue to proliferate and infiltrate every segment of our lives. Emerging technologies are driving down the cost of IoT sensors, while improved connectivity solutions are enabling use of sensors in many more remote locations than previously possible. With lower costs, better connectivity, and longer battery life, sensors and sensing systems are everywhere.
Sensors are now being utilized for monitoring crop growth, livestock health and movement, patient recovery, the movement of shipping containers, temperature in food storage and distribution systems, and a host of other applications. Use cases for these technologies include industrial sensor systems to optimize manufacturing efficiency as well as the monitoring of critical systems in which failure can cause physical damage to property and even human life.
Manufacturers of control systems for industrial systems have long been aware of the need to address safety in their designs, but the focus on security has often lagged. Without addressing security, safety can be compromised.
Developers building IoT sensor devices and networks already face a host of challenges. Which of the emerging IoT standards should they embrace? Which IoT protocols should be used? How can they distinguish their IoT and IIoT products in this competitive emerging field? How can they meet time-to-market challenges?
Between all of these challenges and a lack of clear standards for cybersecurity, building security into the device is often just an afterthought. Consequently, examples of insecure devices abound, from medical devices with hard-coded passwords to home routers with back doors. IoT sensor devices are no exception, with attacks reported on smart light bulbs that leak Wi-Fi passwords, a casino that was hacked via an internet-connected aquarium thermometer, and multiple attacks on Zigbee devices.

Smart home devices and sensing systems with embedded security can reliably resist most cyberattacks.
However, security need not be an overwhelming challenge. By including a few basic security capabilities, manufacturers can develop IoT devices with essential security protections while establishing a strong security foundation on which additional security features can be added in the future.
Vulnerabilities in embedded devices
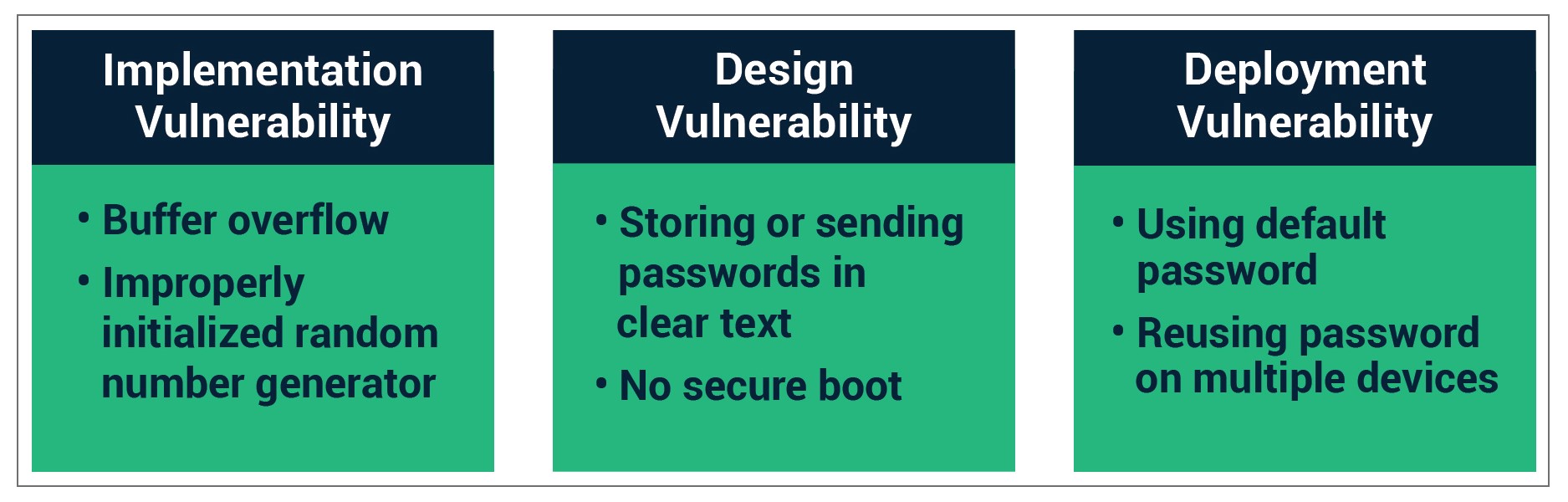
Before considering how to secure IoT sensors and devices, it is important to first consider the origin of security vulnerabilities, especially as they relate to embedded devices. Most vulnerabilities in embedded devices can be divided into one of three categories:
- Implementation
- Design
- Deployment
Implementation vulnerabilities occur when coding errors result in a weakness that can be exploited during a cyberattack. Buffer overflow attacks are a classic example of implementation vulnerabilities. Another common error is improperly seeding random-number generators, resulting in security keys that are easy to guess. Adherence to software development processes, such as the OWASP Secure Software Development Lifecycle or Microsoft’s Security Development Lifecycle, along with thorough testing processes helps to address implementation vulnerabilities.
Design vulnerabilities are weaknesses that result from a failure to include proper security measures when developing the device. Examples of design vulnerabilities include use of hard-coded passwords, control interfaces with no user authentication, and use of communication protocols that send passwords and other sensitive information in clear text. Other less-glaring examples include devices without secure boot, which allow unauthenticated remote firmware updates or that include “back doors” intended to allow remote access for debugging and maintenance of the device.
Deployment vulnerabilities pertain to issues introduced by the end user during the operation or installation of the device. These include not changing default passwords, using weak passwords, not enabling security features, and similar errors. Unfortunately, for many IoT devices, especially smart home products, it is difficult — if not impossible — for end users to implement more effective security solutions.
To address this weakness, governments are driving regulation requiring improved security. For example, California and other jurisdictions have recently enacted legislation requiring IoT devices to utilize unique passwords, an important first step to address this specific issue.
Security vulnerabilities result from implementation flaws, design flaws, or failure to properly enable and use security features.
Security considerations for IoT sensors
Security is critical for all IoT devices, and sensor devices are no exception. Sensors play a critical role in IoT solutions, collecting the data that drives the entire solution. Ensuring the integrity of IoT data is crucial.
However, building security into sensors presents a unique challenge. Cost is often paramount in designing sensor devices, and in the effort to save costs, the underlying hardware often lacks built-in security features found in higher-end platforms. Even though these devices are resource-constrained, critical security capabilities can still be included, although tradeoffs may need to be made.
For example, a sensor design may be able to support encryption, but because of limited processing power and storage, the design may support only shorter key lengths rather than higher-end platforms. The resulting encryption is easier to break using brute-force attacks. However, that “flaw” may not be critical. That is because by the time the data is decrypted, it has already been used by the IoT system and is no longer valuable.
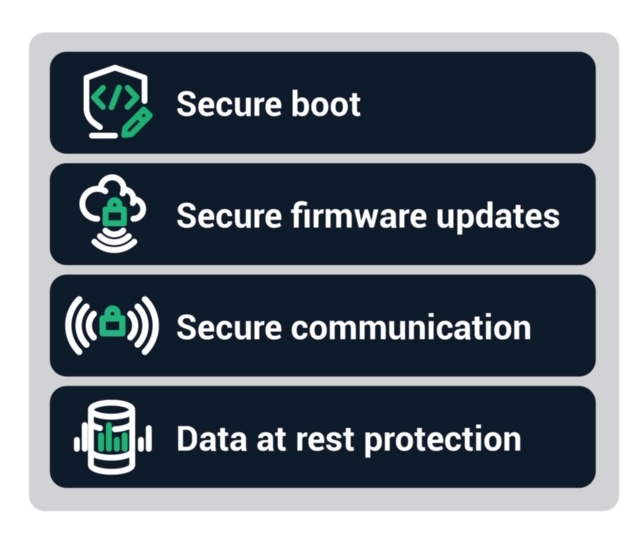
Components of a secure IoT sensing device
There are four essential components of a secure IoT sensing device: secure boot, secure firmware update, secure communication, and data protection.
Secure boot
Secure boot utilizes cryptographic code signing techniques to ensure that the device executes only code that was produced by the device OEM or other trusted party. In a device with secure boot capability, the bootloader computes a cryptographically secure hash on the firmware image prior to loading the image. This hash value is compared with a stored hash value to ensure that the image is authentic. Cryptographic signing of the stored hash value prevents malicious third parties from spoofing the software load, ensuring that only software from the OEM is allowed to execute.
Secure firmware update
Secure firmware updates ensure that device firmware can be updated, but only with firmware from the device OEM or other trusted party. Like secure boot, cryptographically secure hash validation is used to verify the firmware before it is stored on the device. In addition, machine-to-machine authentication methods can be used by the IoT device to authenticate the upgrade server before downloading the new firmware image, thereby adding another layer of protection.
Secure communication
IoT devices, by definition, will support remote communication with other devices. The communication mechanisms will vary by device but may include wireless protocols ranging from BLE and Zigbee to Wi-Fi, cellular data, and Ethernet. Regardless of the transport mechanism and communication protocol, it is important to ensure that all communication is secured. Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS) should be used when possible. For common wireless protocols, such as Zigbee or BLE, which have encryption built into the protocol but that have known encryption vulnerabilities, encrypting at the application layer provides additional protections.
Data protection
Engineers should consider encrypting any sensitive data stored on the device. Many large data breaches have resulted from data recovered from stolen or discarded equipment. Security protocols provide protection for data while it is being transmitted across networks but do not protect the data while it is stored on the device.
Four essential components of a secure IoT sensing device
Implementing security for sensor networks
Implementing security in sensor networks presents some additional unique challenges. As mentioned earlier, many IoT sensors are low-cost devices designed with just the resources required for the core device operation and do not have additional computing power to implement sophisticated cybersecurity solutions.
As these devices are often deployed “in the field,” they may also be subject to physical and proximity attacks. Hackers can physically access the device, then attempt to attack it using available communication ports. Hackers can also physically acquire (buy or steal) a similar device, take it to their labs, and then tear it down or monitor communication buses looking for vulnerabilities. With physical proximity attacks, hackers are also able to exploit vulnerabilities in short-range wireless communications protocols. There have even been reports of hackers using drones to launch proximity-based attacks.
One alternative is to bite the bullet and utilize hardware platforms capable of implementing core security services into the sensor device itself. While this will increase the cost of building the device, sacrificing security to save a few dollars is often a short-sighted tradeoff.
As another alternative, or in addition to securing the sensor devices, manufacturers and suppliers must address the security of the overall network. IoT sensors often communicate with a gateway or edge device that performs data collection or analysis. The gateway or edge device must provide high levels of security, both for itself and to provide protection for the sensors from which it collects data.
Summary
Security is a requirement for all IoT devices and should be prioritized, regardless of how small or seemingly insignificant the device or the data it captures. By adding a few basic capabilities, including secure boot, secure firmware update, secure communication, data protection, and user authentication, the security of any device can be significantly increased.
A comprehensive security analysis can identify attack vectors and prioritize security requirements. Engineers can use this information to prioritize development of security features. Only by including security in the devices themselves can we ensure that IoT-connected sensors and sensing systems will be protected from cyberattacks.
About the author
Alan Grau has 30 years of experience in telecommunications and the embedded software marketplace. He is VP of IoT/Embedded Solutions at Sectigo , the world’s largest commercial Certificate Authority and provider of purpose-built, automated PKI solutions. Alan joined Sectigo in May 2019 as part of the company’s acquisition of Icon Labs, a leading provider of security software for IoT and embedded devices, where he was CTO and co-founder, as well as the architect of Icon Labs’ award-winning Floodgate Firewall. He is a frequent industry speaker and blogger and holds multiple patents related to telecommunication and security.
Prior to founding Icon Labs, Alan worked for AT&T Bell Labs and Motorola. He has an M.S. in computer science from Northwestern University.
Advertisement








